In conversations regarding network or infrastructural security, the word “pentester” often pops up. But who really is a pentester, and what is it that they do? In simplest terms, a pentester, a contraction for penetration tester, is an individual who identifies security flaws within a network or system. They are often external consultants, authorized by a company to perform security audits on their IT ecosystem, and identify any potential cybersecurity risks. Normally, a pentester begins by conducting reconnaissance on their client’s systems, looking for any potential vulnerabilities. Then, they try to infiltrate the systems by exploiting these vulnerabilities and eventually gain access to critical data.
penetration testing
The Importance of Pentesters:
Pentesters are becoming increasingly relevant in the modern world. This is primarily because the average cost of a data breach has reached an all-time high ($3.86 million), and companies know that they can no longer take cybersecurity lightly. It seems more prudent and cost-effective to hire a consultant for thousands, than to incur millions in losses, after being compromised.
Pentesters make it easy for IT managers and technology officers to convince their bosses to approve security budgets. They can do so because we still live in a world where security isn’t considered a fundamental requirement, rather a supplementary feature. For example, let’s say a developer identified a potential security flaw in a payment gateway, which could allow an experienced hacker to obtain sensitive user data. He goes to his supervisor and makes him privy to the information. The supervisor estimates spending of $5000 to add a new authentication mechanism, which could mitigate the issue. He knows that the company’s budget is a bit tight these days, so it would be hard to convince his boss to approve the budget, without concrete proof. So, he hires a pentester instead and asks him to perform the scheduled security audit of the system. The pentester finds the vulnerability and gets his hands on the credit card data of all the company’s users. The supervisor goes to the boss and takes the pentester’s report with him; he now has a sales pitch up his sleeve, that the boss can’t possibly say no to.
What Kind of Vulnerabilities does a Pentester look for?
There can be many different kinds of vulnerabilities within a system; including missing data encryption, OS command injection, SQL injection, missing authentication, missing authorization, reliance on untrusted inputs, buffer and stack overflows, etc. Depending on the level of freedom that the company gives to the pentester, the type and number of scanned and exploited vulnerabilities can differ. If there are no limits imposed by the client, a pentester has the liberty to go to any lengths; from performing a social engineering attack, to using a Wi-Fi sniffer, to making a denial-of-service attack.
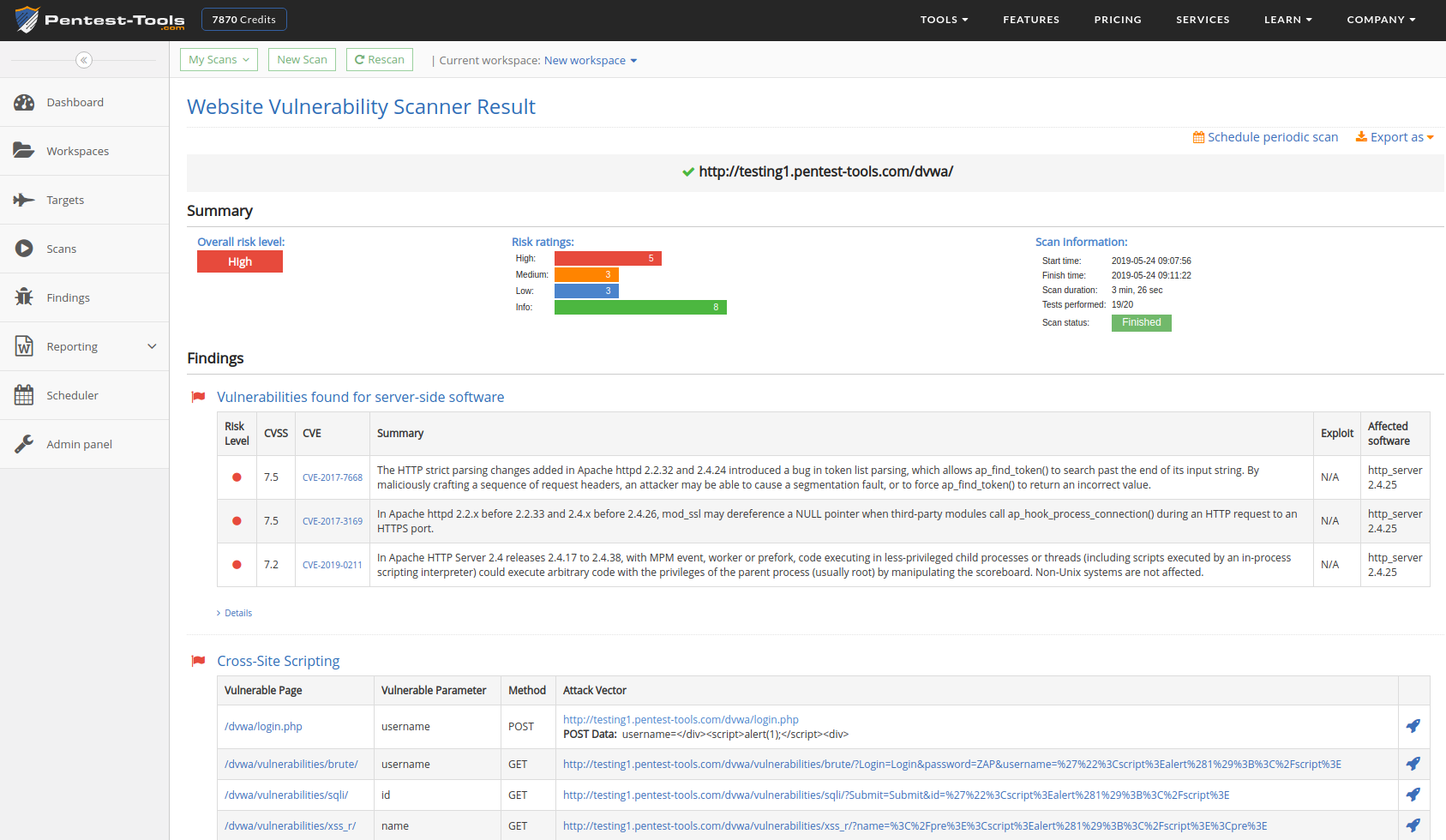
However, generally, pentesters have to work within some limits or boundaries set by the client. Directives from clients can range from “Can you try to gain access to our administration portal?” to “Can you please try to get inside our data center network? You are free to use any resources that could be available to a potential hacker” For the former, the pentester would normally just use any website penetration tools, and won’t be able to utilize their social engineering skills. For the latter, however, they will be free to send phishing emails to employees, meet them at bars, and even try to sneak a USB into the actual data center.
Types of Penetration Testing:
There are three main types of penetration testing: Black box testing, white box testing, and grey-box testing. Which one you should choose typically depends on the extent of information you are willing to share with the pentester. Let’s take a look at all three in more detail:
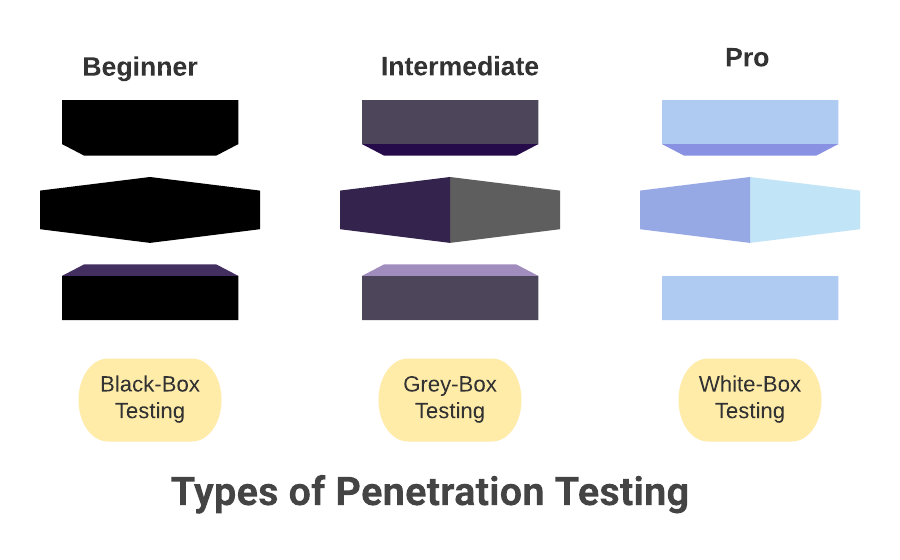
In black-box penetrating testing, the pentester is given no knowledge about the network or the system that they are supposed to test. They basically have to work with a black box. This type of pentesting is relevant when the company wants to simulate an attack made by an outsider.
Conversely, in white box penetration testing, the company shares all the information regarding its infrastructure with the pentester. This includes IP addresses of database servers, OS specifications, source code, and even login credentials, etc. This might seem counter-intuitive, but since the whole purpose of this type is to simulate attacks made by an insider, it makes sense.
Lastly, grey box penetration testing is followed by a company providing partial knowledge of the network and system to the tester. This type of testing simulates attacks made by a hacker who somehow got access to some internal network/software specification documents.
Stages of Penetration Testing:
There are four main stages of any penetration testing effort:
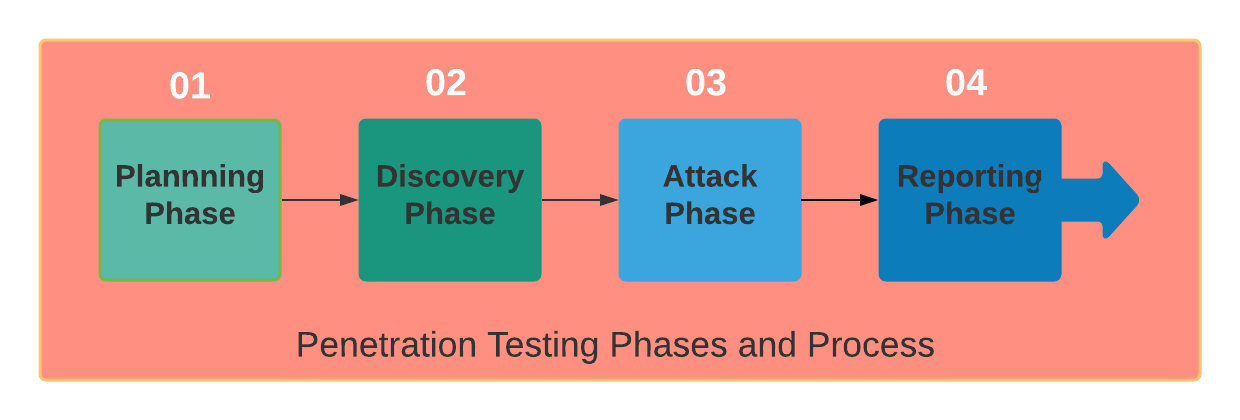
- Planning: Scope and strategy of the project is decided and documented.
- Discovery: At this stage, the pentester scans the system rigorously and repeatedly to find any useful information, like usernames, passwords, encryption keys, etc. This process is also known as fingerprinting. These days, a lot of fingerprinting tools are used for this purpose, e.g. BlindElephant and Wappalyzer. In addition to this, the pentester also identifies any potential vulnerabilities during this stage.
- Attack: The pentester simulates a bunch of relevant attacks on the system during this stage.
- Reporting: Finally, audit reports are compiled, documenting security flaws and suggestions that can help revamp system security.
How to Become a Pentester
Becoming a pentester takes the general path of learning exploits and way around things. But the ones who make a career out of it takes the same route bit confidently. Automated tools and knowing a few scripts don’t make one an expert. There are certain levels of entity and prerequisites. A pentester has to go through different ideologies.
Web App Security Pentesting: As most of our software and applications became versatile and can be accessed via a browser, becoming an expert in web app security can be a great start. We may think companies on the internet are secure. Let me tell you, they are not. Nothing is 100% secure. We are not influencing to crackdown sites and services but giving hope that it is possible to gain the skillset.
XSS, CSRF, SQLi, WAPT on online services is a hefty way to learn. But to scope out one should learn XML/JSON injection, XXE, RCE, SSRF, LFI, RFL. There is no limit on how much one can learn. WireShark, Metasploit are a few interesting tools to learn.
When does one know that enough information is gained? Never! But to have languages like JavaScript, Ruby, Java, Scala, PHP, AJAX, WAPT in respiratory gives a wider range of understanding. Pentesting on service doesn’t come in a hot platter. If one has enough skills, it is easy to find a loophole and this is where the fun begins. Alongside, a pentester needs to learn OAuth and SSO.
Network Security Pentesting: A network security specialist or pentester has the task to figure out network access and weakness even if it is secure. Companies and industrial networks constantly need to figure out loopholes and ways to fix them. Carrying out a network pen-testing is a bit different from web app pentesting, as the pentester needs to listen to a spoofed network protocol and act accordingly.
To get started in the network and communication protocol, TCP/IP, VoIP, LDAP, SMB is the preferred way to get started. Alongside active directory, firewall, IDS, Antivirus crackdown, Sysmon and a good understanding of the operating systems e.g. Windows, Linux or other Unix-based, is required. The terminal commands help a ton by minimizing steps. Of course, the journey to becoming a pentester will introduce newer and efficient ways to learn and practice.
Script Scrambling for Pentesting: Getting hands-on a script or code, a pentester should be able to read it like a book and find the errors like grammatical mistakes. As a beginner, it’s not going to work like that. So, we need practice. Reviewing codes in C, C++, JavaScript, Python, and other languages should become an instinct regarding the target platform.
Before building something, one must learn how to take it apart. And this is why basic coding skills come in handy. Someone with one or two language fluency can jump on others pretty easily as syntax and functions work quite the same. Problem-solving in StackOverflow or GitHub is a good way to learn and improve self-dictionary.
A good programmer can reverse engineer any given code or at least have an idea of where to start. Once a pentester or hacker breaks down the code, they can modify it, take pieces out, and place some too. To engage in specific vulnerability or 0days coding, a pentester may learn about memory allocation, binary format, etc.
Physical/Hardware Pentesting: Sometimes pen testing requires taking a physical device apart and trying to scope out ways to pentest. Electronic devices have many architectures (like ARM) and a pentester should be familiar with its work methodology. Also, SPI, FPGA, UART, JTAG are great tools to tweak. Architecture like x64 and x86, flash memory alongside connected scripts help understand embedded or hardware devices pen-testing.

There are a lot more than this, depending on where your career lands. Having a college degree in Computer Science, Security, or Information Technology will help in front of employers who are willing to teach a few things in the intern period. Open learning from various sources will give the best result nonetheless. Learning Nix-based OS, network protocol, Nmap, scanning, and listening will also give adequate experience towards being a pentester. Of course, we are not trying to scare future pentesters, but happily informing there is scope to learn a lot in this highly rewarding sector.
Overall training, practice, and experience is the way to go to become a pentester.
Pitfalls of Penetration Testing:
No good thing comes without its pitfalls, and penetration testing is no different:
- Even though a pentester will try their best, some security flaws might remain undetected. There is no guarantee that your system will be completely impervious to potential attacks after the audit.
- Penetration tests take time, and since they are carried out on the core system/network, chances are that your business activities will get disrupted.
- Penetration testing is a labor and time-intensive task, so high costs can be associated with it.
Final Word:
An experienced pentester can help a company in identifying vulnerabilities that can otherwise cause a lot of reputational and financial damage. Regardless of whether you want to simulate an insider attack, or one made by an experienced external hacker, a pentester can do the job for you!

Leave a Reply