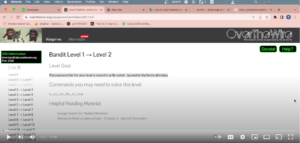
Automate Your Own CTF Solution
Learn how to code your own solution to CTF (Capture The Flag) exercises. After you manually solve a part of

Learn how to code your own solution to CTF (Capture The Flag) exercises. After you manually solve a part of
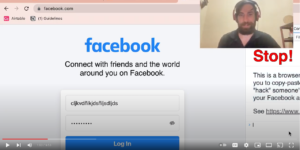
Learn how to create your own social media keylogger and by extension how to defend yourself from this kind of

What are zero-click compromises? How can hackers get my credentials through a file share? Do these questions come into your

The previous article was all about how to perform Kerberoasting. This blog will cover one of the interesting attacks. The