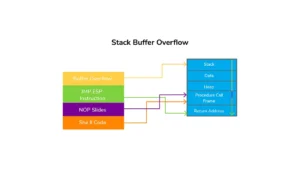
Buffer Overflow Steps (Part 2)
This is the follow-up article to the previous one in which we did Spiking and Fuzzing. In this article, we

This is the follow-up article to the previous one in which we did Spiking and Fuzzing. In this article, we

Buffer Overflow Attack is one that most beginners find challenging to understand and perform. This is because it involves a
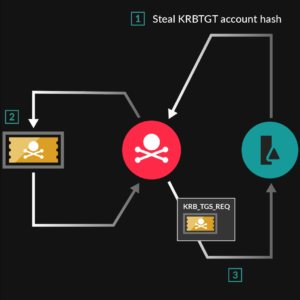
The previous article was about how can we dump the credentials using the super amazing open-source and free tool Mimikatz.

So far, we have been discussing the attacks on Active Directory. The attackers are always looking for some loophole to