Buffer Overflow Attack is one that most beginners find challenging to understand and perform. This is because it involves a combination of programming, computer architecture, memory, and software security concepts. So, by exploiting this, an attacker can gain unauthorized access to the systems. It is one of the known vulnerabilities and was common a few years ago but still, we can find it in various applications.
This BOF article series is inspired by the PEH course by TCM.
Buffer
Before diving into the attack itself, it is important to understand the terms. A buffer is a memory storage region that temporarily holds the data for several purposes. Buffers are commonly used in the following contexts:
- Input/Output operations
- Inter-Process Communication
- Memory Management
- Performance Optimization
Also, the buffers can be implemented in various forms including:
- Arrays
- Queues
- Linked Lists
Consider the following code in C language
#include<stdio.h>
void main(){
char name[5];
}The above code will declare a memory of 5 bytes and assign it to a buffer

Overflow
Each buffer has a size that determines how much data it can hold. Overflow, as the term suggests, occurs when the data to write is larger than the storage capacity. As a result, the buffer can store the data up to its maximum capacity, and the remaining data overflows.
Buffer Overflow
Buffer Overflow is a software vulnerability that occurs when the software writing data to the buffer overflows the buffer’s capacity. When a program tries to write more data into a fixed-size buffer than its capacity, an overflow occurs resulting in the remaining data overwriting adjacent memory areas. This happens when the program does not validate the input data size with the buffer’s capacity.
Buffer Overflows are commonly found in programs written in languages like C and C++. The manual memory management and lack of built-in safety features in these languages make them prone to buffer overflows. However, this vulnerability can exist in other languages as well depending upon the implementation of input validation and memory management.
Buffer Overflow Attack
Buffer Overflow Attack involves binary exploitation as our primary goal is to subvert the binary’s execution in a way that benefits us. These are the most common type of binary exploitation, but other types of binary exploitation exist, such as Format String exploitation and Heap Exploitation.
In this article, we will be focusing on Stack Based Buffer Overflow. We need to understand the stack and its structure.
- Stack is a LIFO data structure meaning the data pushed, in the end, will pop out at first and vice versa
- The stack contains a bunch of memory registers among which EIP, EBP, and ESP are of our interest
- EBP (Extended Base Pointer) is a stack pointer that points to the base of the stack
- ESP (Extended Stack Pointer) is a stack pointer that points to the top of the stack
- EIP (Extended Instruction Pointer) contains the address of the next instruction to be executed
- Stack’s buffer space is filled from higher memory to lower memory (top to bottom)
- All variables are accessed relative to EBP
- Every function in the program has its own stack
See the below image for a better understanding
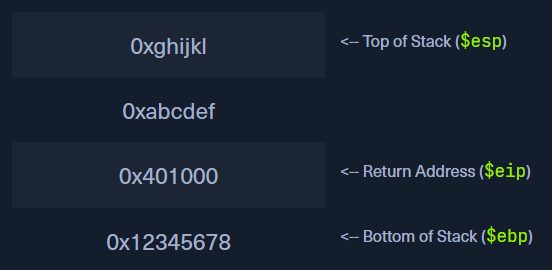
Attack Vector
We can provide input for filling up in the stack, but keeping in mind the constraint of buffer space. Let’s assume the buffer space is only 8 bytes. What if we provide an input that exceeds the 8 bytes limit? If the input validation is not implemented, the buffer space will be filled with 8 bytes and the remaining data will be overwritten to the next buffer space as below
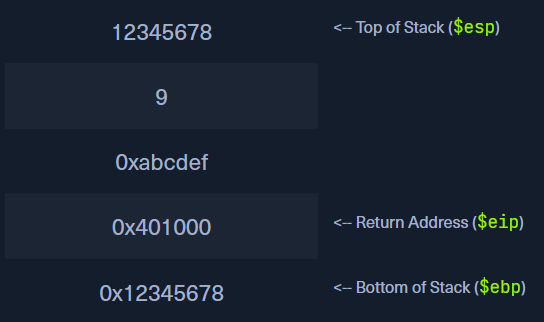
As you can see that upon providing the input “123456789”, the characters from 1-8 (8 bytes) get the space but the extra character (1 byte) overwrites the existing previous value. Now imagine, if we could provide the input long enough to overwrite the whole stack and eventually change the value of the EIP register. This could lead an attacker to control the next instruction to execute in the program.
As an example, if we provide the input “EvilCommJUNKDATAJUNKDATAJUNKDATAValOfESP”, then we can overwrite EIP value and let the program run our Evil Command as below
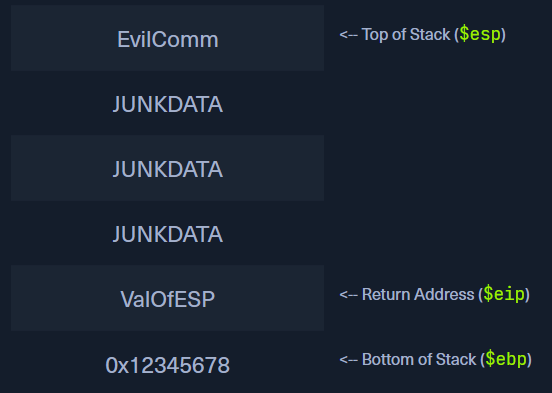
This can lead an attacker to have unauthorized access to either the application or in the best case (for an attacker) access to the whole system.
Login Exploit Theory
Upon every function call, a new stack is created and the old EIP gets pushed to the top of that function’s stack. This is to tell where to return upon the completion of function execution. If we craft our input we can make it overwrite the EIP value. This would lead the program to return to the address of our choice. This way, we can subvert the program’s execution.
Now, imagine a program that asks you for credentials before giving you sensitive information. If the program is vulnerable to the Buffer Overflow Attack, we can find the address of the function that displays the sensitive information. So we can craft our payload that would overwrite the address in EIP and give us access even upon an unsuccessful login attempt.
Steps For Buffer Overflow
Following are the essential steps to perform a Buffer Overflow Attack and we will discuss them in detail in upcoming articles
- Spiking
- Fuzzing
- Finding the Offset
- Overwriting the EIP
- Finding Bad Characters
- Finding the Right Module
- Generating Shellcode
Requirements
Before starting, we need to set up our lab and install the necessary tools. So, you need to have a Kali Machine (Attacker) and a Windows Machine (Victim). It can either be a Virtual Machine or you can use your own Windows host machine. Also, on the victim Windows machine, you need to install
- Vulnerable Server that we will be attacking
- Download and unzip the file
- Immunity Debugger to run the program through the program debugger showing memory changes at runtime
- Fill in any fake data and download it
- Python2.7 for the debugger. The
Immunity Debuggerinstaller will detect and ask you to install Python2.7 along with the debugger
Resources
Following are some of the good resources that can help you better understand the in-depth concepts

Leave a Reply