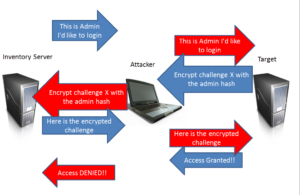
SMB Relay Attack
The previous article was about LLMNR Poisoning and how can we dump NTLMv2 hashes and later on crack them. Not

The previous article was about LLMNR Poisoning and how can we dump NTLMv2 hashes and later on crack them. Not
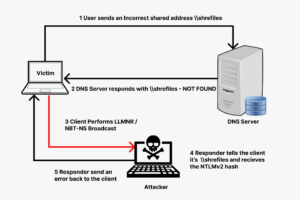
In the previous article about active directory lab setup, we set up the lab environment to perform attacks. This article
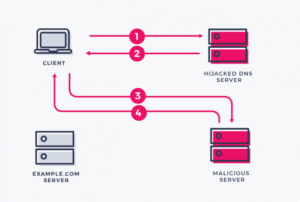
Previously, we did a full demonstration of an SMB Relay Attack. And how it is possible to exploit SMB by
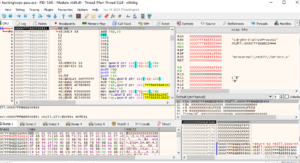
We often confront with software applications that are either password protected or require certain conditions to proceed. One way to