In the initial attack vectors, we were able to compromise a user (Frank Castle). All this by gaining its hash through LLMNR Poisoning and then cracking the hash to get a plaintext password. Also using SMB Relay Attack to gain access to the machine along with dumping the SAM file hashes. Not only this but going through an IPv6 attack using mitm6 and ntlmrelayx, taking over DNS and capturing almost all information about the domain. Now, what can we do once we have a compromise? How can we enumerate the network using these compromises? In this article, we will talk about Post-Compromise AD Enumeration. For that, we will be using 2 tools
- PowerView
- BloodHound
PowerView
PowerView is a PowerShell tool to gain network situational awareness on Windows domains. It contains a set of pure-PowerShell replacements for various windows net * commands, which utilize PowerShell AD hooks and underlying Win32 API functions to perform useful Windows domain functionality. It basically helps us enumerate Domain Controllers, Policies, Users, Groups, and much more.
Installing PowerView
First, we need to get PowerView. We have access to one account (Frank Castle). Also, through SMB Relay Attack, we can get an interactive shell on that machine. Taking advantage of these, we can run PowerView from the windows machine. So, for easier demonstration, I will go through the Windows machine instead of running commands from the shell.
So, go to the windows machine and download PowerView from GitHub
In case of dropping it through the shell, an attacker can download the script to their host and then transfer it through the shell. I am running it directly on the machine because it will allow me to auto-tab completion to make things smoother.
Running PowerView
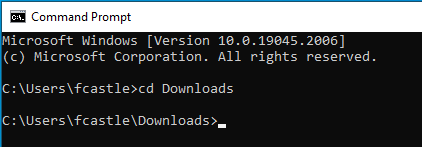
Go to the windows machine at which you have downloaded PowerView, open the command prompt, and change the directory to Downloads.
Since this is a PowerShell script, we need to run it from PowerShell. But before running, we need to change the execution policy.
Execution Policy
An execution policy is part of the PowerShell security strategy. Execution policies determine whether you can load configuration files, such as your PowerShell profile, or run scripts. And, whether scripts must be digitally signed before they are run.
So, for running the script, we need to bypass the execution policy. For this, run either one of the following commands in the command prompt
powershell -ep bypass
OR
powershell -ExecutionPolicy bypass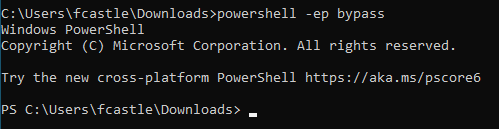
Loading PowerView
Now that we have set up everything, we can load the script using the following command
. .\PowerView.ps1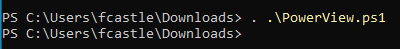
AD Enumeration using PowerView
The script is loaded, so we can perform AD Enumeration through its commands.
Of course, there are multiple things one can perform using this tool but we will be going through only some of them.
AD Enumeration Domain Info
- To get information about the domain, run the following command
Get-NetDomain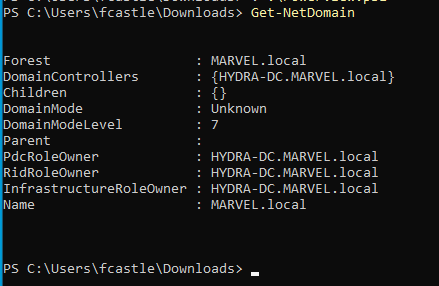
It will give information about the domain.
- To get information about the Domain Controllers, run the following command
Get-NetDomainController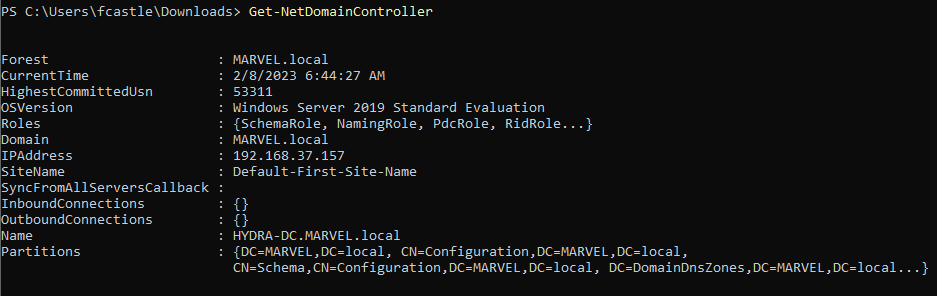
It will not only list what domain controllers are available but also its name, IP, OS, and other information. This can be further useful in targeting domain controllers specifically.
- To get the domain policy, use the following command
Get-DomainPolicy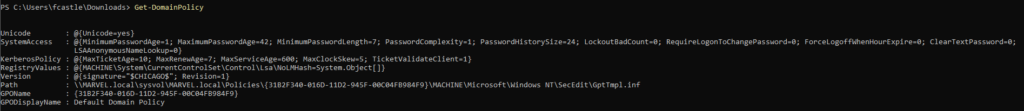
- To view the specific policy, use the following command
(Get-DomainPolicy)."POLICY_NAME"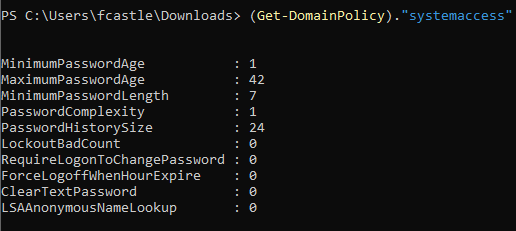
Checking the system access policy tells that the minimum length of the password is 7. This can be useful while doing brute forcing and so on.
AD Enumeration User Info
- To get information on all users, we can use following
Get-NetUser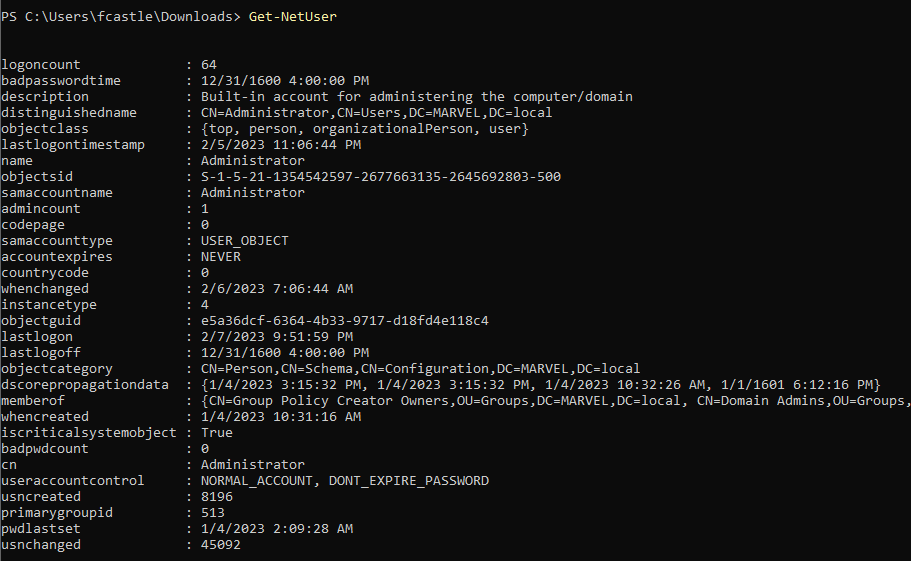
This command gives a lot of input depending on the number of users.
To come around this dirty output and query only the fields of choice, it is useful to know what are user properties.
Get-UserProperties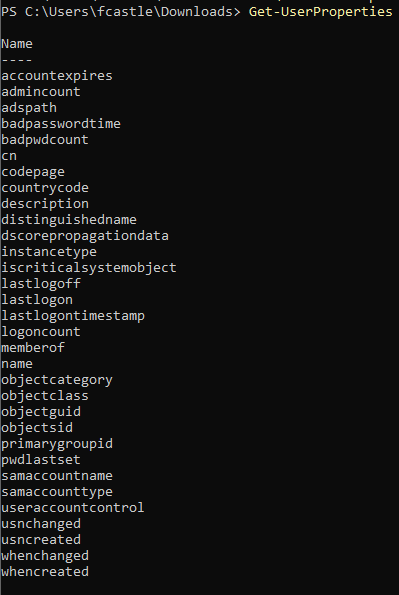
So, we can use the select command which is the same as grep in Linux to query specific property.
Get-NetUser | select cnThis command will show only the user names as below
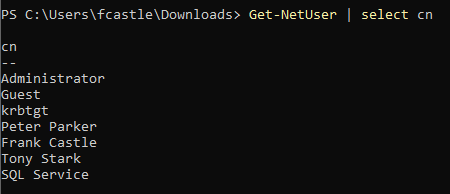
- To view users and the time of the last password set, we can use the following
Get-UserProperties -Properties pwdlastset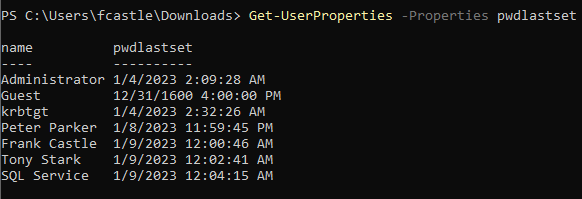
This can be useful in determining the possibility of what accounts are new or old.
- To view bad password attempts to highlight the possibility of an account being attacked
Get-UserProperties -Properties badpwdcount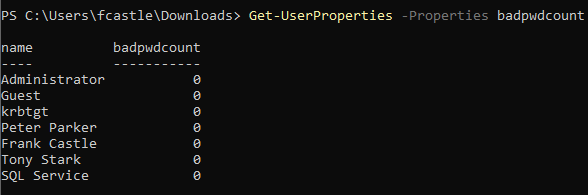
AD Enumeration Computer Info
- To get information about the all computers
Get-NetComputer -FullData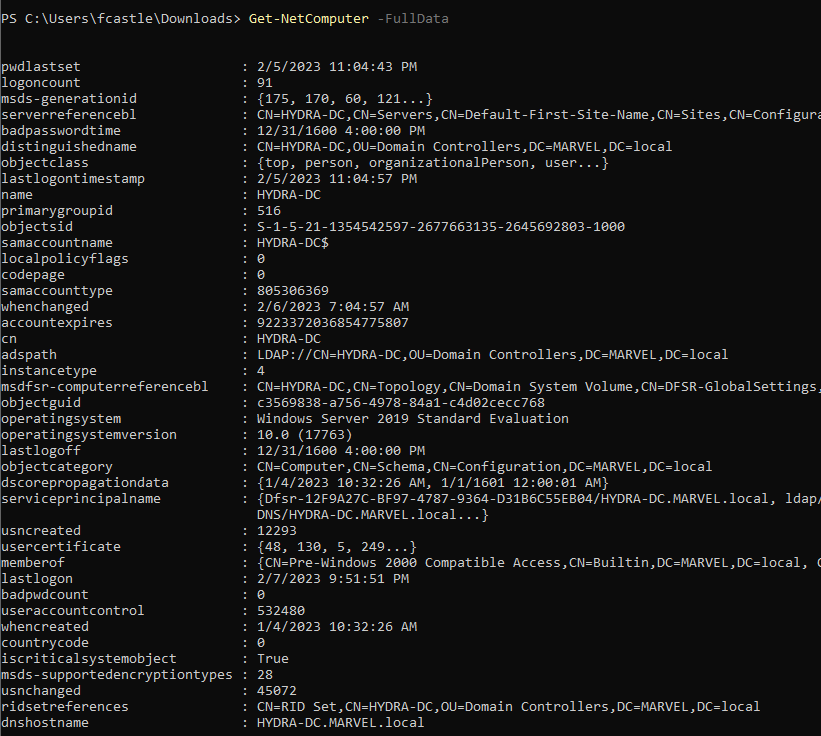
AD Enumeration Group Info
- In order to find the groups, we can use the following command
Get-NetGroup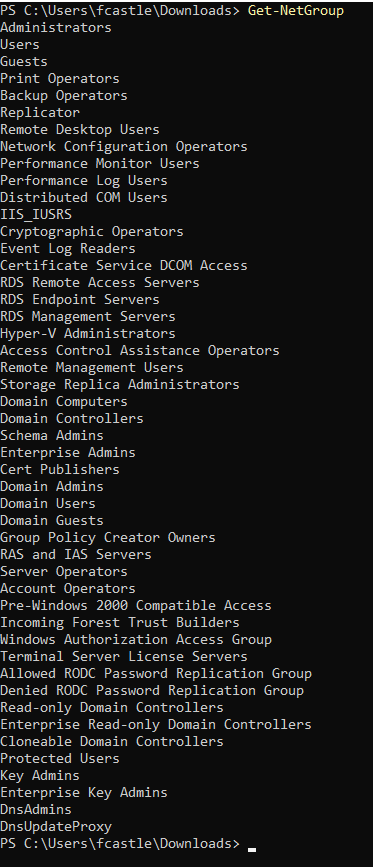
To further get admin groups, we can use a wildcard for admin in the command
Get-NetGroup -GroupName *admin*To get the members of a specific group, we can use the following command
Get-NetGroupMember -GroupName "Domain Admin"AD Enumeration File Share
There is a module for finding the file shares in the network
Invoke-FileShare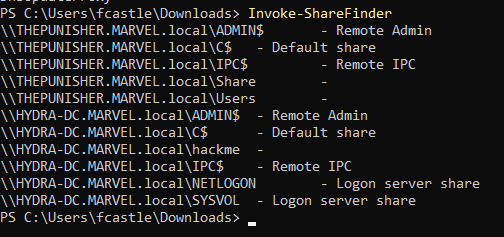
This lists what shares are being shared and where. For example, from the above image, some shares are shared on the local machine while some are shared on the domain.
AD Enumeration Group Policy
- To view the Group Policies, we can use the following command
Get-NetGPO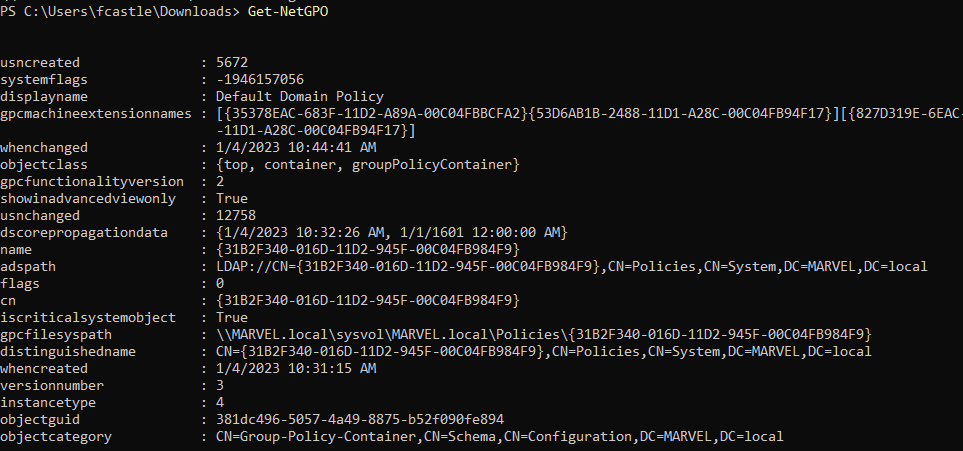
In order to view only specified fields, we can simply use select. For example, to list only the policy name and when it was changed, we can use the following command
Get-NetGPO | select displayname, whenchangedThis can be helpful in determining when was a policy changed and then thinking about the next attack vector.
Not the END
There is much more that can be gathered through this tool. I have shown the common surface gathering but you can dig deeper and find what you can find. In the real AD environment, there will be much more and complex things to get information about.
Enumeration is the Key
Since this is an enumeration, we are gathering every possible data about the AD environment to get a better understanding. Then use the information gathered to prioritize the users, computers, groups, or services we want to attack. The purpose is to enumerate most of what we can get so as to use it in the actual attacking phase and lateral movement.
Resources
Following are some of the useful resources for the PowerView
- https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993
- https://book.hacktricks.xyz/windows-hardening/basic-powershell-for-pentesters/powerview
- https://powersploit.readthedocs.io/en/latest/Recon/
- https://nored0x.github.io/red-teaming/active-directory-domain-enumeration-part-1/