Autopsy Kali Linux – Demo of The Best Digital Forensic
To acquire a forensically sound copy or disk image, we need appropriate media to analyze the files. To rule out

To acquire a forensically sound copy or disk image, we need appropriate media to analyze the files. To rule out
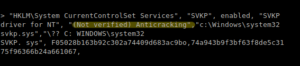
Malware is any software that is created with the intent of causing harm to a device, server, client, or an

Almost every organization with an IT setup is vulnerable to Cyber-attacks. There is a general rule of thumb regarding managing

The entire internet infrastructure is based on different sets of rules called protocols. These protocols determine internet communication and activities,