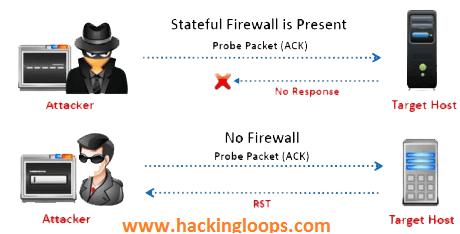
The ACK scanning method is used to determine whether the host is protected by some kind of filtering system. In ACK scanning method, the attacker sends an ACK probe packet with a random sequence number where no response means that the port is filtered (a stateful inspection firewall is present in this case); if an RST response comes back, this means the port is closed.
Now, let’s go through this code:
from scapy.all import *
ip1 = IP(src=”192.168.0.10″, dst =”192.168.0.11″)
sy1 = TCP(sport =1024, dport=137, flags=”A”, seq=12345)
packet = ip1/sy1
p =sr1(packet)
p.show()
In the preceding code, the flag has been set to ACK, and the destination port is 137.
Now, check the output:
root@Lokesh|Lucky:/scapy# python ack.py
WARNING: No route found for IPv6 destination :: (no default route?)
Begin emission:
..Finished to send 1 packets.
^Z
[30] Stopped python ack.py
The packet has been sent but no response was received. You do not need to worry as we have our Python sniffer to detect the response. So run the sniffer. There is no need to run it in promiscuous mode and send the ACK packet again:
Out-put of sniffer
——–Ethernet Frame——–
desination mac 000c294f8e35
Source mac 000c292e847a
———–IP——————
TTL : 128
Source IP 192.168.0.11
Destination IP 192.168.0.10
———TCP———-
Source Port 137
Destination port 1024
Flag 04
The return packet shows flag 04, which means RST. It means that the port is not filtered.
Let’s set up a firewall and check the response of the ACK packet again. Now that the firewall is set, let’s send the packet again. The output will be as follows:
root@Lokesh|Lucky:/scapy# python ack.py
WARNING: No route found for IPv6 destination :: (no default route?)
Begin emission:
.Finished to send 1 packets.
The output of the sniffer shows nothing, which means that the firewall is present.
That’s all for today friends. If you like our tutorial and wish to support us, then you can show your gratitude by visiting any of our sponsors or ads.

Leave a Reply