Credentials Stealing
Ever wondered how your credentials can be stolen from SSO (Single Sign-On)? How a legit-looking windows popup can steal the credentials? Phishing has been around for many years. Attackers have been using many techniques to lure the victims into their trap and gather their credentials. These techniques include social engineering, fake emails, campaigns, messages, websites, etc. There have been many detection mechanisms to protect users from common and/or suspected phishing attempts. But a new technique called Browser In The Browser (BITB) Attack has taken over the internet with its unique and impressive attack vector.
The old way of phishing
Attackers have been creating similar-looking websites and hosting them over the internet. They then social engineer the victims to visit that website and upon interacting with the website and putting the credentials, attackers would have gotten the secrets. But the problem with this approach is that any person with some technical knowledge can see that the URL of the website is not the same as the real website which might put the user in suspicion.
But what if the user is presented with the website with the same URL and same look, how come are they gonna tell whether they are being tricked or not.
Browser In The Browser (BITB) Attack works around the same principle to minimize the suspicion ratio and show the fake website window as a legit one.
Discovery
Browser In The Browser (BITB) Attack discovered by a security researcher mr.d0x. He has published it on his website
Single Sign-On (SSO)
Many websites now allow users to signup with Google, Facebook, Apple, and some other popular social logins through their SSO because it is easier than having users fill in all the details. BITB takes advantage of these third parties’ Single Sign-On (SSO) option.
Power of Javascript
Thanks to Javascript, it gives the developers the power to do anything. From submitting the forms, adding/deleting elements to/from the DOM, showing popups to displaying separate windows with any content. BITB Attack uses the same features to lure victims into believing the fake browser window is the real one. Attackers can pop out a new window with the URL of the legit website and even with the SSL-protected padlock displayed.
Proof of Concept (POC)
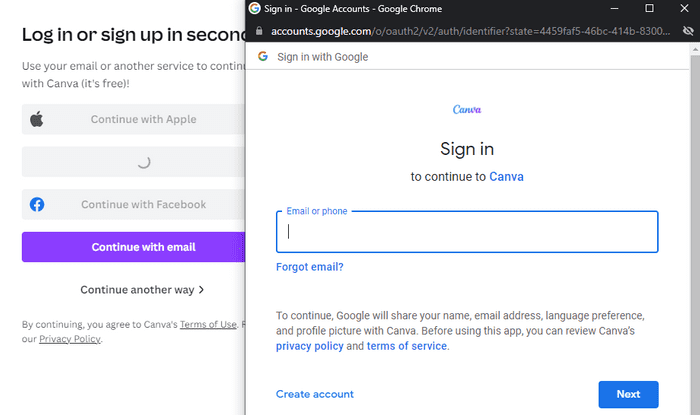
The above image from mr.d0x’s POC shows Gmail’s login form. The popup window from Google is requesting authentication and asking for the credentials. But an attacker can create the similar one by just writing some HTML and CSS. Then Javascript can be used to popup the window and make the user believe it is real.
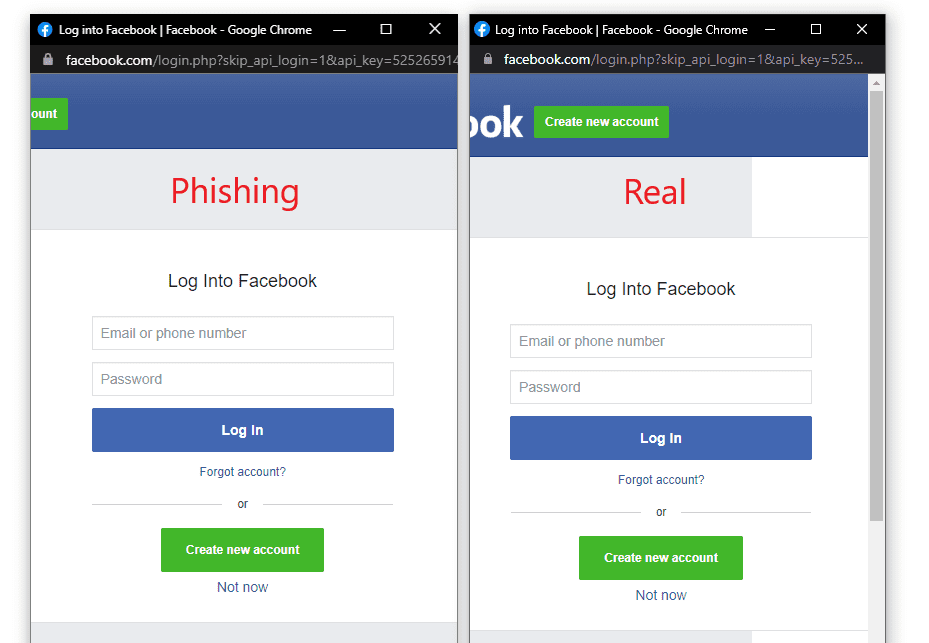
The popup on the left side is a fake one. Anyone entering the credentials will be sending their credentials to the attacker rather than to Facebook’s server. But it’s nearly impossible to differentiate between both real and fake one.
Working of Browser In The Browser (BITB) Attack
The attacker will create a website of something that users find interesting and want to explore further. But for that, users have to signup on to the website and make an account.
You can think of the website as the same as Pinterest where users can see the pictures. But once you scroll down a specific limit, it asks you to either signup or login to the website.
The attacker makes users Sign-On using only Google, Microsoft, or Apple. One of the popular cyber security learning platforms PenterterAcademy allows users to signup/login to their website attackdefense.com only via Google as shown below
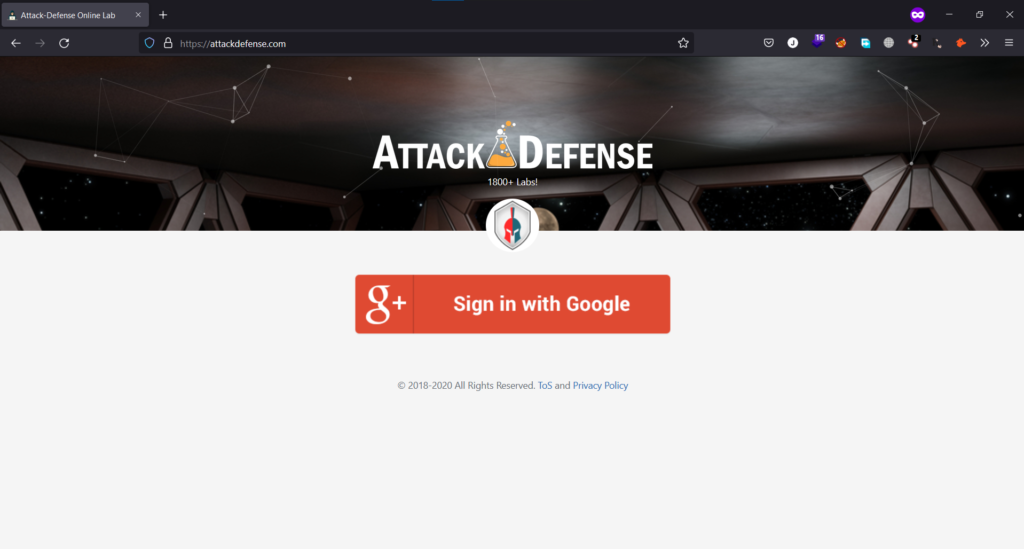
Users will have no choice but to log in to the website with SSO. Javascript code used to trick the user into believing the button is linking to the real URL is as below
<a href="https://gmail.com" onclick="return launchWindow();">Google</a>
function launchWindow(){
// Launch the fake authentication window
return false; // This will make sure the href attribute is ignored
}The above code will show https://gmail.com upon hovering over the link but upon clicking, launchWindow function will be called which will ignore the href attribute and popup a fake phishing window that will resemble the same look like the real one but will have the attacker’s server route in the action of form submission.
As soon the fake window will be popped-up, the user will see that as a real one and put in the credentials, and submit it. The attacker will receive the credentials at their server. The user will see nothing happening and might think that website is not fully functional at the moment.
Detection
Till now, no detection mechanism rolled out to protect the users from this attack. But users can manually check for it by dragging the popped-out window beyond the host window limits. If the new window can go out of the host window boundaries, then it is a real one. But if the window is getting stuck at the boundary, then it is a fake one.
Limitations
The user has to visit the attacker-controlled website in order to get a fake SSO window to pop up.
BITB Templates
You can get Browser In The Browser (BITB) Attack templates from this Github repo by none other that mr.d0x.

Leave a Reply