
Today we are going to take a closer look at the vulnerabilities in the WEP (Wired Equivalent Privacy) protocol and see how to exploit those vulnerabilities and how hackers can gain access to a Wi-Fi network they don’t already have access to. We will be using the aircrack-ng software to facilitate the attack from a Kali Linux installation, but I wanted to point out a few caveats, warnings, and explanations before we dig into the demonstration.
First of all, you should note that some of the attack process is similar to cracking the WPA and WPA2 Wi-Fi protocols. However, WEP is a different protocol altogether, so past starting the software on a wireless interface and performing the dumps, the process is a little different. In addition, you should note that we are not going to be taking advantage of a handshaking and reconnection flaw and performing a dictionary-based attack as we did with WPA. Instead, we are going to monitor wireless data and capture packets to deduce the key based on some well-known vulnerabilities.
WEP Vulnerabilities vs WPA Vulnerabilities
Before we begin the WEP cracking demonstration, you should have a general understanding of the protocol, its vulnerabilities, and how they differ from WPA and WPA2. First off, you should understand that WEP is a security protocol that uses RC4 security which is a type of stream cipher. The cipher uses a short key to generate a ‘random’ key stream, but this technology has been exploited for years.
There are several ways that WEP vulnerabilities can be exploited. One way that it is commonly attacked is by comparing two streams that used cipher-texts with identical key streams. By using an XOR operation (Exclusive Or) on the data, the protocol can be reverse engineered.
One of the fatal flaws in the protocol revolve around the CRC-32 checksum that is used to ensure that data hasn’t been changed in transit – otherwise known as an integrity check. By changing the bits and editing the checksum to a valid permutation, it is possible to fool the RC4 stream data into appearing valid. However, this is just the tip of the iceberg regarding WEP vulnerabilities, and you should know that these security flaws give rise to both passive and active attacks.
Conversely, WPA suffers from a security vulnerability related to TKIP (Temporal Key Integrity Protocol). These flaws make WPA and WPA2 vulnerable to packet spoofing, decryption, and brute force attacks. While the underlying mechanics of WEP and WPA are very different, you’ll find that you can crack either protocol in a matter of minutes (usually) by using the aircrack-ng software on Kali.
One of the key differences between our attacks is how we attack the protocol. In the WPA and WPA2 tutorial, we used a dictionary of passwords to find the key. This time, however, we are going to be intercepting wireless packets out of the air with aircrack-ng (though there are many other types of packet sniffers) to discover the key data.
Attack Types
Passive attacks are facilitated by a wiretapping technique that allows an attacker to intercept wireless communications until they spot an ICV collision. Then, the attacker can use software to deduce the contents of the data. Because of the flaws in the RC4 algorithm, an attacker can relatively easily gather data and cross-check that data to decrypt messages and even gain network access.
Conversely, and active attack can be used when an attacker already knows the plaintext data for an encrypted message. Then, the attacker can manually craft additional encrypted packets to fool the WEP device. Because they know how to manipulate the hashing algorithm, they can fool the integrity checks, causing the WEP device to erroneously accept the packets as valid data. This is a type of injection attack, and they are surprisingly easy to carry out.
Getting Started
Before you begin, you are going to need several things to build an environment where you can begin hacking. As always, you should know that you don’t have the legal right to misuse this information in public to attack real-life networks, so you should only attempt this exploit in the privacy of your home network. You are going to need the following five items before we can begin:
- A computer system running Kali Linux
- A wireless router using WEP that you own and control
- The aircrack-ng software
- A wireless interface that can be run in monitor mode to collect packets
- Another wireless host connected to the router
Step 1
Make sure your wireless card is seen in your Kali Linux system. You can run the ifconfig command to look for wireless interfaces. You should see an Ethernet and loopback interface, but we are interested in the interface that starts with a ‘w.’ Likely, the wireless interface you want to use will be wlan0 unless you have multiple wireless cards.
Step 2
Next, we are going to use aircrack-ng to put your wireless interface into monitor mode, which will allow it to monitor and capture wireless frames from other devices to facilitate the attack. You will need to run the following command:
- aircrack-ng start wlan0
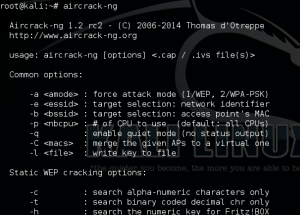 Note that you may have a wireless interface with a different name. If your interface’s name is wlan1 or it has a different name, append it to the end of the command. Make special note of the output, because it will create a listening interface, likely named mon0.
Note that you may have a wireless interface with a different name. If your interface’s name is wlan1 or it has a different name, append it to the end of the command. Make special note of the output, because it will create a listening interface, likely named mon0.
Step 3
Then we will start using the dump command to grab packets from other wireless devices, and the software will be able to make calculations and comparisons among the data to break the insecure WEP protocol. Enter the following command:
- airodump-ng mon0
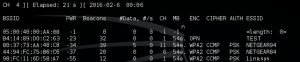
Step 4
Now it is time to tell your wireless interface to start storing captured wireless data based on the network of your choosing. Remember to plug in three key pieces of information from the previous output into the following command:
- airodump-ng –w [ESSID] –c [Channel] –bssid [BSSID] mon0
More specifically, you will need to plug in the ESSID, the channel number (CH), and the BSSID. By now your wireless interface should be capturing wireless frames, but you are going to need to store them in a local file. You will want to have at least 10,000 packets before you move on to the remaining steps. Use the following command to write your data to a file on your hard drive:
- airodump-ng mon0 –[file-name]
Step 5
Last but not least, you are going to need to do the most important step of the process by actually using the captured data from the WEP device. Issue the following command:
- aircrack-ng [file-name].cap
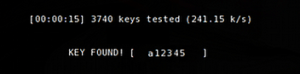
If all goes according to plan, you should be able to break the WEP system. However, if the command fails, you will want to wait until your wireless card captures more data. Give it time to capture 15,000 packets and then try again.
Caveats and Differences from WPA
You’ll probably note that the attack procedure has fewer steps than the WPA/WPA2 attack procedure. While it may seem simpler on the surface, you should know that the WEP attack process revolves around capturing data transmitted by other wireless hosts. If there is only one host connected to the network or hosts aren’t sending much data, it will take longer to gather enough data for the attack to work. On the other hand, the WPA/WPA2 attack centered around using a dictionary of passwords after forcing a host to reconnect.
Final Thoughts
It is a simple matter to break WEP encryption provided you have the right tools, but be warned. You shouldn’t ever abuse this knowledge. Doing so could lead to severe consequences that negatively impact your life. Make sure that you only attempt these attacks on devices that you own, and make sure that you never use WEP to secure your wireless access points and routers.

Leave a Reply