
Buffer Overflow Steps Spiking & Fuzzing
In this article, we will understand and perform Spiking and Fuzzing in detail. Before proceeding, disable Defender’s Real Time Protection

In this article, we will understand and perform Spiking and Fuzzing in detail. Before proceeding, disable Defender’s Real Time Protection
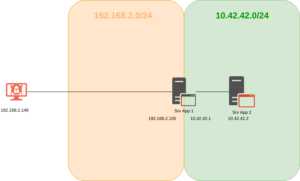
The most important task for an attacker, after gaining access to a target system or infrastructure, is maintaining access. And

In the initial attack vectors, we were able to compromise a user (Frank Castle). All this by gaining its hash
Most people believe that their browsing history is private. However, trackers on websites have clever ways of uncloaking other sites