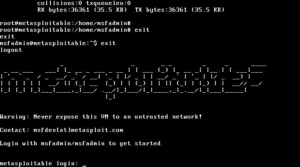
Metasploitable 2 – The Most Interesting Vulnerabilities
The Rapid7 Metasploit community has developed a machine with a range of vulnerabilities. Metasploitable 2 VM is an ideal virtual

The Rapid7 Metasploit community has developed a machine with a range of vulnerabilities. Metasploitable 2 VM is an ideal virtual

Kevgir VM: CTF Challenge In this article we are going to deal with the walkthrough of Kevgir VM which is

SQL Injection is the most commonly found vulnerability in web applications according to Open Web Application Security Project (OWASP). Moreover,

In conversations regarding network or infrastructural security, the word “pentester” often pops up. But who really is a pentester, and