Urbit is a peer-to-peer computing platform that reimagines the idea of an operating system from the ground up. Hacking Urbit apps is also very, very fun. I want to show you why Urbit is a really interesting hacker playground by just picking an Urbit app and finding a bug in it. Just be careful, once you fall into this rabbithole you won’t want to climb back out into the normal old internet.
Let’s go!
What even is Urbit?
Simply, it’s a virtual machine that can communicate directly with other Urbit VM’s with full end-to-end encryption. It accomplishes this with a bunch of mindblowing ideas that you can read about in the Urbit docs. The best way to learn about Urbit is to just go to https://tlon.io/ and get started for free with your very own planet. But if you want a general intro to the idea, you can watch this: https://www.youtube.com/watch?v=M04AKTCDavc.
It’s decentralized nature, and the unique design decisions of the Urbit OS, make it fun to work on and play with. But Urbit is more than tech. It’s an aesthetic (the “calm computing vibe” typified by images such as those below), and most preciously, a community.

Lest anyone accuse me of cherry-picking, we’ll just start with a fresh planet hosted by Tlon and hack one of the default apps.
Hacking Urbit’s most popular app
If you use Tlon, this is what you’ll see when logging into your Urbit.

Picking at random, let’s run the Groups app, which looks like this.
We can also create our own Group. So, this is the app we have to hack. Or just, mess around with and find any bug. So let’s think – we’re not on the internet anymore. Or rather, we’re in something else, which happens, currently to live in the internet. Like a tick in bear’s fur. We’re in a bear, but we aren’t a bear. Anyway, let’s think – how does this app work, compared to a conventional chat app like WhatsApp?
Well, when you chat in a group on WhatsApp, all of the users send their messages, not to each other, but to WhatsApp. When you read messages, you ask WhatsApp for the messages. When an admin performs a moderation task, she is really just asking WhatsApp to perform the task for her. If we were hacking WhatsApp groups, we would aim at the infrastructure around WhatsApp’s servers.
But on Urbit, everyone is a server, so no one is the server. In other words – where do Groups store there messages, if there is no central server that hosts them?
We’ll have to break out of our usual drone-like hunt for the same old XSS bugs and see how Urbit’s computational and networking model creates new kinds of security problems.
Hacking Urbit means hacking differently
Groups could solve this by hosting each user’s messages on their own Urbit. This would suck, because if someone’s Urbit went offline, their messages would disappear from groups they’re in. Also, users could modify their message history arbitrarily (although there are ways to prevent this, which I’ll discuss later).
The better solution is to host the chat history in the Urbit of whoever owns the group. This would mean that group owners can modify whatever data they want within the group, and this is the data users would see when they use a chat. Let’s just try posting a message to a group we own, but changing it so it appears to be have been posted by someone else. In other words, let’s see if group owners can forge messages in the groups they own.
First, I’ll post a message and intercept it with Burp.
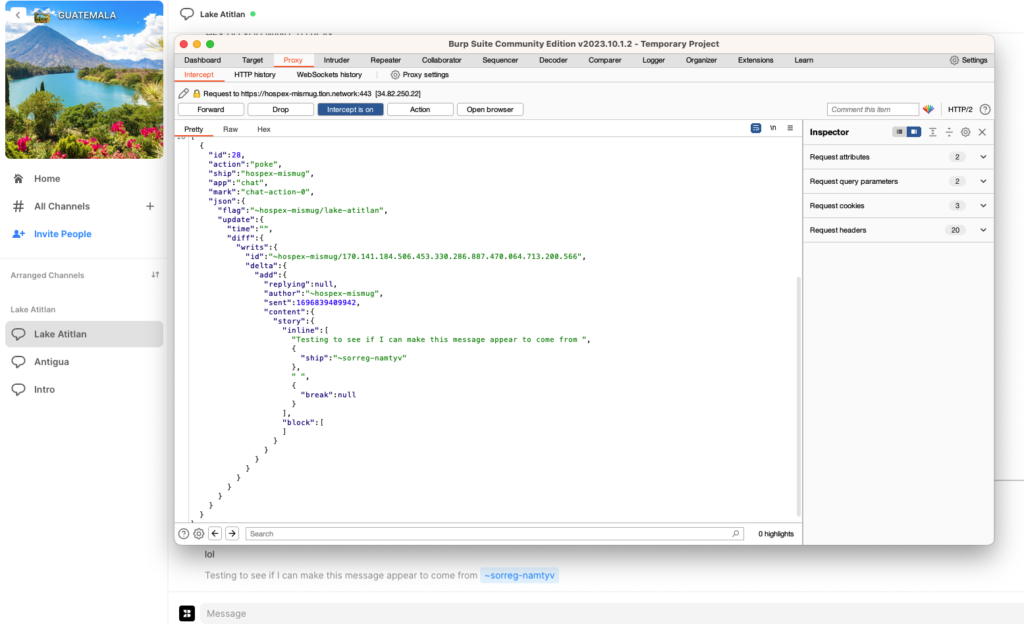
The text is really small, so I’ll copy the JSON below:
[
{
"id":23,
"action":"poke",
"ship":"hospex-mismug",
"app":"chat",
"mark":"chat-action-0",
"json":{
"flag":"~hospex-mismug/lake-atitlan",
"update":{
"time":"",
"diff":{
"writs":{
"id":"~hospex-mismug/170.141.184.506.453.334.390.088.988.100.297.314.271",
"delta":{
"add":{
"replying":null,
"author":"~hospex-mismug",
"sent":1696839632377,
"content":{
"story":{
"inline":[
"Testing to see if I can make this message appear to come from ",
{
"ship":"~sorreg-namtyv"
},
" ",
{
"break":null
}
],
"block":[
]
}
}
}
}
}
}
}
}
}
]What happens if I just change the other to another user? Let’s try ~sorreg-namtyv, the founder of Urbit.
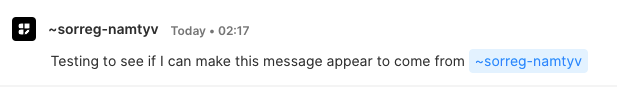
Wow, there’s our first Urbit vulnerability! Admins can forge messages from any Urbit ID. Tsk, tsk. Now that we’ve had our first success hacking Urbit…
How to fix it?
Cryptography is weaponized mathematics. In this case, the devs can arm users with cryptography to prevent admins from impersonating people in groups. The solution is simply to send messages with a signature, signed by your Urbit’s private key.
The public key is available for lookup in Azimuth (the Urbit Public Key Infrastructure) even if a particular Urbit is offline. So when you see the messages in a group, your chat client would simply verify the signature of each message in the background. Forged messages could still appear, albeit with some kind of warning.
I’d love to submit a patch for this myself. Sadly, my skills as an Urbit app dev are severely lacking. Maybe one day! If you enjoy casual bug hunting, Urbit apps are a goldmine of bugs at every level. There’s something for everyone. The community isn’t huge so even beginners can contribute a lot.
It’s like a completely different evolutionary timeline of computing. You get to feel the sense of wonder and novelty and uncertainty you felt when you first opened a command line.

Leave a Reply