A Firewall is a security solution that inspects incoming and outgoing traffic based on some certain security rules and we plan to show you three ways to bypass these modern day firewalls. It blocks or allows a connection based on these rules, these rules are in form of tables called Access Control List (ACL). Organizations use firewalls for security and to block certain types of websites and connection from the organization. They use DNS, IP, Port and content filtration to block incoming and outgoing traffic from an organization’s network. Here we’ll show you exactly how to evade and bypass the firewalls restrictions.
DNS filtration
Domain Name Resolution (DNS) works like a telephone directory, it is used to resolve Domain Name into IP addresses. This type of filtration is offered by firewalls and some general security solutions like OpenDNS (https://www.opendns.com/), So when a user requests for a website that is restricted, it refuses to resolve the Domain Name into IP Address. This is how it looks:
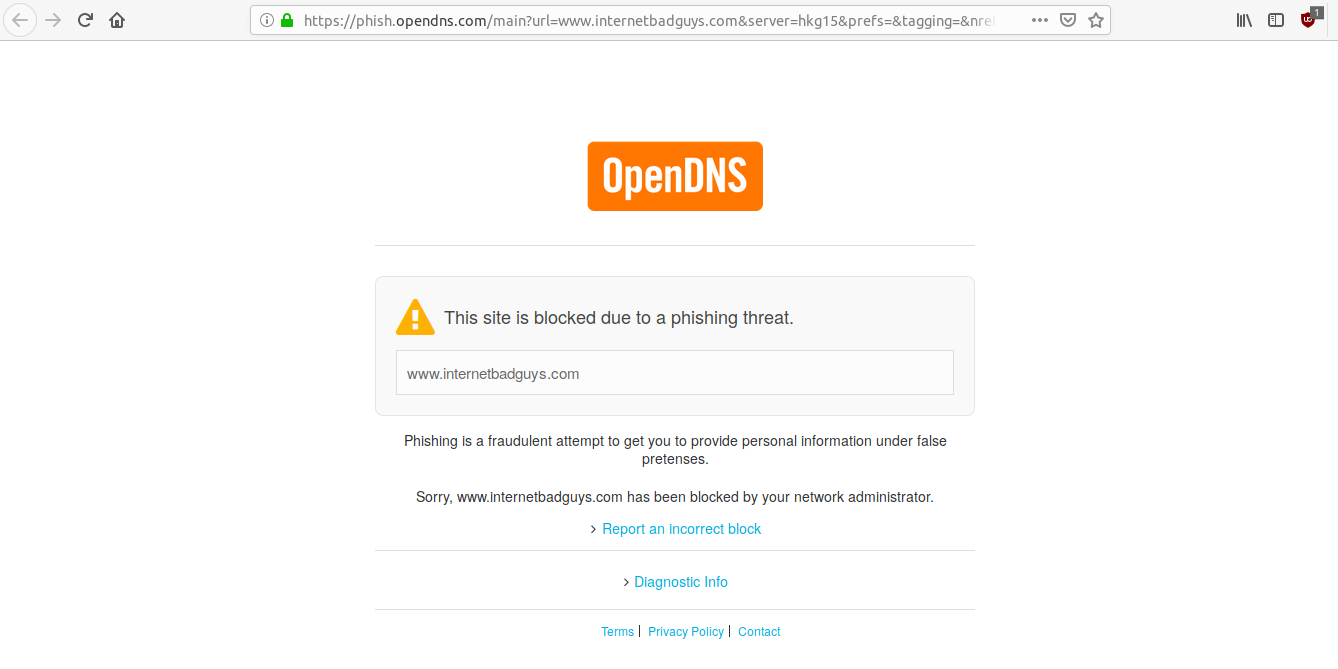
This type of filtration can be evaded by changing your DNS Server or entering the restricted website’s IP address in your browser. For example, facebook.com is blocked within your organization so you need to first find its IP Address. To find the IP Address of this restricted site, go to www.hcidata.info
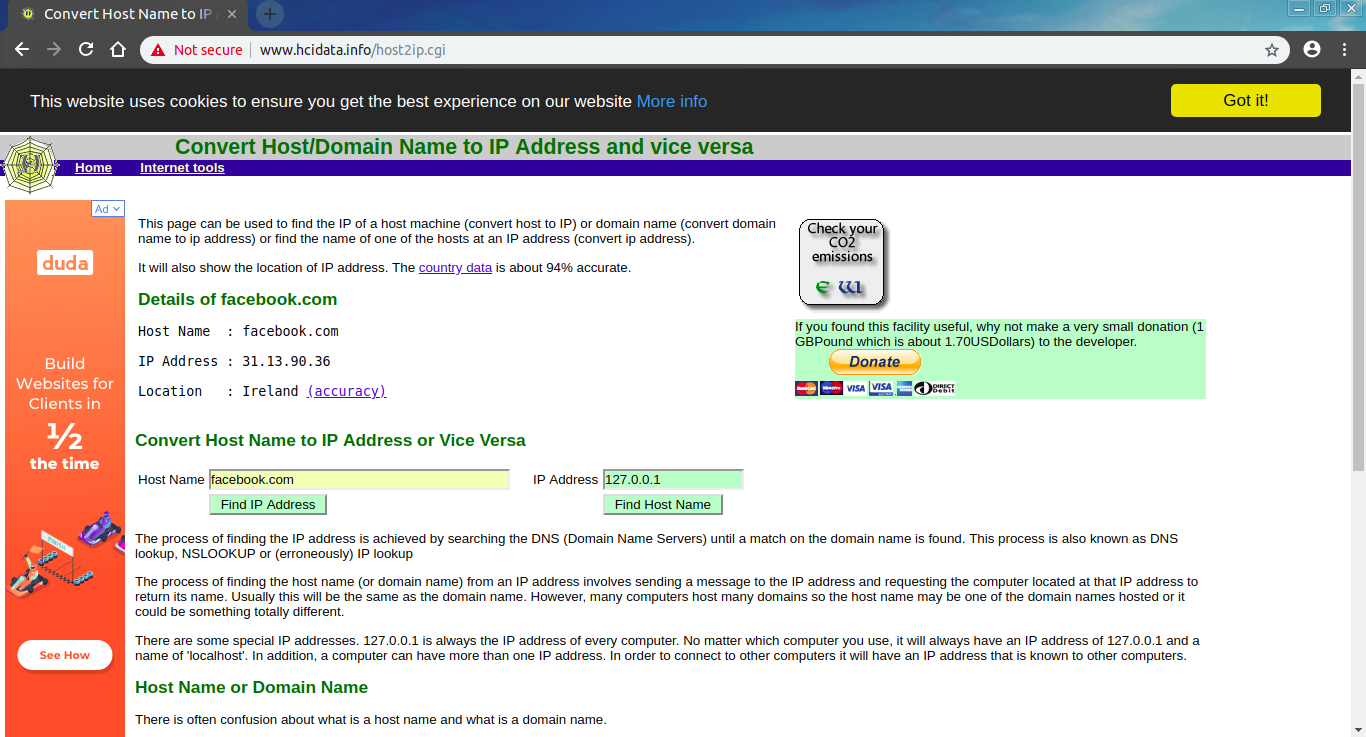
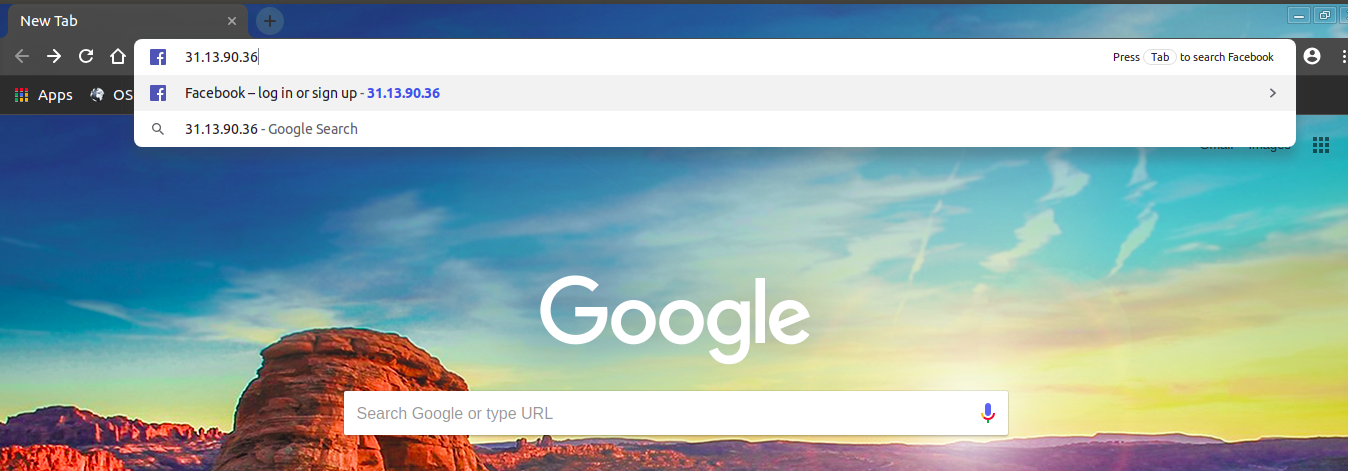
Now enter this IP Address into your browser and browse the site with no restrictions.
Changing your DNS Settings
You can evade DNS filtration by changing DNS settings of your network. In Linux go to your Network Setting > IPv4 setting, and change your DNS Server to 8.8.8.8 or 1.1.1.1 .
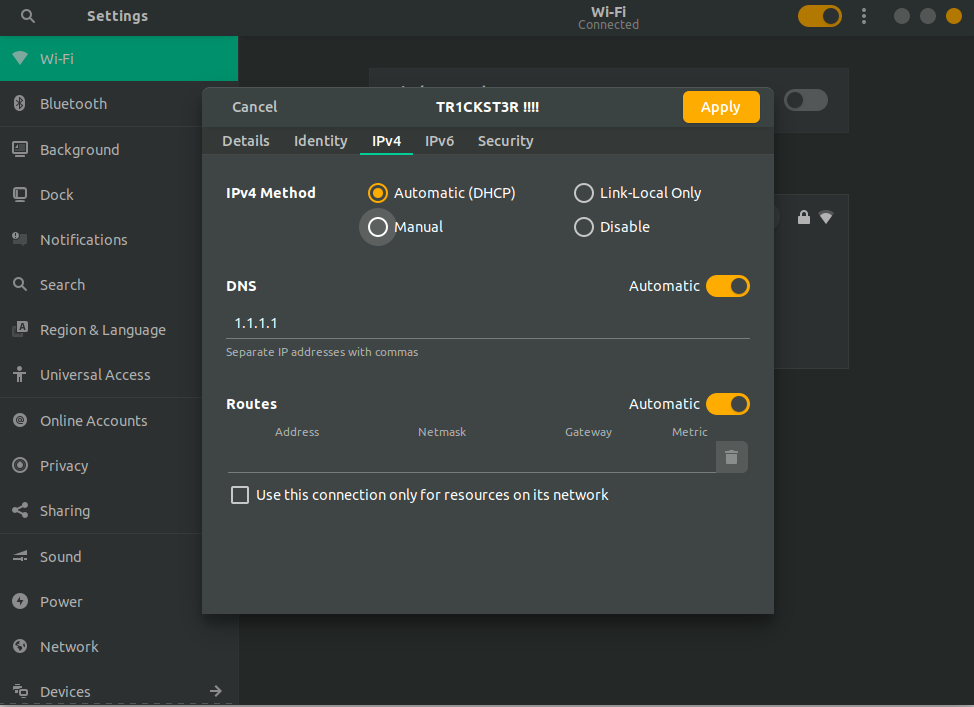
In Windows, go to Network and sharing Center then Click on your connection and go to Advanced
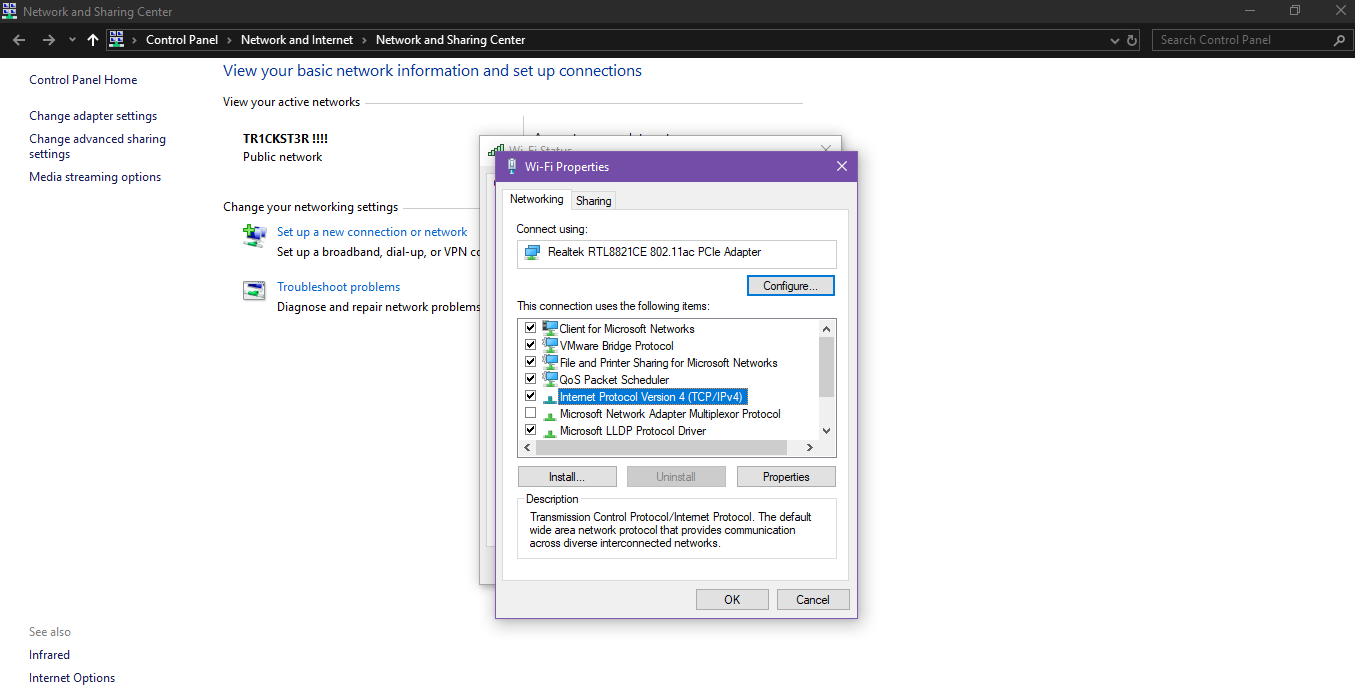
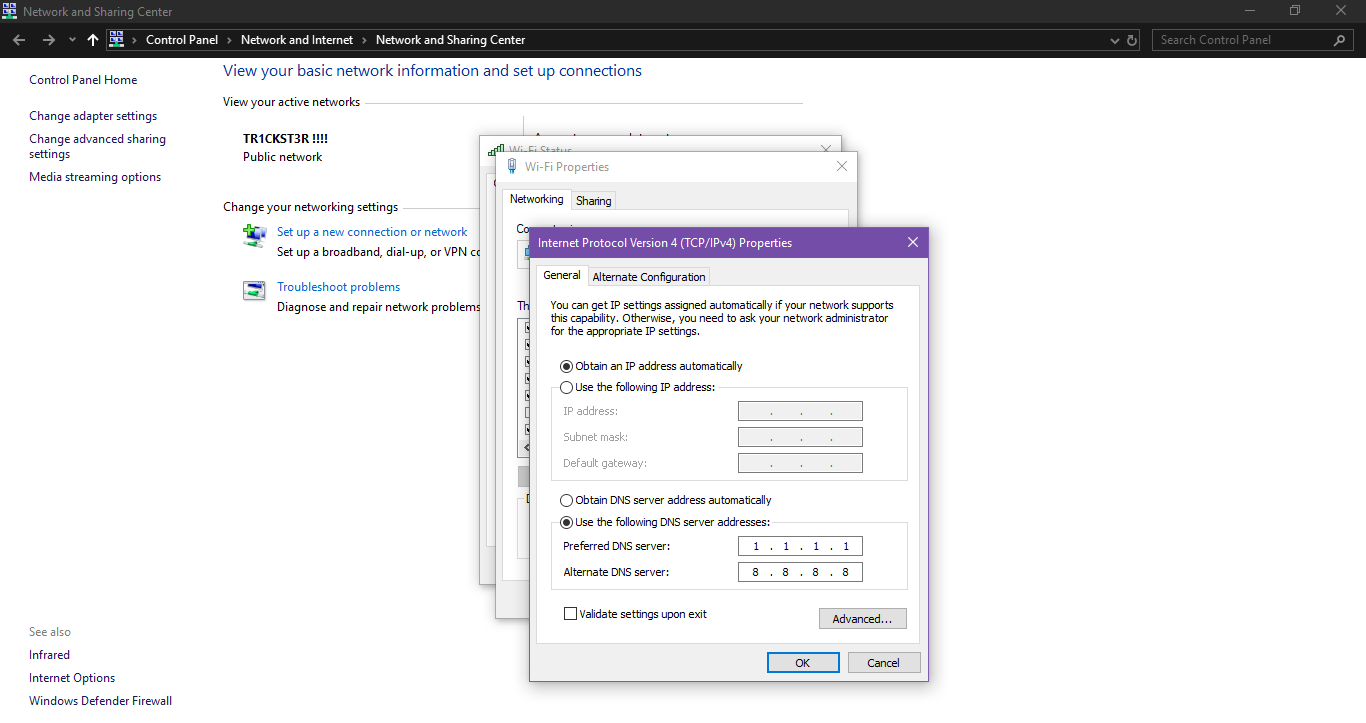
Click on TCP/IPv4 and then properties. Here change your DNS.
IP and Port Filtration
In this filtration, Firewalls or routers block the unwanted IP or a specific Port number instead of Domain Name. This type of filtration can be evaded by redirection, encapsulation and tunneling of the network traffic. There are a lot of easy methods to evade IP filtration but bypassing port restriction is a bit tricky.
You can bypass IP filtration by using Proxies, VPNs, Browser extensions and Proxy sites. A VPN routes your network traffic to another Virtual Private Server to bypass administrative filtration. VPN encrypts all the data between client and Virtual Private Server so that firewall can’t see what’s going on, it makes all connections on the behalf on client and then this connection is encrypted and sent to the client. There is a list of Proxy sites and VPNs that you can use to evade IP restrictions,
Proxy sites
http://my-proxy.com
http://proxy-site.net
http://spysurfing.com
http://bypasser.us
https://www.filterbypass.me/
https://hide.me/en/proxy/
VPNs
Nord VPN https://nordvpn.com/
Express VPN https://www.expressvpn.com/
Hotspot Shield https://www.hotspotshield.com/
Pure VPN https://www.purevpn.com/
Port Forwarding
Now in case of Port filtration, if your firewall blocks IPs of proxy sites and ports of some particular VPN or a service then a lot of VPNs, browser extensions and proxy sites might not work. Some firewalls block all ports except some common ports like SSH, Telnet, HTTP and HTTPs. For example, you’re at work and your office firewall blocks every outgoing connection except on port 21 (FTP), 80 (HTTP), and 443 (HTTPs) and you wanna play a game at https://steampowered.com/ which uses port 4444, you can’t play it because your firewall will block every connection except those 3 ports. To evade this filtration, you need another computer, this might be a spare PC at home or a server in Cloud.
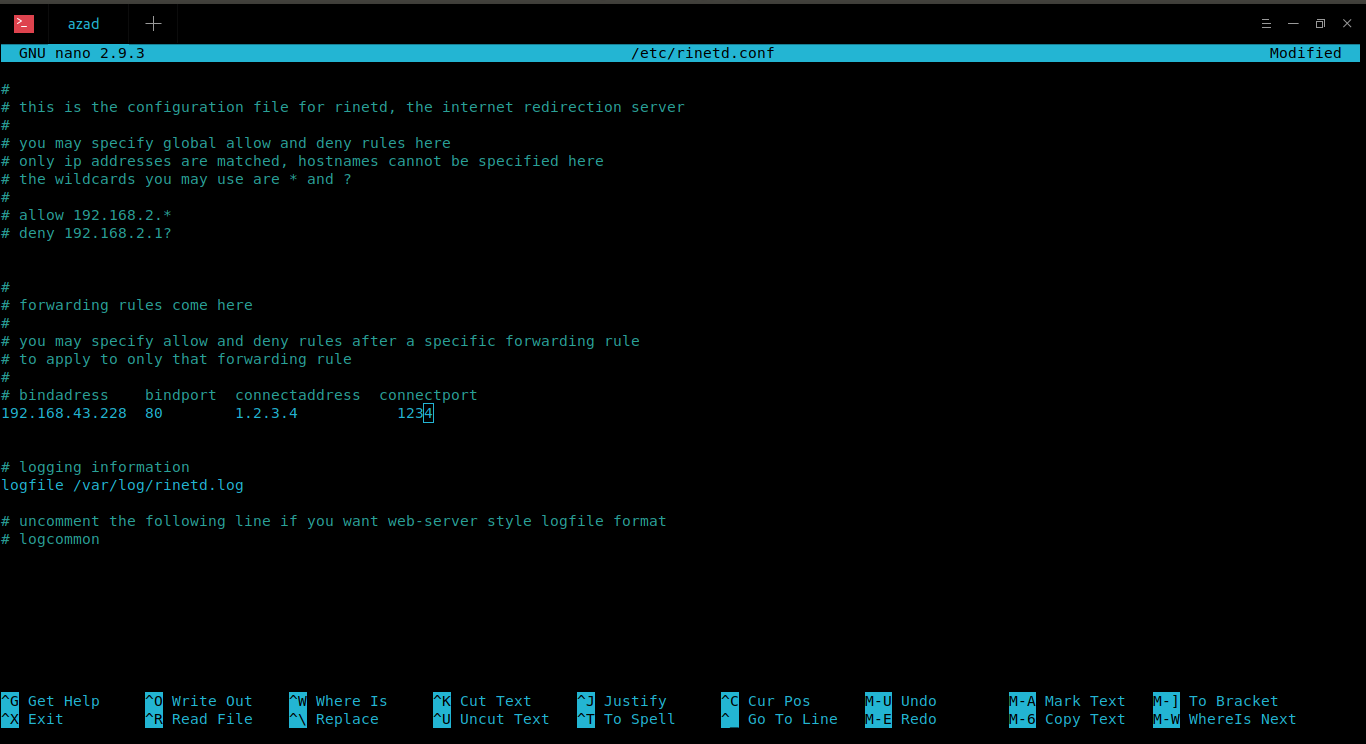
You can configure your Home PC to accept any connection on port 80 and forward it to Game Server (IP is let’s say 1.2.3.4) on port 4444. You can send your game traffic to your Home PC at port 80 which will evade port restriction because your firewalls allows connection on port 80. You Home PC will accept connection on port 80 and will forward it to Game Server (1.2.3.4) at port 4444 and will send you back the Server reply at port 80.
You will need to configure a port forwarder like rinetd available for both Linux and Windows on your Home PC. It is available for download at http://www.lenzg.net/rinetd/rinetd.html , and also can be downloaded using APT in Linux. Type the following in your terminal,
ubuntu@ubuntu:~$ sudo apt-get update && sudo apt-get -y upgrade ubuntu@ubuntu:~$ sudo apt-get install rinetd -y
Now we need to configure rinetd in a way that it accepts connection from our IP Address and redirects to the Game Server (IP 1.2.3.4) at port 4444. rinetd’s configuration file is stored as “/etc/rinetd.conf”, to edit, type
ubuntu@ubuntu:~$ sudo nano /etc/rinetd.conf
rinetd is configured, start its service by typing
ubuntu@ubuntu:~$ sudo service rinetd start
Now it’ll take all of your traffic from port 80 and will redirect it to Game server’s port 4444.
Application level Security and Deep Content Inspection
Some modern day firewalls don’t only have Network restrictions but they also inspect the content of a connection. These firewalls also see protocol name & application level communication instead of only looking at the port number. A famous HTTP firewall of this type is Squid Cache Proxy. Normally, it allows HTTP traffic on port 80 & HTTPS traffic on port 443 so even if you try to communicate with an FTP Server or a Game Server on port 80 or 443, it wouldn’t allow this to happen because it will inspect the application layer protocol too.
To evade this type of filtration, you need to encapsulate all the traffic in HTTP protocol. For example, you want to browse FTP on Server X.Y.Z but your firewall doesn’t allow FTP on any of its port even on port 80. So here you’ll use HTTP’s CONNECT method to connect to your spare Home PC or Cloud and then to the FTP Server. CONNECT was added to HTTP Protocol to offer stateful tunneling of SSL, using CONNECT you can connect to any web server within HTTP Protocol. So in order to browse FTP on X.Y.Z Server, you need to configure an HTTP tunnel using HTTP’s CONNECT on port 80 to your HOME PC instead of plain connection. So in this case, instead of rinetd, you should use applications like HTTPTunnel, Proxy Tunnel or OpenVPN to forward FTP connection encapsulated in HTTP to your Home PC or Cloud Server.
OpenVPN
Using OpenVPN, you can host an OpenVPN Virtual Private Server (VPS) on Cloud or your Home PC, that method is best described here https://www.hackingloops.com/how-to-setup-openvpn-server-on-your-linux-server/, you just need to set port 80 or 443 instead of what is used in this article.
There are some other commercial and free services that use HTTP’s CONNECT and OpenVPN in their products Like Psiphon , Tor Browser and NordVPN that you can use to bypass restrictions.
HTTP TUNNEL
OpenVPN uses HTTP’s CONNECT verb to evade firewall’s restrictions, incase you want to use HTTP’s GET, HEAD or POST verbs then you can use another amazing utility called HTTP Tunnel. It is available here to download https://github.com/larsbrinkhoff/httptunnel, but you can also be downloading using APT in Linux. You need it for Client’s PC as well as the PC acting as server (Home PC or Cloud).
azad@ubuntu:~$ sudo apt-get update && sudo apt-get upgrade -y azad@ubuntu:~$ sudo apt-get install httptunnel -y
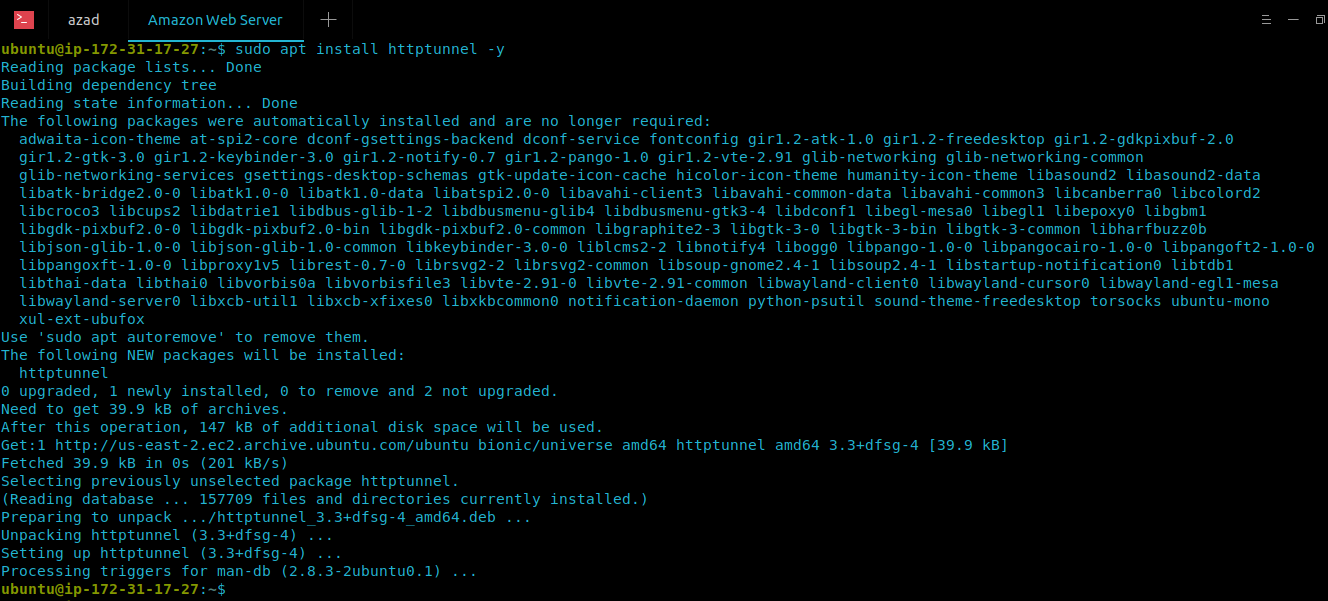
For example, you want to browse FTP Server (ftp.gnu.org) on port 21 but your deep content inspection firewall allows only HTTP connection at port 80 or 443, so you’ll install and configure the HTTP TUNNEL application on Server (Your space Home PC or Cloud) as well as the Client’s PC. Here is the scenario,
FTP Server: ftp.gnu.org Port: 21
Server (Your Home PC or Cloud): 18.X.X.X Port: 80 (to listen from client)
On your Server, run the following command
ubuntu@ubuntu:~$ sudo hts -F ftp.gnu.org:21 80
On your client machine, type
ubuntu@ubuntu:~$ htc -F 4444 [Your Home PC or Cloud's IP]:80
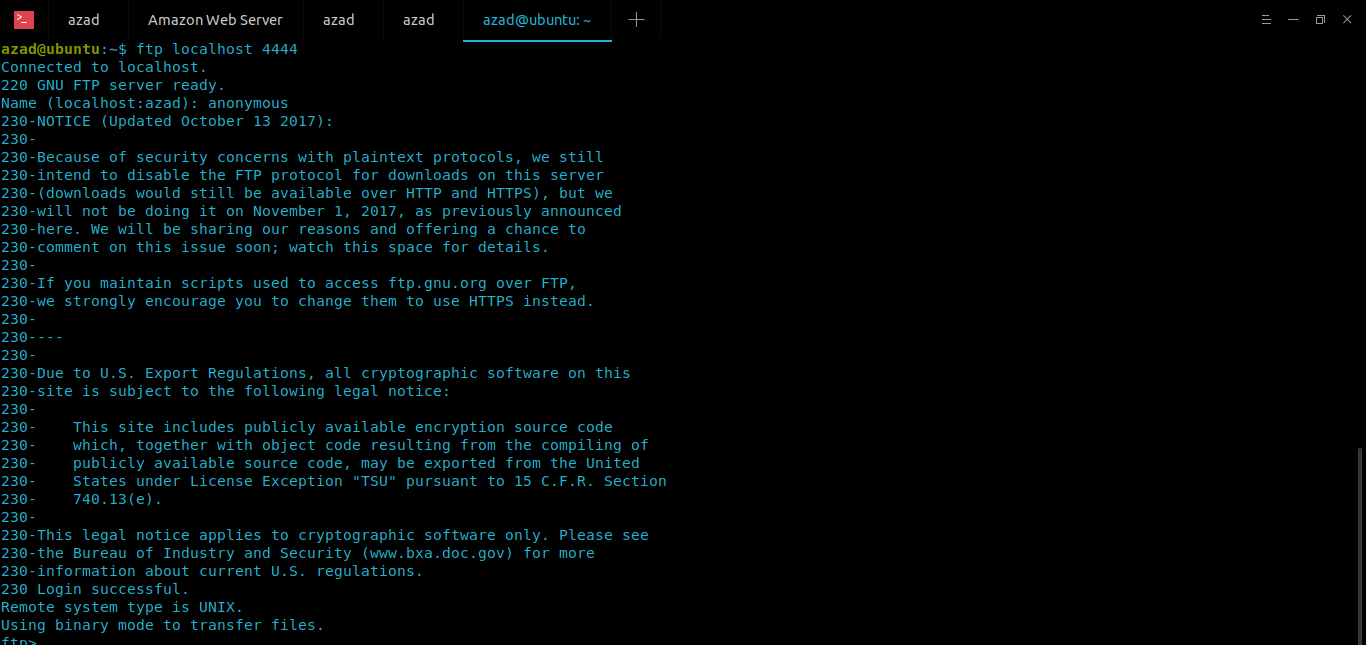
Now connect to that port (4444) on localhost, HT Client will forward your connection from localhost’s port 4444 to your server’s port 80 and then your server will forward this connection to ftp.gnu.org at its port 21. And using this you can browse FTP on clients machine. Type
ubuntu@ubuntu:~$ ftp localhost 4444
For more help, type
ubuntu@ubuntu:~$ htc -h Usage: htc [OPTION]... HOST[:PORT] Set up a httptunnel connection to PORT at HOST (default port is 8888). When a connection is made, I/O is redirected from the source specified by the --device, --forward-port or --stdin-stdout switch to the tunnel. -A, --proxy-authorization USER:PASSWORD proxy authorization -z, --proxy-authorization-file FILE proxy authorization file -B, --proxy-buffer-size BYTES assume a proxy buffer size of BYTES bytes (k, M, and G postfixes recognized) -c, --content-length BYTES use HTTP PUT requests of BYTES size ...snip...
That way you can evade restrictions by using HTTP Tunnel. HTTP Tunnel is more stealth and makes stateful connection but it is slower than OpenVPN and other utilities.

Eddie says
Nice tutoring. I love it and keep it coming
UsamaAzad says
Thanks