Working in the field of cybersecurity and IT can eventually turn into becoming an information security consultant. Methods and protocols in this sector change every day. Even if someone claimed to be an expert 10 years ago, chances are the followed procedures and tools used already expired.
Becoming a professional in the field and an expert above all requires staying UpToDate with the latest and upcoming protocols as well as syntaxes. And by far it is one of the many keys to get the attention of targeted companies for anyone looking to get hired.
This article will cover the overall points and ways someone can achieve the goals of becoming an information security consultant. Gazing through will give an individual a general idea of becoming an information security consultant.
What is an Information Security Consultant?
Information is key to everything in the world today. Most businesses and tech companies spend years collecting data. These data can be how a customer access a product, sharing statics, how it can translate to growth, and a few other notable points. But these are wrapped up around security features.
An ideal information security consultant helps clients to solve any kind of issues related to IT. It can be long- or short-term assessments with the network or giving brief ideas generally to educate on the matter.
Alongside that, an information security consultant is also a troubleshooting expert. Analyzing cybersecurity threats, regularly scanning for breaches, taking precautions and protection measures also suffice.

So, the consultant has to access the data an attacker may be interested in and try to breach that. Upon completion, statics is provided to the company on what can be improved and what ways it can be breached. With that data, a client or company fixes potential vulnerabilities.
Hacking, spoofing, social engineering, unauthorized access, spyware, ransomware, bloatware, worms, viruses, spamming’s are some of the side effects that came with technological benefits. According to Moore’s law, the number of semiconductors doubles every two years. To follow that accurately, companies and organizations are improving their tech services. And with that, the dark side is too advancing. Sadly, there are not enough specialists and consultants as we require, and the IT sector needs all available quality sets of hands.
Problems around IT are solved by information security consultants worldwide. They provide the best solution for organizations and play different roles. The consultants put on the shoe of both an attacker and the victim. It helps to allocate the issues efficiently and quickly.
Responsibilities and duties of an Information Security Consultant
In the field of information security, experience plays a vital role. Of course, responsibilities and authorities matter but no one can claim to be an expert, if the protocols are taken for granted. Firstly, being successful in the field comes from the perspective of a hobbyist.
As the procedure and learning can be quite daunting. There are too many complex algorithms, calculations to run through, and overall thinkability out of the box for foolproofing a system is required.
So, we can easily say, those who are an expert in the field enjoy what they do and pets desire to learn more.
From this perspective, responsibilities and duties come with the necessity to make an impact.
North star of an information security consultant is to provide valuable results for clients. But to be in that phase, adequate qualifications must be met. Those qualifications can be cloud certifications, web or mobile applications, IoT and code reviews, penetration testing methodologies, secure development training, Security Information and Event Management (SIEM), Security orchestration, automation and response (SOAR), etc. The list can go on and on.
An ideal information security consultant maintains teams of experts in some ways with QA or risk management sessions. Planning, coordinating, and monitoring the project activities and supporting development on some days. Troubleshooting, update maintenance, and following standard procedures to ensure project life-cycle is important too.
Skills of an Information Security Consultant
In some areas, information security is also referred to as cybersecurity. Protecting client’s networks and giving them feedback can be a day-to-day job for a cybersecurity expert. Areas of cybersecurity are vast and can fit many shoes. A specialist or consultant may be working on a single project but necessarily have to be an expert in related environments.
To become one, an individual must go through practices of learning networking, penetration testing, scripting, and certification process. A few years back, cyber-attacks were severe and done in a single wave. Today, we have many functionalities that can run the same script several thousand or million times with one click. This means more severe damage may arise so the job of a cybersecurity consultant or information security consultant became critical.
A list of skills required to pass as an information security consultant
Technical Skills for an Information Security Consultant:
• Well, understanding of IT infrastructure.
• Networking/ administrate tasks, CISA, CISSP, CISM, CGEIT, CISCO, CCNA.
• Industry-standard protocols.
• VPN, proxy, firewalls, SIEM, SOAR, IPS, etc.
• Operating systems.
• Cloud architecture e.g., Microsoft Azure Cloud or Amazon Web Services (AWS), more the merrier.
• Degrees and certifications.
• Programing language such as Python, JavaScript, C++, C#, or PHP.
• DevSecOps experience, etc.
• Web applications, mobile, desktop applications, and environments.
Soft skills that benefit overall:
• Documentation and organizational skills.
• Strong leadership.
• Communication and customer handling practice.
• Intelligent and intellectual to learn new skills.
Both technical and soft skills are required to gain the freedom to become a well-suited information security consultant or cybersecurity specialist. Don’t worry, no one comes to work with every skill in the arsenal. New things can be learned through time and practice. And these are just scratching the surface.
Achievable Goals
As we are in the sweet era of technology where a small step can cover a bigger distance, it is quite easy to get into the idea of becoming an information security consultant. But before that, the thresholds and skills we mentioned need to be there. Lacking’s of some point is not a matter of concern if the individual is willing to put in the efforts.
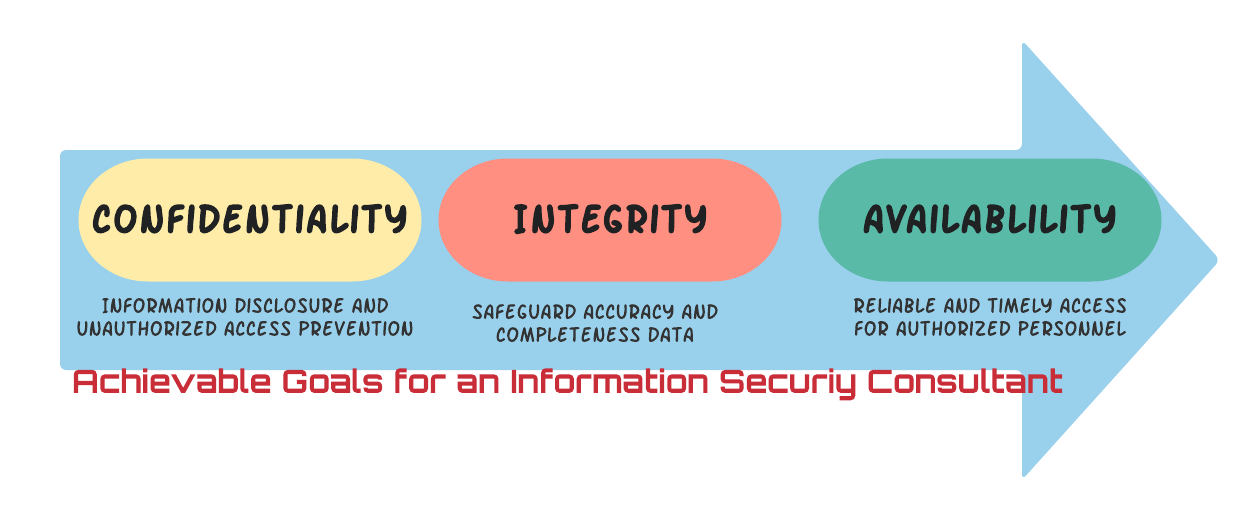
Cybersecurity specialists or information security consultants are paid adequately or handsomely and the skills are highly respected. Nonetheless, the makes it easier to hang around with brilliant individuals who are also interested in relevant fields. The subject and position for jobs are highly technical. So, summarizing the needs of customers is not that difficult, but some troubleshooting’s truly are. Joining webinars, teaching young people cybersecurity topics, and helping overall global tech prosper is the goal.
Wrapping Up
Ending our small session on how to become an Information Security Consultant with roles and responsibilities.
“You don’t understand anything until you learn it more than one way.” – Marvin Minsky.
This article is a guide to know some information related to the field to get started. It can be expanded as much as one wants. There is more than one way to learn. Hands-on practice on different tools will take someone further. This article hopefully will provide enough ideas for a beginner or someone choosing to take a carrier path.

Leave a Reply