
What is Smishing?
Smishing attacks are when a phishing attack occurs over text messages (such as WhatsApp or SMS, which is where the name comes from). Sounds simple, right? Yet the smartphone environment opens up a whole new world of opportunity for phishing attacks. For example, phone numbers don’t have the same security level as modern email.
One example: spoofing a phone number is too easy. So you can pretend to be someone else. Also, you can convince phone companies just to give you someone else’s number! This is a common attack that we in the infosec space call SIM swapping. This is also how hackers steal accounts that users protect with two factor authentication. Need to receive a special code via text message? No problem, just steal their phone number and receive the code yourself!
The list goes on and on. We’ll show you more common tricks, then walk you through a real life smishing attack so you can see how this works. Without further ado let’s see what kinds of attacks there are!
Types of smishing attack
Just like any other social engineering based attack, there are a million ways to smish someone. But these days, the attacks tend to fall into the following categories:
- Customer Service Smishing
- Invoice or Order Confirmation Smishing
- Free Stuff Smishing
- Financial Services Smishing
- COVID-19 and Emergency Smishing
These categories fall into the oldest pressure trick types in the world: MICE. That stands for Money, Ideology, Coercion, and Ego. When bad guys try to trick you into doing something you shouldn’t, they’ll often borrow tactics from those four basic types of pressure.
Other attacks are more traditional. Below is a traditional smish using basic tactics, to show the core of how a generic smish works in the wild.
Showing a real life smishing attack
You receive a message…from yourself? The message is urgent, and seems important. Maybe someone was using your phone and sent this to you? Intrigued and anxious, you unlock your phone and open the text message.
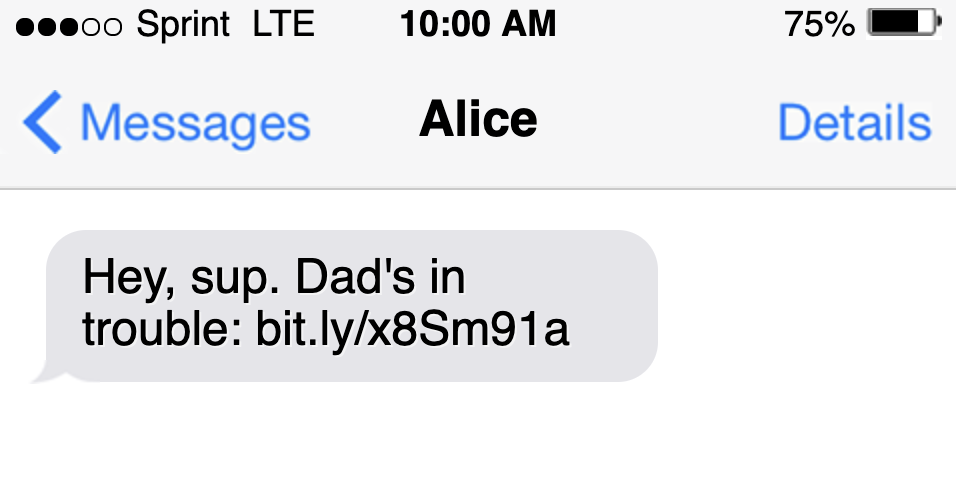
Huh, that’s weird. Little do you know, the attacker is forging your own number because unknown numbers often don’t get through. They know your own number will appear as known on your phone, so the message won’t be flagged as easily.
So you go ahead and click on the link. Then a website opens and you hear a voice message from your dad saying they need your help immediately.
You have no way to know it, but the attacker generated this fake voice using the FakeYou AI. When phishers use voice attacks, they call it vishing. This AI lets them impersonate anyone, as long as they have access to the victim’s voice.
The link redirects to a web page with a messaging app where you can give the attackers your login. On that page, they claim to have your dad held for ransom. Do you send the money, or risk losing your own dad?
Let’s learn how to prevent smishing, so you never have to answer that question. After all, an ounce of prevention is worth a pound of remediation!
Preventing Smishing Attacks
The number one way to defend against smishing is to call your phone service provider and lock down your number. This will prevent SIM swapping, which is useful for smishing as well as a myriad of related attacks.
If you want a state of the art window into smishing to defend against next gen attacks, sign up for dark web hacking forums and learn how the bad guys are doing things.
Finally, you will want to sign up for HaveIBeenPwned so you can receive alerts when any credentials relevant to your company show up in new data breaches.
Big Smishing Attack Cases
Perhaps the best known smishing attack: in 2020, smishers told victims they could get free, new iPhones if they sent credit card info. Which many of them did. The attackers made off with hundreds of thousands of dollars in the end.
In a recent smishing attack against iPhone fans, hackers in Eastern Europe made off with nearly a million dollars. Law enforcement is investingating the attack but there’s little hope of arresting the suspects due to lack of international coopoeration in the region where the attackers are believed to reside. Companies in the US and it’s allied nations should seek to harden themselves against these novel attack vectors, rather than just relying on traditional law enforcement to discourage the behavior.
White House Cybersecurity Office, December press release 2020
More recently, the most famous COVID smish involved offering a free test, with links to super cheap medicine. Seniors clicked the links, and sent the money, except the medicine didn’t exist. The attackers simply scammed them out of their money. Seniors are common targets for phishing due to their trusting nature and lower knowledge of modern tech.
Conclusion – Don’t trust any suspicious texts even if they come from you
Smishing has become a lot more popular since the use of smartphones has also become a lot more popular. Not only is smishing also very popular but it has resulted to be very effective. It is good to be very cautious of any suspicious links or even messages that you receive. Sadly, phone calls are also very easy to get scammed by so make sure to not put your info anywhere suspicious. It’s preferable to not put your info anywhere online unless it’s totally necessary.
You should consider text messages from unknown numbers as unsafe. If you get a text message from yourself that you don’t remember sending don’t pay attention to it. Remembering little tips like these can help a lot. So, make sure to take them into account in order to save yourself from a scam.
Hopefully, you now have a much better idea of how smishing works and what you can do to protect yourself. I wish you the best of luck keeping you and your team safe, and keep reading HackingLoops for up-to-date info on today’s top hacks!

Leave a Reply