oclHashcat is legendary for good reason but Hashcat is the newer bigger cat in town and the best password cracker these days to get the job done. We are going to take a deeper dive and show you exactly how to crack passwords with unbelievable speed so let’s get started.
Hashcat is one of the advanced security tools used for recovering passwords from hash values. The tool supports more than 150 algorithms including the highly optimized SHA256, SHA512, MD4, MD5, HMAC, LM, NTLM, WPA, DES, and triple DES algorithms. Hashcat can crack multiple hashes simultaneously with pause and resume capabilities.
Hashcat Installation (similar to oclHashcat)
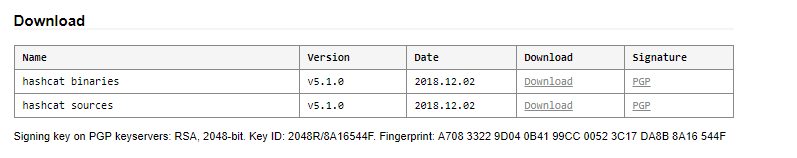
Hashcat is an open source tool that is supported by all major Operating Systems including Windows and Linux. The tool comes as a pre-installed utility in Kali Linux distribution. In Windows OS, the tool does not require any installation. Download the latest version of Hashcat binary package from the following official repository and unpack the package using 7 Zip open software.
https://hashcat.net/hashcat/
Hashcat requires certain GPU drivers as mention in the following screenshot.
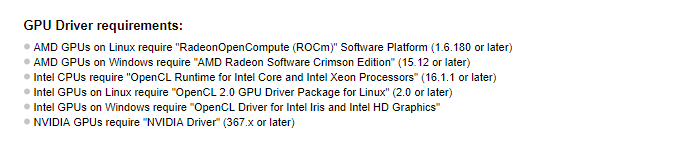
In case an update is required, upgrade the GPU drivers according to the OS. In Windows OS, the GPU drivers’ version can be queried through dxdiag command. In our case, OpenCL driver is required as we are installing Hashcat on Windows10 OS with Intel’s HD graphics.
How Hashcat Works (many similarities to the older oclHashcat)
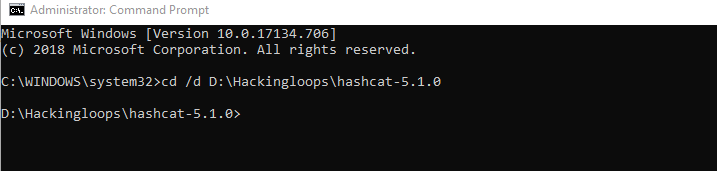
Open the command prompt and set the path of the directory containing Hashcat files. In our case it is D drive> Hackingloops folder> hashcat-5.1.0 folder.
cd /d D:\Hackingloops\hashcat-5.1.0
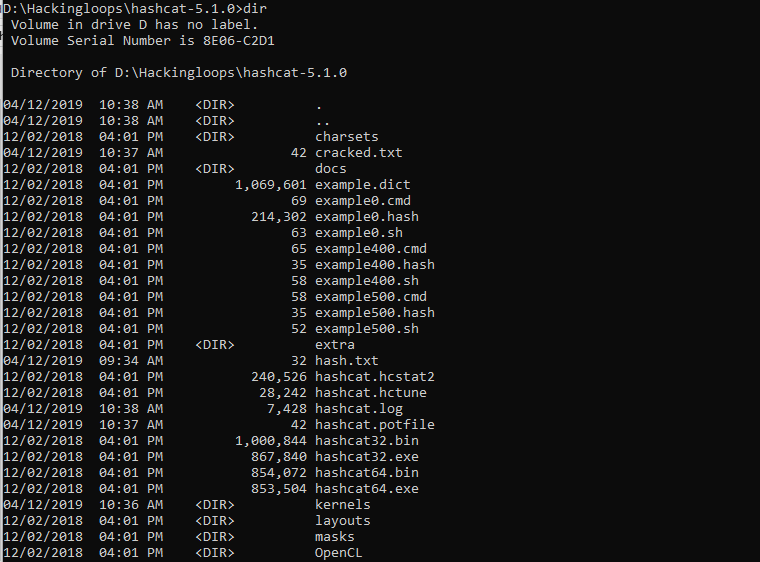
To confirm the path, type the following command to see all the directories in the folder.
D:\Hackingloops\hashcat-5.1.0>dir
Type the commands in the terminal based on the desired attack to crack the secrets in hash values.
Password Recovery Example
There are different ways we can use Hashcat to crack the passwords. In this particular example, we can use the following command format to crack the hash values.
<hashcat executable > <-m value> <-a value> <-o files>
<hashcat executable> is hashcat64.exe or hashcat32.exe, depending on the OS running the tool.
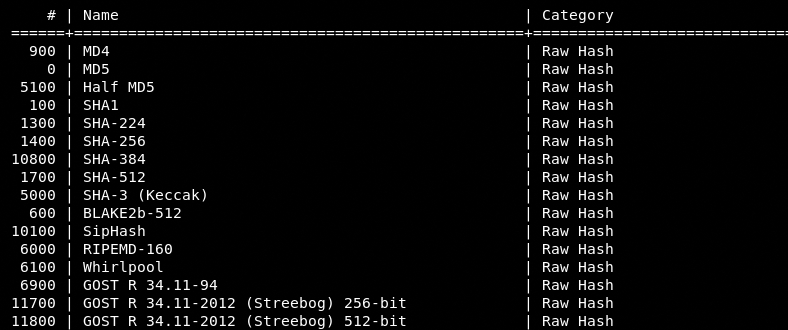
<-m> represents the type of algorithm that is being attacked by Hashcat. Hashcat supports more than 150 algorithms. Each algorithm is assigned a sequence number. The following screenshot shows the sequence numbers for some of the supported algorithms. The complete list of algorithms and associated sequence numbers can be found through help command [hashcat –h] or visit the official wiki page of the tool: https://hashcat.net/wiki/doku.php?id=hashcat
<-a> represent the attack mode. Hashcat supports five attack modes namely Bruteforce, Combination, Straight, Hybrid dict+mask, and Hybrid mask+dict. In a dictionary attack, the tool reads each line of the specified text file as a password candidate. The combination attack is similar to the dictionary attack. Here the tool uses two dictionaries to guess the hashes. The mask attack is a brute-force attack type that operates on user-specified characters set. Here the tool tries all the combinations in a given keyspace. The hybrid attack is a combination of the mask and dictionary attacks. Each attack mode is assigned a sequence number similar to the algorithms.

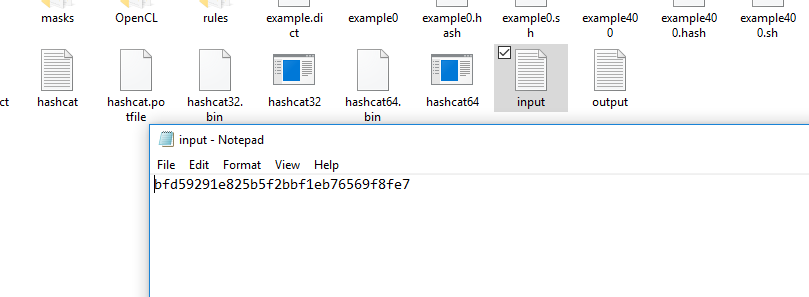
In this example, we are using brute-force attack mode to crack a MD5 hash value. In order to execute the attack, we need to create two text files in the tool’s directory. Hashacat reads the hashes (to be cracked) from one file and writes the cracked secrets on another file. In our case input.txt is the file containing the hash values and output.txt is the file where the cracked results are stored. Let’s assume asd123 is the secret with the following MD5 hash value.
Hash: bfd59291e825b5f2bbf1eb76569f8fe7
Store this hash in the input.txt file as shown in the following screenshot.
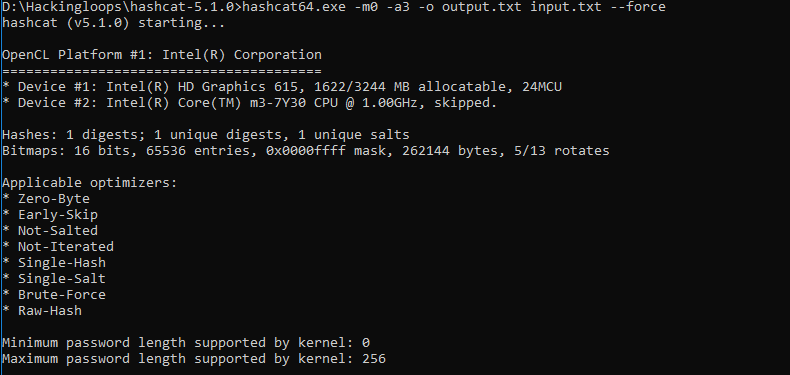
Run the following command to crack the hash value mentioned in the input.txt file.
hashcat64.exe –m 0 –a 3 –o output.txt input.txt --force
The current version of Intel’s OpenCL has a runtime issue while executing Hashcat. Since we are using Intel’s OpenCL, We have used the –force parameter in the command to override the error.
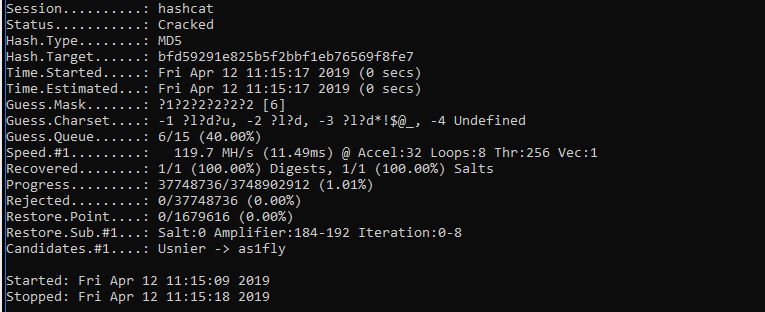
Hashcat can operate in sessions to crack the secret hash. The status of the session (Exhausted | Cracked) can be seen under the session name.
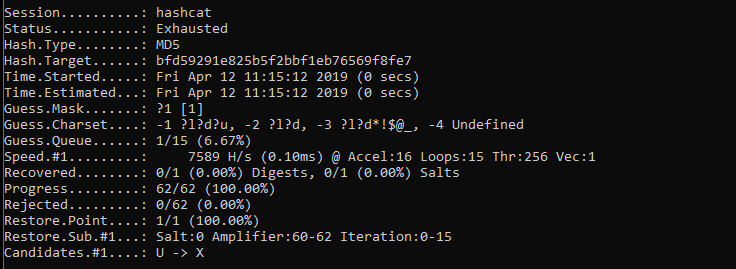
When Hashcat successfully finds a secret with the similar hash value as mentioned in the input.txt file, the session status changes from Exhausted to Cracked.
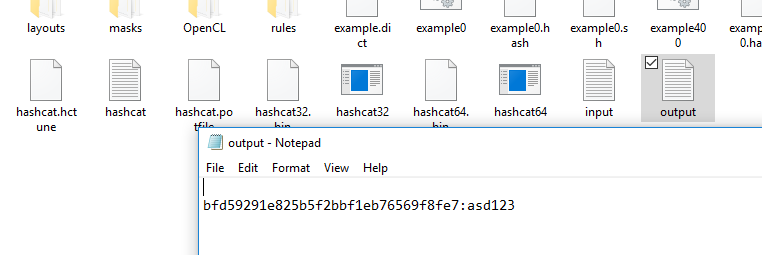
The cracked secret can be seen in the output.txt file as shown below.
Summary
Hashcat is one of the fastest ways of cracking secrets generated through some of the highly optimized hashing algorithms. The tool can be the optimum choice of red teamers and digital Forensics experts in scenarios where bulk hash files are required to be cracked in a single operation.
