Just about anyone with even a slightly above average understanding of computers, networks, and the Internet has heard of a DDoS attack. Even users who don’t understand what they are or how they work have likely been exposed to them by movies. The truth is that they can be incredibly effective and disruptive, and white hat hackers are always on the lookout for ways to prevent themselves from becoming the next victim. But DDoS attacks are shrouded in a cloud of mystery. After all, what are they, and how do they work? Well, we are going to answer these questions with a brief tutorial.
What is a DoS Attack?
A DDoS attack is a Distributed Denial of Service attack, but first let’s define a DoS attack. In a DoS attack, flaws and code vulnerabilities are exploited with one main goal: to overwhelm a resource so drastically that it ceases to function correctly. For example, if an attacker wanted to initiate a DoS attack against a website, the attacker might generate so many requests that the web server couldn’t possibly keep up with the demands, making it unavailable for other web surfers.
However, a distributed DoS attack is a little different in that it is not initiated by a single host. Instead, the attack is carried out by a network of different machines that make it hard to pinpoint the origin of the attack. Humorously enough, I have seen gamers resort to using a DDoS or DoS attack to target other online gamers when their tempers flared, or when they wanted to boot the winning player from the game. However, even though this is admittedly amusing, it is also illegal.
This guide is intended as a way to show you how DDoS attacks work, not to give you a tool to attempt to take down a website or mess with your neighbor. If you have dreams of taking down a website, watch out. There are legal implications and negative consequences if you get caught. I would advise you to try this out on a network or entity you control. For example, if you host your own Minecraft server, that would be a perfectly acceptable test – but only if you own, control, and manage the server.
The truth is that there are many sophisticated and advanced ways of initiating these types of attacks; one of the more advanced techniques is called hping3. Today, however, we are going to be looking at how to DDoS an individual IP address using an extremely simple piece of software.
Note that my antivirus software raised some flags after the download, but it appears to only recognize that this code was developed to initiate attacks. After scanning my computer post install, I didn’t find any viruses, and it only labeled the software as a PUP (potentially unwanted program). You might have a similar experience, but the code seems fine to run.
The steps are as follows:
Step 1: Download and Install the Application
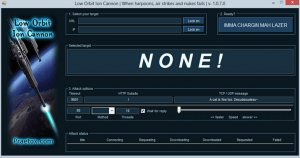 The first thing you need is the software. We’ll be using LOIC (Low Orbit Ion Cannon – I know, sounds like something from a Sci-Fi movie, right?) to carry out the attack. Proceed by downloading the file and extracting it in a location of your preference, though I just did it on my desktop.
The first thing you need is the software. We’ll be using LOIC (Low Orbit Ion Cannon – I know, sounds like something from a Sci-Fi movie, right?) to carry out the attack. Proceed by downloading the file and extracting it in a location of your preference, though I just did it on my desktop.
Step 2: Target an IP Address of a Website
Go ahead and fire up the software after you have installed it. The first things you should notice at the top are the fields that are labeled as your target. If you want to test out this software on a website, go ahead and enter the URL. If you want to try this on another type of server, perhaps a game console on your local LAN while it is playing an online game, go ahead and enter its IP address. Whichever you chose, go ahead and click the “lock-on” button next to the field.
Step 3: Setting Up the Attack
Now we want to focus on the portion of the interface that shows different options and settings. Leave the timeout, HTTP subsite, and speed at the default settings (you can play around with these later, if you want). However, in the TCP/UDP field go ahead and enter some random message. Furthermore, pay attention to the port field. If you are attacking a common HTTP web server, this will be port 80, however, this could change depending on the service you are trying to overwhelm. Lastly, disable the “wait for reply” and keep the thread count at 10.
Step 4: Attack!
The only thing left to do is to actually run the attack. Though I can’t say that I really like the language used in this application, it is one of the simplest ways to run a denial of service attack. After the fields have been filled in, simply click the “IMMA CHARGIN MAH LAZER” button (ugh). Then the attack status should be displayed. It will essentially show you the number of requests that have been made for a given service. For example, if you are attacking a website (that you own, of course), it will show you the number of HTTP requests that have been generated.
Final Thoughts
Admittedly, there are much more sophisticated ways to run this type of attack, but again, this tutorial was aimed at simplicity. A lot of beginners want instant gratification, which this simple utility delivers. However, the ugly truth is that to become truly competent, a burgeoning hacker needs to invest countless hours studying their craft. In another tutorial, we’ll look at some more advanced ways to run denial of service attacks.
Final Warning
It cannot be stressed enough. Do not use this software in the real world to carry out an attack. That is illegal, and it can land you in a boatload of trouble. If you want to test a DoS attack to see how they function (as well as how to prevent them with different security defenses), only try them on your home network!
