Cybercrimes are pretty common matters today, and every single variant can take place at any time. We understand that an attack can happen at any moment, but the MITRE ATT&CK assumes it already took place and executes the solution swiftly. The MITRE ATT&CK framework is constantly evolving with the help of highly competent IT personnel and security teams. It is a common language among professionals comprising of techniques, tactics, and procedures.
“With the creation of ATT&CK, MITRE is fulfilling its mission to solve problems for a safer world — by bringing communities together to develop more effective cybersecurity. ATT&CK is open and available to any person or organization for use at no charge.” – MITRE Corporation
Followed up by standard adversarial techniques, MITRE ATT&CK also stands for tactics and common ATT&CK knowledge. From 2015, the framework started with the motive to help understand adversary behavior with adequate security and acted as a baseline to advance defense against adversaries. The cybersecurity community matured enough for subsequent use of the framework rather than clinging to one technique.
What is the MITRE ATT&CK Framework?
The framework, on the whole, is pretty simple. Rather than focusing on every type of cyber threat, it reflects the lifecycle of techniques. The framework consists of Structured Threat Information Expression (STIX™) used by cyber threat intelligence (CTI), spreadsheets containing dataset, ATT&CK navigator for annotation, exploring metrics, workbench, which is a whole application itself, along with Python utilities for automation tactics with those datasets.
ATT&CK can focus on the enterprise-level solution to catch up with operating systems like the Windows, Mac, Linux, and cloud environment along with the mobile OS, e.g., Android and iOS. Pre-ATT&CK for adversarial behavior recognition, also known as “pre-exploit,” goes both for enterprise and mobile ATT&CK. We determine the sectors by OS because it is the baseline of hardware and software used by both adversarial groups and security specialists.


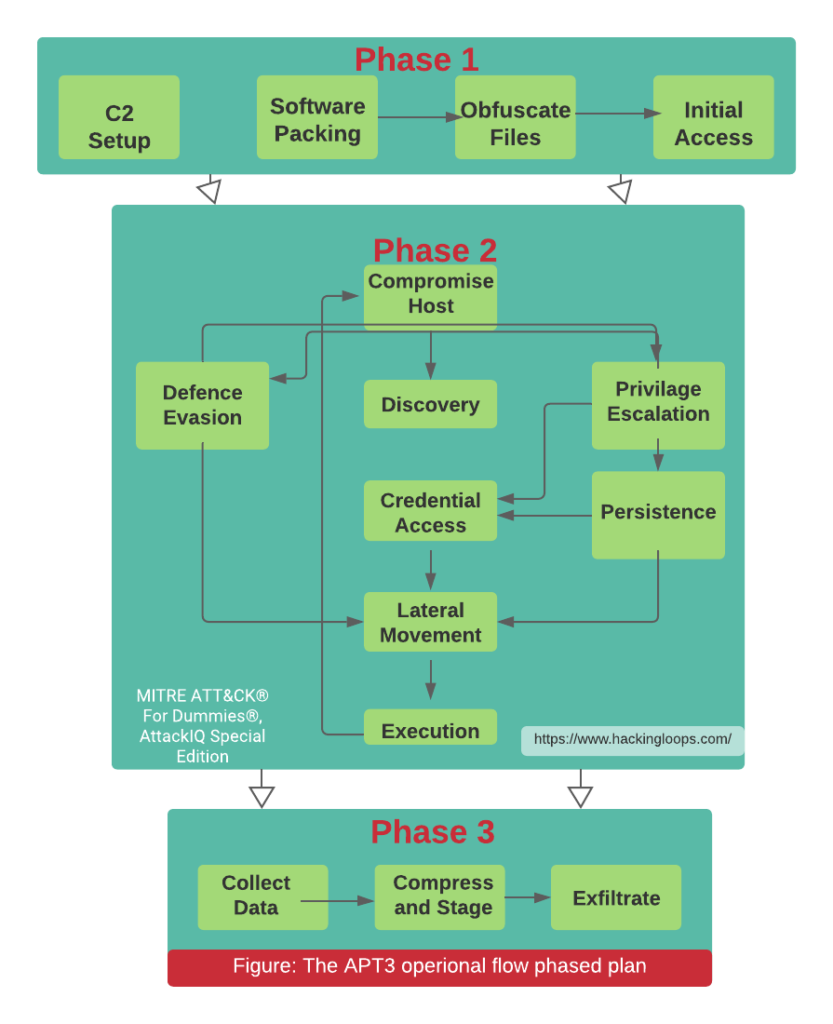
The ATT&CK Matrix for Enterprise has Reconnaissance, resource development, initial access, execution, persistence, privilege escalation, defense evasion, credential access, discovery, lateral movement, collection, command and control, exfiltration, and impact as primary categories like the chart shown above.
These stages can break into subsections depending on the type and severity of the action. Clicking each technique explains broader details clearly with the definition, tactics, and techniques of an ATT&CK. It concludes our initial framework breakdown for MITRE ATT&CK.
Building Detection and Analytics
According to the “MITRE ATT&CK for dummies,” understanding the current state and search capabilities is essential to create data analytics. A resourceful way is to browse the data sources listed for each ATT&CK technique. There are several protocols to gather data with as like as monitoring task process, command-line containing Windows event logs, endpoint detection and response (EDR), system logs.
Another great way to find analytic data in Laymen’s terms is to monitor files and registers along with authentication logs and examining packet captures. Packets contain data from the host, sender, or receiver of a network and even sensor information, which is an excellent way to “mine” analytics for building detection algorithm.
Here are some resources to help along the way for data testing of the security operations center (SOC) as a starting point. Both are found in JSON and standard text-based format and loading options for ELK, Splunk, and SIEMs.
- MITRE brawl public game
- Splunk
- From McAfee, training from ATT&CK homepage.
- Medium resource, Tripwire guide, and documentation from F5 Labs.
We already mentioned pre-attack, prioritizing diagram on the official MITRE ATT&CK Corp. priority definition, target selection, information gathering, weakness identification, persona development, establishing and maintaining infrastructure, adversary OpSec, Test and stage capabilities initial access, execution, persistence, privilege escalation, defense evasion, credential access, lateral movement, discovery, collection, exploitation, command, and control are the most important notes to take away.
Using MITRE ATT&CK and Threat Intelligence
The MITRE Corporation is a federally funded research and development organization working as a non-profit for public safety. There are many known and unknown actors in the threat world, which is included in the threat intelligence category.
To use MITRE ATT&CK and threat intelligence, one must understand the adversary by “studying its behaviors.” Later, a good grasp on which adversaries targeted a sector and used TTP. From there, a method of detection and prevention is generated to help prevent the attack. Enterprises have their own data log, so the threat intelligence protocol manually removes false positives and detections, helping detect only accurate ones built step by step with the MITRE ATT&CK framework.
Organizations create teams for tackling threats such as:
Blue Team: For achieving defensive security measures, a blue team is formed. They work inside a security operations center (SOC) and have various responsibilities.
Red Team: This team is formed to perform penetration tests and similar patterns to adversarial groups. This group is smaller than a blue team to cut down costs and have scalability.
Purple Team: The purple team consists of both ingredients of the blue and red team and their work ethic, along with the permission to execute coordinated improvement on the overall security program.
Utilizing MITRE ATT&CK
The MITRE ATT&CK matrix can work in several ways to help an organization adapt to the latest security practices and achieve great results. As the team behind MITRE works closely with the federal government, all its parts and resources are sourced from the most reliable components. Utilizing MITRE ATT&CK can give the following benefits:
- SOC Maturity Assessment: ATT&CK came a long way with perfection and testing that can give an effective detection, analysis, and response solution.
- Behavioral Analytics Development: This component is highly adequate with the techniques used in the framework as behavioral analytics proved to be much worthy in detecting or predicting threats. It would be inefficient to assume specific tasks and work with them one by one. Still, following behavioral analytics, the teams can now follow and monitor particular behavior regarding the platform to detect intrusion or adversaries.
- Adversary Emulation: The components in the MITRE framework emulates specific parameters and defensive threats to manually tackles risk component within the system. Teams apply intelligence with the adversary techniques to simulate threats and strengthen the defenses along with emulations by purple teaming.
Best Practice
The cyberworld is vast, and to stay protected at all levels requires severe attention. Every bit of tech we have today involves some sort of software or programming. Even the most minor firmware can have consequences on the hands of illegal parties. Turning human history into an online chapter is an ongoing process but at what cost? If the loopholes are not correctly patched, criminal organizations can take an interest and penetrate the most secure firewall.
 For that reason, cyber intelligence parties, IT authorities, and governed entities took the matter into their own hands and developed many modules of flawless security. Also, building a better wall against the enemy by keeping them out of the system and understanding adversary intrusion signs.
For that reason, cyber intelligence parties, IT authorities, and governed entities took the matter into their own hands and developed many modules of flawless security. Also, building a better wall against the enemy by keeping them out of the system and understanding adversary intrusion signs.
For best practices, adversary library tactics should be placed with technical goals. Proper techniques of achieving the goals, and procedures to implement appropriate strategies are some of the best approaches to achieve the MITRE ATT&CK framework. Using adversary follow-ups by external research around detections, sharing information throughout the community, leveraging integration with tools, and encouraging vendors and service providers may give more noticeable results.
Conclusion
The MITRE ATT&CK framework help cybersecurity professional and companies to understand adversary movement easily. Rather than focusing on a single tactic of breach or two, adjusting ATT&CK can widen the view. With the help of automation tools, the scanning and defending became much flexible. It gives time enough time to protect against attacks and keep information protected.
MITRE contains a massive library of cross-referenced repository of information along with MITRE’s APT29 evaluation. Defenders and professionals are now highly confident of their abilities by using the proper format of the MITRE ATT&CK framework.
