How to Fingerprint Web Application Framework : Web Application Framework Fingerprinting is one of the most important task information gathering. Knowing the type of framework a web application is using will give a great advantage to hacker or penetration tester. Because once we know framework, we can easily locate known vulnerabilities in that framework. Most of the web frameworks are widely used by popular websites across the globe which help an attacker to spot them. This is basically what all automatic tools do, they look for frameworks used from a predefined location and then compare it to the database of known signatures.
Note : This penetrating testing tutorial is also useful for CMS(Content Management Systems) along with WAF(Web Application Frameworks).
Since we are focused on finding out the Web Application Framework used by a website or web application, it means we don’t have any information about what Web application framework is being used by website or web application. So we will be following Black box pen testing approach. So let’s begin with our Penetration testing approach for Fingerprinting Web application Framework.

Web Application Framework Fingerprinting
Penetration Testing to Fingerprint Web Application Framework :
There are lot of things which can help us in Fingerprinting Web Application Framework, some of them are mentioned below :
- HTTP Headers
- Cookies
- HTML View Source
- Specific Files and Folders
Lets discuss these one by one how we can use them to Fingerprint Web Application Framework. Lets start with HTTP Headers..
HTTP Headers to Fingerprint Web application framework :
The most common way to identify Web Application Framework is to look for X-POWERED-BY or X-GENERATOR tags in HTTP headers as these tags contains information about frameworks. This approach might not have 100% success rate but yes in most cases it will help.
Sample HTTP headers look like below :
HTTP/1.1 200 OK Server: nginx/1.4.1 Date: Sat, 07 Sep 2013 09:22:52 GMT Content-Type: text/html Connection: keep-alive Vary: Accept-Encoding X-Powered-By: PHP/5.4.16-1~dotdeb.1 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache X-Generator: Swiftlet
In above example, you can see X-Powered-By is showing us PHP version and X-Generator is pointing that Swiftlet is actual framework. It helps a penetration tester or hacker to expand his attack vectors. When performing fingerprinting, always carefully inspect every HTTP-header for such leaks.
Now lets move to Cookies..
Cookies to Fingerprint Web Application Framework :
Another similar and even more reliable way to determine the current web application framework are looking for framework-specific cookies.
Consider the following HTTP request :
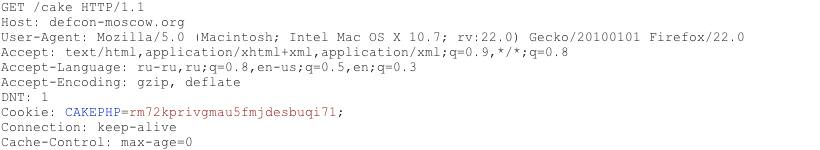
Sample HTTP Request to Fingerprint Web Application Framework
The cookie CAKEPHP has automatically been set, which gives information about the framework being used. You can google for list of common cookies generated for frameworks. Limitations are the same – it is possible to change the name of the cookie, so its success rate is also not 100%.
Another way of fingerprinting web application framework is looking into HTML source code of website and looking for meta tags and other frameworks specific files.
HTML View Source to Fingerprint Web application Framework :
This technique is based on finding certain patterns in the HTML page source code. Often one can find a lot of information which helps a tester to recognize a specific web framework. One of the common markers are HTML comments that directly lead to framework disclosure. More often certain framework-specific paths can be found, i.e. links to framework-specific css and/or js folders. Finally, specific script variables might also point to a certain framework. Also you can look for meta tags which contains generator information.
More frequently such information is placed between <head></head> tags, in <meta> tags or at the end of the page. Nevertheless, it is recommended to check the whole document since it can be useful for other purposes such as inspection of other useful comments and hidden fields. Sometimes, web developers do not care much about hiding information about the framework used.
Now 4th way identify framework is looking for Specific Files and Folder.
Specific Files and Folders to Fingerprint Web Application Framework:
Specific files and folders are different for each specific framework. It is recommended to install the corresponding framework during penetration tests in order to have better understanding of what infrastructure is presented and what files might be left on the server. However, several good file lists already exist and one good example is FuzzDB wordlists of predictable files/folders.
We can use WhatWeb tool to do all above steps. But that’s for script kiddie’s.
That’s all for today!! Keep Learning !! Keep Connected!!
