Today we’ll be running through a simple tutorial with the Harvester. Apart from showing you how to run the command, we’ll also be talking about how it’s supposed to be used, and what value it provides for a penetration tester or hacker.
It does come packaged with Kali, though it can be installed on other Linux systems. Also, I’m going to assume that you already have Kali (or another Linux distribution) installed. Furthermore, you should be comfortable running commands from the BASH shell. But I would also like to point out that this isn’t an overly complex tool that takes advanced knowledge to use.
In fact, it’s actually rather simple. And it’s really more of an automated information gathering tool than anything else. Nevertheless, the Harvester is pretty darn useful for hackers, and it shouldn’t take very long to pick up, either.
Not Your Typical Hacking Tool
The Harvester isn’t your usual hacking tool. Whenever someone mentions command line hacking utilities, your thoughts probably naturally gravitate towards programs like NMAP, Metasploit, Reaver, and wireless password cracking utilities. But the Harvester doesn’t use advanced algorithms to crack passwords, test firewalls, or capture local network data.
Instead, it gathers public information such as the names of employees, their email addresses, subdomains, banners, and other similar information. But why collect this information, you might ask? Well, it is extremely important in the first stage of reconnaissance and information gathering. Knowing these types of information will help a hacker or penetration tester gather an idea of their target, and understand them better.
Furthermore, it will help paint a picture of just how big the target’s Internet footprint is. In addition, it’s useful for organizations who want to see how much of their employees’ information is available to the public on freely accessible web pages. The latest version of the tool has added some useful features such as the ability to set time delays between web server requests, improved sources search, enumeration techniques, graph and statistic plotting, SHODAN integration, and more.
Essentially, given certain criteria, the Harvester will run around on the Internet as your surrogate, snatching up any and all information that fits certain criteria. I would also like to point out one more thing before moving forward. This tool can be used to gather email addresses, which could be incredibly useful to an attacker trying to crack online login credentials or gain access to an individual’s email account.
Using The Harvester
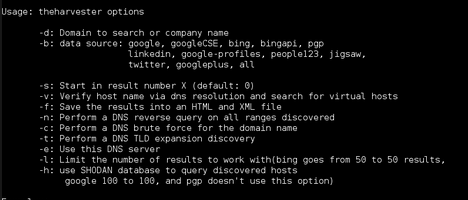
The Harvester has a rather basic command syntax. And it isn’t as complicated as some other hacking procedures such as cracking a Wi-Fi password, which can have as many as 10 steps or more. The following outlines the Harvester’s basic command syntax:
- theharvester -d [domain] -l [number_of_results] -b [source_of_search_query]
However, first you’ll need to type ‘theharvester’ into the shell to launch the program. Using the preceding query on a domain of your choice will return email addresses, depending on how many you set the limit to. And the results can be stored in a file of your choosing. For instance, I could run the following query on a school’s website to gather email addresses of all the faculty:
- theharvester -d myuniversity.com -l 500 -b google
…and that’s about all there is to it. See? I told you it was simple! Of course, there are some additional special options and flags, but that’s the Harvester in a nutshell. Note that you can substitute different domains and search engines, too. Also consider that you could use the collected email addresses as tools to attack login passwords through account recovery procedures. But don’t do that in real life – just know that hackers can utilize the Harvester this way.
Final Thoughts
Normally with Kali tutorials, I have to give a disclaimer detailing a spiel about how you shouldn’t abuse the tool we used. After all, breaking into computer systems is against the law. However, the Harvester program is different. You can use it to your hearts desire to gather information as much as you want – so long as you don’t abuse the data.
I don’t need to provide a disclaimer because all the information it gathers is already in the public domain. If you really wanted to, I suppose you could manually crawl the web to gather all the information that this tool collects – but it would take a while. The only real abuse I can see someone easily committing with this tool (without the aid of more sophisticated hacking, reconnaissance, and information gather tools) is farming email addresses for a spammy marketing campaign. Other than that, feel free to play around with this tool and craft your own unique queries.

Leave a Reply