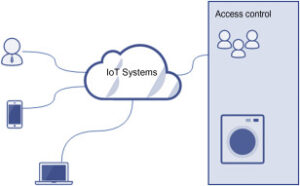
MQTT Attacks – Comprehensive Hackers Guide With Examples
In the previous article, we learned about what is MQTT, what are the topics, and MQTT broker. In addition to

In the previous article, we learned about what is MQTT, what are the topics, and MQTT broker. In addition to
External Entity Injection is a type of security vulnerability that allows the attacker to manipulate the way a web application
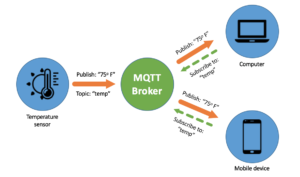
In the previous article, we had gone through IoT Security as an overview. Now is the time to learn about
Before diving into IoT Security, it is important to know what is IoT and why we need it. IoT stands