In the previous article, we had gone through IoT Security as an overview. Now is the time to learn about the protocols that IoT uses for communications. In this article, we will talk about pentesting IoT protocol MQTT by walking through the Pentester Academy labs.
MQTT
MQTT stands for MQ Telemetry Transport. It is an OASIS standard messaging protocol for the Internet of Things (IoT). By design, it is an extremely lightweight publish/subscribe messaging transport. This characteristic makes it ideal for connecting remote devices with a small code footprint and minimal network bandwidth.
This protocol is a set of rules defining how IoT devices can communicate over the internet. It is an event-driven protocol and connects devices with the publisher/subscriber model.
Topics
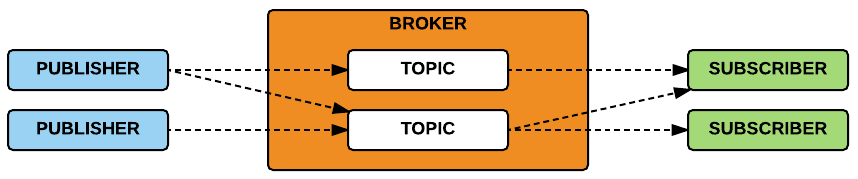
A topic is a UTF-8 string that the broker uses to filter messages for each connected client. The topic consists of multiple topic levels which are separated by a forward slash / indicating the depth of the topic.
The publisher and subscriber communicate via these topics and both are decoupled from each other as well.
The topics beginning with the dollar symbol $ have a special meaning. Thus, these are reserved for the internal statistics of the broker.
Broker
MQTT broker handles the connection between publisher and subscriber. It filters all the incoming messages and distributes them correctly to the subscribers.
Pentesting MQTT
We will walk through the multiple labs to get a better understanding.
Note: These labs require an active Pentester Academy subscription
Broker Recon and Fingerprinting
In this challenge, we will do basic MQTT server recon. The default port at which the MQTT service runs is 1883 and the secure version of it runs on port 8883.
The lab environment has the following topology
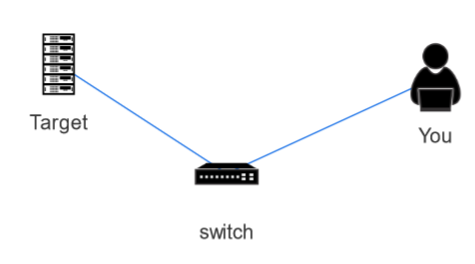
We need to enumerate the target to read the topic values and answer the questions.
Run the lab and you will get a dedicated environment to launch the lab. Navigating to the link gives you a Kali instance with root privileges.
- Is MQTT running on the server? If yes, what is the port for MQTT over TLS?
The target IP is 192.158.97.3 so we will run nmap on it as shown below
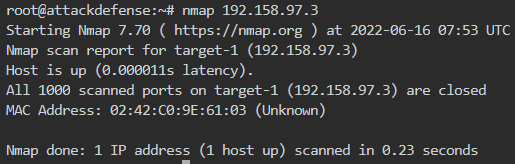
No open port is found and thus no MQTT. This is because nmap by default finds the top 1000 ports and MQTT port 1883 is not in the top 1000. So we need to either scan all ports or explicitly specify port 1883/8883 in the nmap scan command as shown below
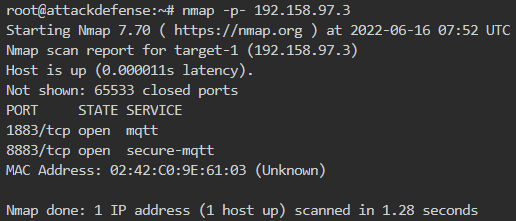
It is clear that the MQTT service is up and running at both insecure (1883) and secure (8883) ports.
- What is the name and version of the MQTT server?
To further enumerate, we check the version of mosquitto (the broker for MQTT) as shown below
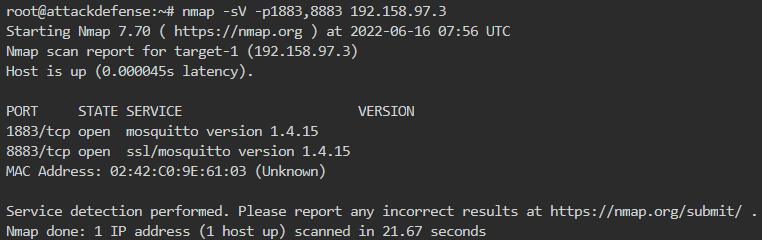
The MQTT is running with broker mosquitto version 1.4.15.
What command can be used to enumerate the MQTT server using the NMAP script?
Now we enumerate using nmap default scripts as shown below
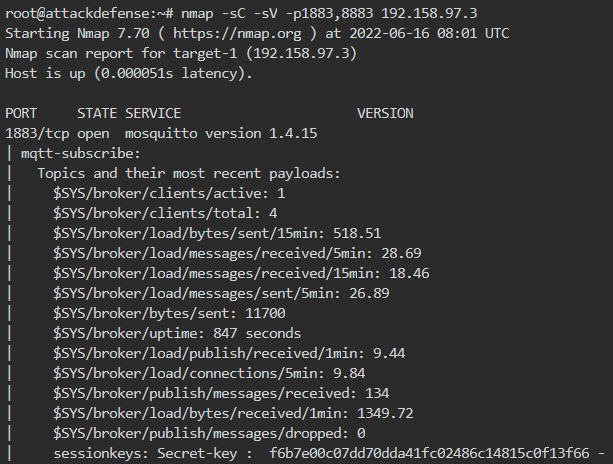
The topics with their most recent payloads are already in the output of the nmap scan. There are many reserved (starting with $) as well as custom topics with some interesting payloads.
What is the welcome message set for the topic “industrial”?
We can use multiple tools to read the topic values. In the nmap output, we can see the topic (industrial) payload as shown below
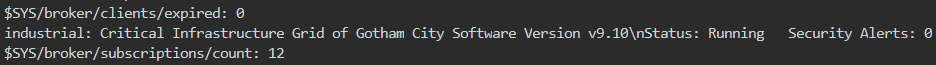
But we will use a tool mosquitto_sub. Its usage is to subscribe to a topic and keep listening to the topic payloads in real time. We can read the welcome message for the topic as shown below
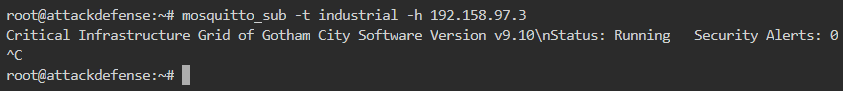
- -t flag specifies the topic that we want to subscribe to
- -h flag specifies the target host
Which topic is being used by the sensors to publish their updates?
We cannot say with surety which topic to subscribe to in order to get the topic name. We have a multilevel wildcard represented by hash symbol # which basically if subscribed, receives all messages sent to MQTT broker. Thus, it gives us all topics and their payloads. So we find the topic used by sensors as shown below
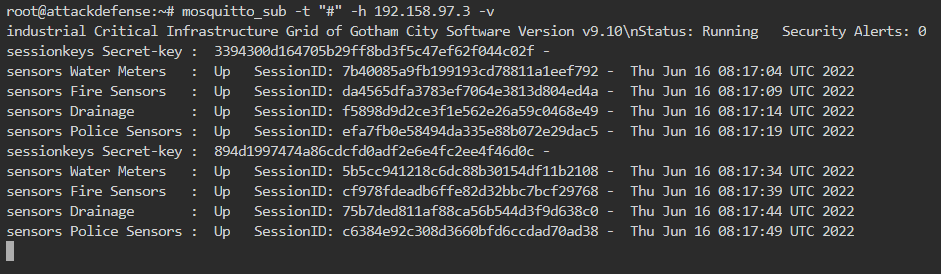
The topic used is sensors
Session keys are being published on a topic periodically. What is the approx time period between the appearance of two consecutive session keys?
The time for session keys publishing is not available. However, we can notice the time delay between the consecutive publishing of the same topic. From the output, it is clear that the topics update every 30 seconds. So, the approx time period between the appearance of two consecutive session keys is also 30 seconds.
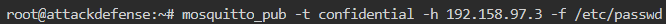
What is the command to post the content of file /etc/passwd to topic “confidential”?
As the usage of mosquitto_sub is to subscribe to a topic. Similarly, the usage of mosquitto_pub is to publish the payload to a topic. We can publish any payload value to the topic. So we publish the file contents to the new topic confidential as shown below
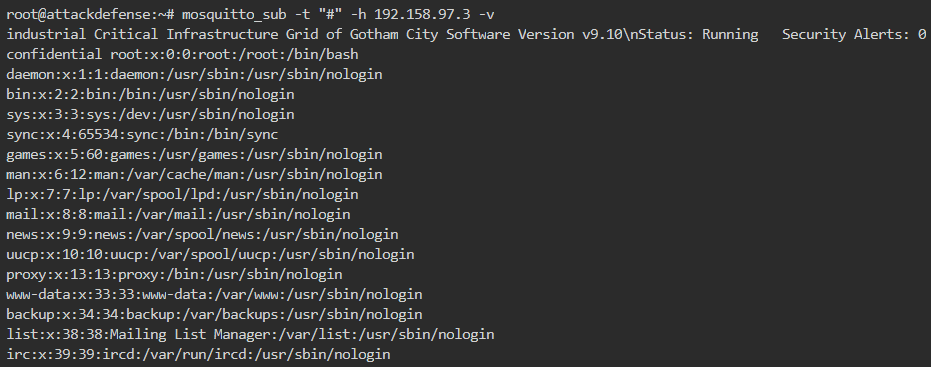
To better see the live results of publishing, we can subscribe to the multilevel wildcard to listen to all messages sent to the MQTT broker. So first subscribe to # and then run the above command for publishing, we will be able to see the live publishing as shown below

Leave a Reply