A botnet is a network of machines infected by malware that lets a central “botmaster” to control them. Botmasters use their botnets for many criminal purposes. Eg, sending spam, launching DDoS attacks, and a slew of other nefarious aims. The botnet is also used to infect more machines, meaning it can make itself bigger and doesn’t always require the botmaster to manually hack more systems.
Botnets are dangerous, complex, and strangely beautiful to study. Like a venomous snake, it’s interesting to see how these harmful systems work and how we can stay safe. In this article, we’ll study botnets in the context of a real botnet map from around the world.
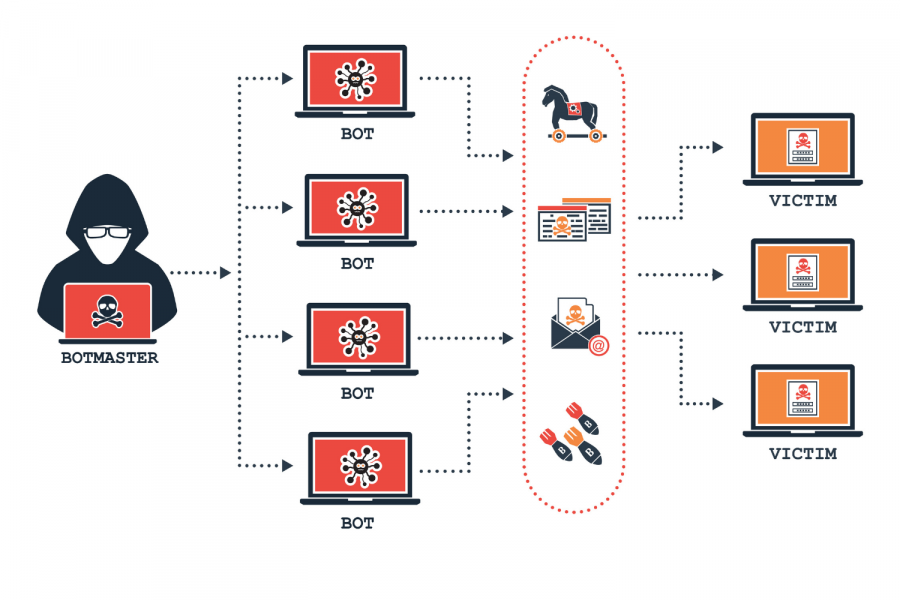
These computers become infected via insecure configurations. For example, instead of using a secure language like Rust, a lot of software still relies on easy-to-exploit C code.
Despite…the rise in the number of new botnet command and controllers (C&Cs) identified by our research team. Despite this increase, our researchers are aware of botnet C&C activity they cannot track due to communications being made via DNS over HTTPS (DoH). This is worrying and certainly tilts the scales in the cybercriminals’ favor.
Spamhaus Malware Team, Spamhaus Botnet Threat Update
Creating our botnet map
But who are these people behind the curtain, with huge botnets? Where are they from, and why do some places have more botnets than others?
Lucky for us, sources like FireHOL provide databases of IP addresses. These IPs are banned. That’s because they run command and control servers for botnets. By mapping these IPs with geolite2, we can see exactly where in the world botnets are running:
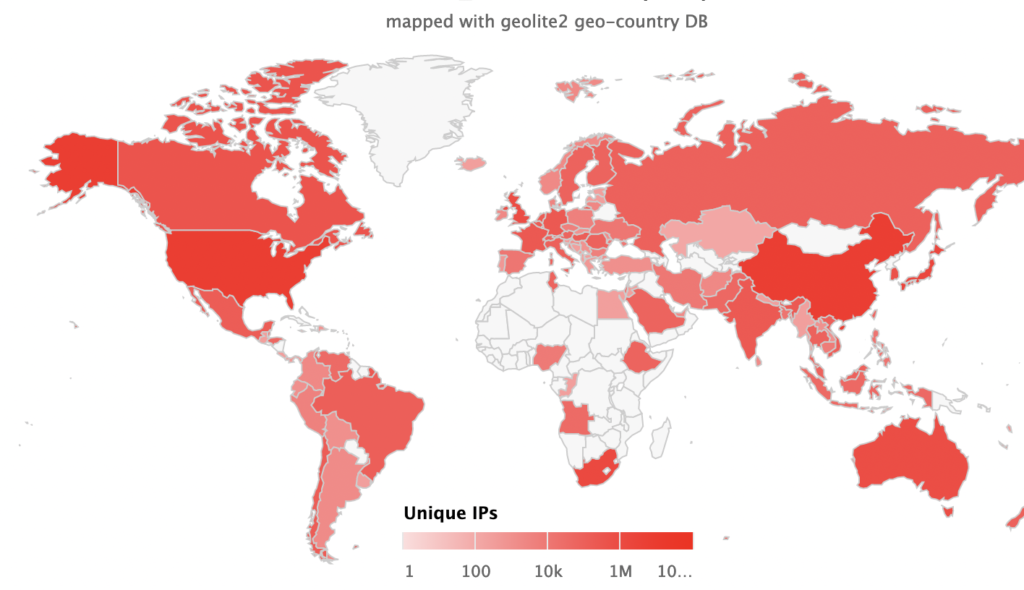
The top three countries appear to be:
- The United States
- China
- South Africa
Why these countries? Hackers often target the US due to the density of wealth found there, making it a prime target for crime. China on the other hand hosts a large population of cybersecurity pros who have government permission to engage in certain hacking activities on behalf of the state. This is similar to the practice of privateering in centuries past. Finally, we see a high concentration of IPs in South Africa. Sadly, this is due to the combination of a highly educated workforce with low economic opportunity. In a very unequal society, this leads to crime within the country. Cybercrime is no exception.
Making your own botnet map?
There are a few fantastic resources for you to collect data about where botnet malware is running. You can even see what it’s doing, and try connecting to the botnet. Exploring live botnets is a core tactic of reverse engineering modern malware.
- Shodan
The easiest way to get started finding and exploring real-live botnets. You can find infected systems on the internet by simply searching “tag:malware” in Shodan’s search engine. However, you’ll need a paid subscription in order to use this feature, so it’s not accessible to the public for free.
Though this one feature requires money, most other Shodan features are free. Thus, if you can figure out a good way to identify malware, you can use that signature on Shodan. This will allow you to find live botnet networks running on the internet, to do with as you wish. It’s a great resource, good luck!
If you don’t want to pay anything, this is what you’ll want to use. The data is completely free and of top quality. It’s good for making maps, but it’s also practical if you’re a sysadmin. Why? Because you can ban dangerous IP addresses from accessing your systems, thus protecting yourself and your team members.
In fact, FilterLists is one of the top resources protecting Fortune 500 networks from malicious origins like botnets. There are even APIs allowing you to interact with FilterLists from the code you write.
Plenty of other tools exist. For example, visual map-making tools like D3.js. As well as data analysis software like Tableau. And the best part is, that most of these tools are free and open source for you to download online. So have fun exploring the thousands of tools and datasets available for your to make malware maps with!
Understanding botnets
Aside from just making a botnet map, let’s also explore the code that drives these botnets very briefly. First, let’s look at the code for a simple botnet malware snippet using Python.
import botnet
import machine
this = machine.infect()
master = botnet.connect(this)Okay, so we’ve got an imaginary snippet showing what a client is doing.
Now we’ll look at the code for the command and control server. This is the program that manages the network and tells infected machines what to do.
bots = listen_for_bots()
c_and_c = listen_for_admin(bots)
run_commands(c_and_c)Maybe you’re thinking, “okay, cool, but this is way to theoretical. I want the real, complete code!”
Good! In today’s security culture, open-source malware that you can study is easy to find. Here’s an open source C&C server written in Python: A Simple C&C Server Written In Python.
There are plenty more that you can find using a quick Google search. I hope this gives you some insight into how these botnets work under the hood.
Conclusion
It’s fascinating to see where botnets come from. But that’s not the only reason we make a botnet map. For lawmakers, it’s a vital window into where in the world new legislation is needed. And for us as security pros, it informs the policies we craft to defend the organizations that employ us.
The botnet landscape is always shifting. If you try this same experiment in a year, you’ll likely get totally different results. That’s a good thing! We need curious engineers to update our understanding. Operating on old data is worse than knowing nothing. The reason is that bad info poisons your results.
Keep playing with data and learning how these systems are operating. Most governments are working hard to fight this problem, as it’s a serious drag on national economies. Yet private firms take the biggest hit, with those expenses finally harming customers via higher prices. By learning where the crime occurs, we can create better strategies for fighting against it.

Leave a Reply