WAScan is an open source web application scanner that performs various penetration testing tasks including fingerprinting, attacking, auditing, bruteforcing, and finding sensitive data leaks. The fingerprinting tasks include web frameworks, content management system, server, operating systems, languages, and web applications firewalls fingerprinting. The attacks performed by WAScan include SQL injections, blind SQL injection, bash command injection, HTML injection, PHP injection, LDAP injection, Xpath injection, XSS attacks, OS commanding, Local File Inclusion (LFI) checks, Server side injection, and Buffer overflow attack. WAScan can audit Apache Status page, open redirect, PHPInfo, Cross Site Tracing (XST), and Robots.txt files. The bruteforce option can be used against admin panels, backup directories, backup files, common directories, common files, and hidden parameters of the target web application. Moreover, WAScan can look for sensitive information like credit card data, Social Security Number (SSN), private IPs, emails, and fatal errors.
WAScan Installation
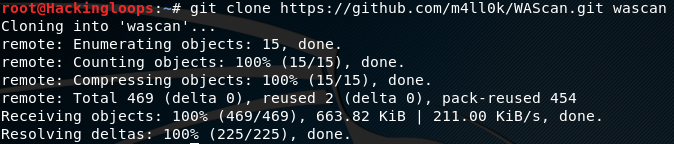
WAScan is a python tool that works best on Linux systems. The latest version of the tool can be cloned from Github source using the following path.
git clone https://github.com/m4ll0k/WAScan.git wascan
WAScan requires BeautifulSoup package to operate. WE can install the package using the following commands.
cd wascan pip install BeautifulSoup
WAScan Working
After successful installation of WAScan, the tool can be launched by running the wascan.py file from the terminal.
python wascan.py
As mentioned, WAScan can be used for fingerprinting, attacking, auditing, bruteforcing, and finding sensitive information hosted by the target web application (information disclosure). The default scanning format is illustrated in the following command.
python wascan.py --url <target web application> --scan <sequence number>
The sequence number in the format is used to define the type of penetration testing task. To launch the fingerprinting task, we set the sequence number to 0. For instance, the following command initiates the fingerprinting utility of WAScan.
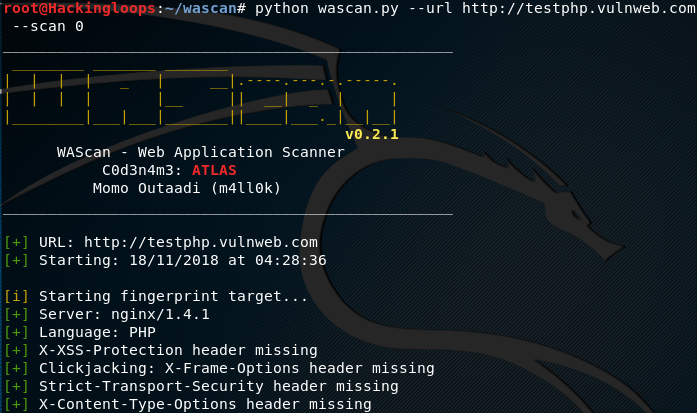
python wascan.py --url http://testphp.vulnweb.com --scan 0
The fingerprint option unveils useful information like target server, programming language, cookies information, and different headers configuration.
We can use WAScan to attack a web application by setting the sequence number to 1, as shown in the following command.
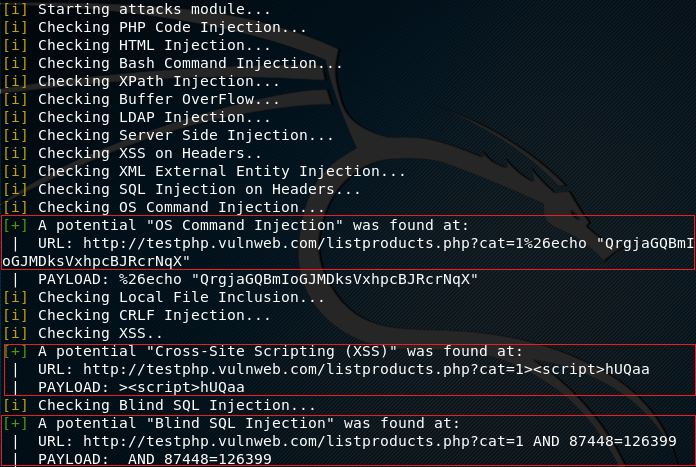
python wascan.py --url http://testphp.vulnweb.com/listproducts.php?cat=1 --scan 1
In the attack mode, WAScan tool launches the attack modules to test if the target web application is vulnerable to any of the aforementioned attacks. Any possible attack is shown in the results along with the vulnerable paths as shown in the following screenshot.
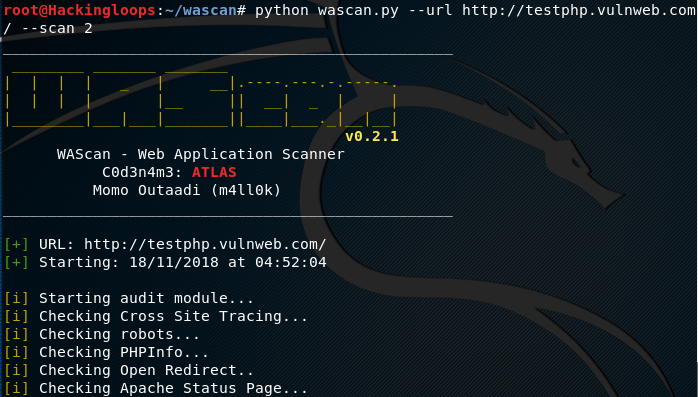
WAScan audits the target web application in the following format.
python wascan.py –url http://testphp.vulnweb.com/ –scan 2
We can use WAScan to bruteforce the target web application by setting the sequence number to 3. Sequence number 4 is used to find the possibility of disclosure of sensitive information like credit card data and Social Security Number (SSN). We can also run WAScan to perform all the tests (fingerprint, attack, audit, bruteforce, information disclosure) in a single scan by setting the sequence number to 5.
python wascan.py --url http://testphp.vulnweb.com/ --scan 5
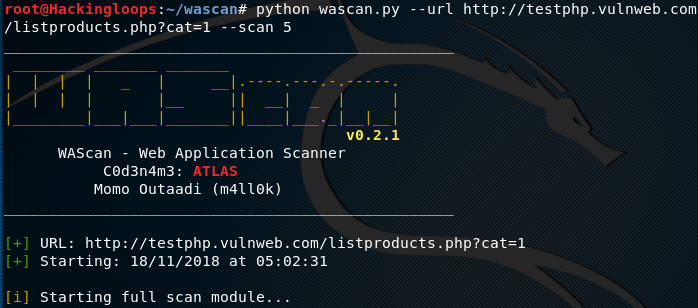
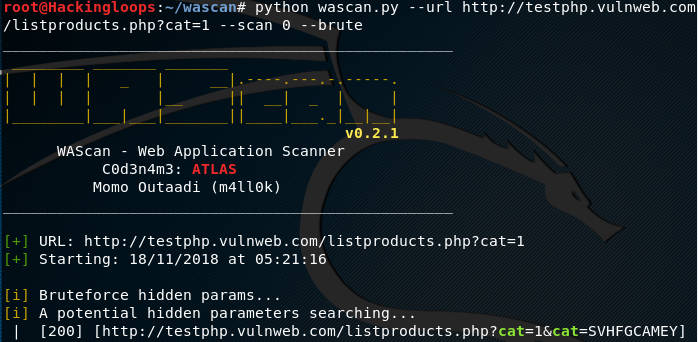
WAScan also allows different parameters to be used in combination with the default attack options. For example, we can apply the –brute parameter with the fingerprint scan option in the following format.
python wascan.py --url http://testphp.vulnweb.com/listproducts.php?cat=1 --scan 0 --brute
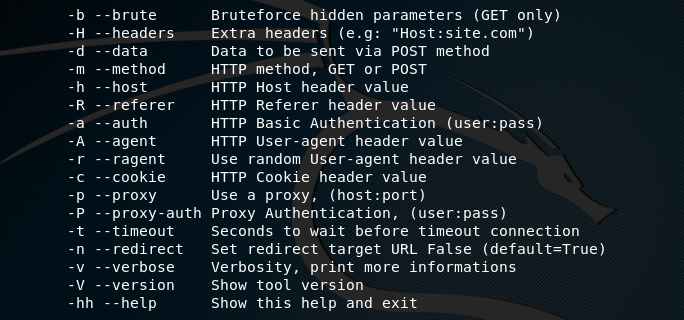
The complete list of parameters can be viewed in the help section.
python wascan.py --help
Conclusion
WAScan is a semi-automated web application scanner that can be used for information gathering and attacking purpose. The tool is capable of finding bugs in web applications that can lead to different cyber-attacks like SQL injections, cross site scripting, OS commanding, and server side injections.

Leave a Reply