As we know that there are two types of Cross Site Scripting namely Reflected Cross Site Scripting (Reflected XSS) and Stored Cross Site Scripting (Stored XSS). In our previous articles we have learned about Reflected XSS and how does it works. Today we will learn about most dangerous type of Cross Site Scripting attack i.e. Stored Cross Site Scripting. Web applications which allow users to store data are usually exposed to Stored Cross Site Scripting.
Stored Cross Site Scripting or Stored XSS usually occurs when a web application (say website) takes input from a user via some web forms (usually input forms for example, shopping cart, Forum, contact page, user or profile pages, blogs, settings page etc i.e. from where application accepts data and store it into database) and user injects malicious code into it, and the field in which user has entered the malicious code is not validated correctly and data is stored in some database for future use. As a result, the malicious data inserted by hacker appears to be part of the website or web application and runs in victim’s web browser (as per privileges set for web application) and it can result into complete hold over victim’s machine based on the arbitrary code inserted by the hacker. Likes we studied in Reflected XSS, an XSS attack allows hackers to install browser based Keyloggers, steal session cookies or sensitive information or change data on the web page usually download links etc.
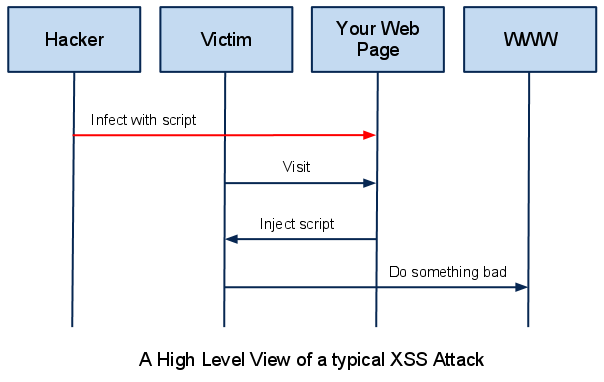
In case of Stored XSS, there is not need of exploiting a malicious link. An exploit automatically triggers when any user visits the web page containing stored XSS. We can define a typical Stored XSS attack in below steps:
- Hacker identifies the vulnerable website which asks for data from user and stores it into website database.
- Attacker injects the arbitrary code into the vulnerable page.
- User visits the vulnerable page on website which contains the Stored XSS.
- Arbitrary or malicious code is executed by the user’s web browser.
This is how stored XSS attack works. Now below are after effects that a hacker can achieve after successful XSS attack:
- Hijacking User’s Web browser
- Install JavaScript or vbscript browser based Keyloggers to capture key strokes of victim.
- Capture sensitive information of the users visiting the vulnerable website like session cookies etc.
- Can deface website
- Redirect users to other malicious websites.
- Changed download links and expose users to download other malicious software’s like Rat’s, Trojans, Keyloggers etc.
Stored Cross Site Scripting attack can be exploited using various browser based exploitation frameworks available online like XSS Proxy, Backframe, BeEF etc.
That’s all for today! We will learn Stored XSS in detail with help of practical examples in later tutorials, so keep connected.

Leave a Reply