The demand for Cybersecurity professionals has increased tremendously over the past few years. Various Cybersecurity surveys indicate that the number of unfilled Cybersecurity positions can reach up to 3 million by 2022. Lack of desired Cybersecurity skills is one of the main reasons of the vast gap between supply and demand of qualified Cybersecurity professionals. Whether you are an expert or rookie Cybersecurity professional, you always need a test-bed like Kali Linux Virtualbox or VMware Pentest lab for practicing and mastering the evolving methodologies of Cybersecurity. Normally, demo applications are used in such environments to simulate the attacks. These applications are either remotely hosted or cloned on a local machine. This tutorial is about setting up vulnerable web applications on a local host for experimenting penetration testing tools and tricks in a legal environment.
Damn Vulnerable Web Application
Damn Vulnerable Web Application (DVWA) is designed to apply web penetration knowledge on a deliberately vulnerable application with many security flaws. The idea behind DVWA is to assess your web penetration testing skills for various web attacks, such as SQL injection, Cross-Site Scripting (XSS), command injection, brute-force, file inclusion, file upload, session hijack, and Cross-Site Request Forgery (CSRF) attacks.
How to Setup DVWA on Local Host?
To setup DVWA on a Linux machine, we need to clone the source files using the following command.
git clone https://github.com/ethicalhack3r/DVWA
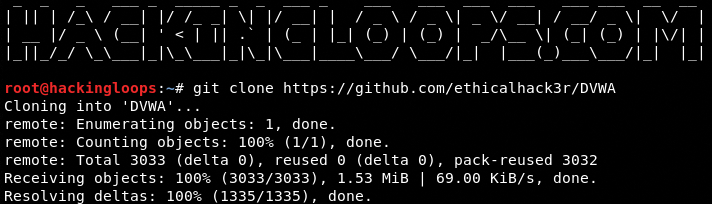
Since we are using the Apache server in Kali Linux, we need to move the DVWA package to the /var/www/html/ location to make it work.
mv DVWA /var/www/html/
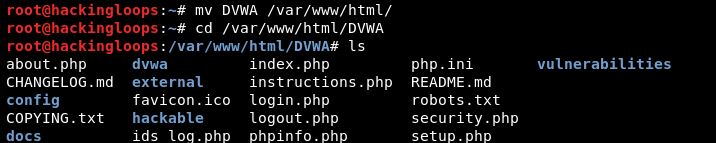
Start the Apache server using the following command.
service apache2 start
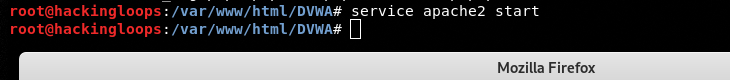
Navigate to the /DVWA/config folder and rename the config.inc.php.dist file as config.inc.php.
mv config.inc.php.dist config.inc.php
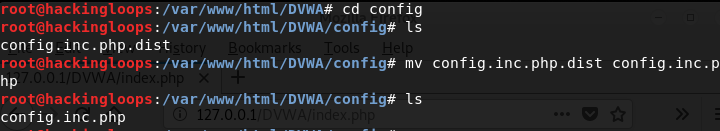
The DVWA folder contains different setup files including index.php. Open a web browser and execute the index.php file using the localhost address.
127.0.0.1/DVWA/index.php
The above command automatically takes you to the 127.0.0.1/DVWA/setup.php page as shown below.
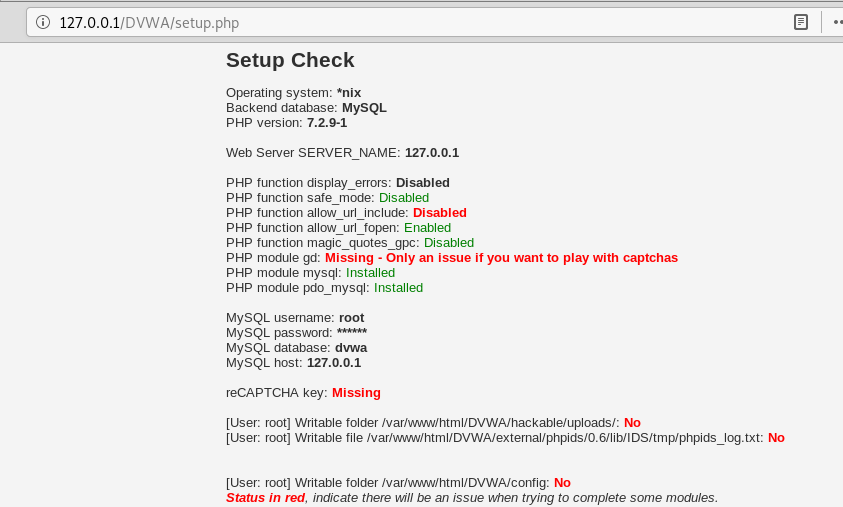
The first step after reaching this page is to look for the database error.
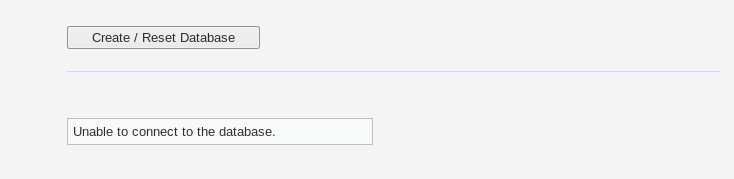
If there is any database connection error mentioned at the bottom of setup.php page, start the MySQL service using the following command.
service mysql start
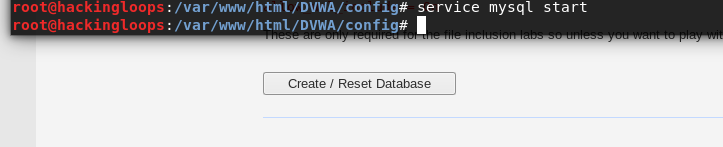
After running the MySQL service, navigate to the setup.php page and click on the [create/reset database] tab to see if the database connection is fixed. If there is no database error, the page automatically navigates to the DVWA admin page. Use the following credentials to log in and explore all the DVWA vulnerabilities.
Username: admin
Password: password

Since we are using MariaDB instead of MySQL database, we get the following error.
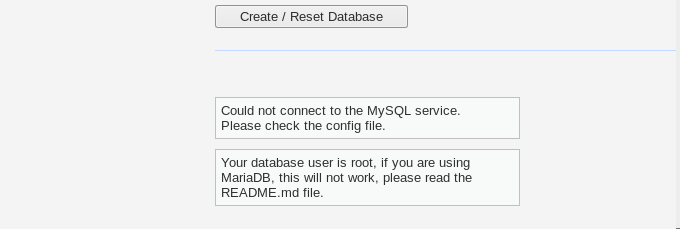
Typing mysql in the terminal confirms that we are using the MariaDB database.
mysql
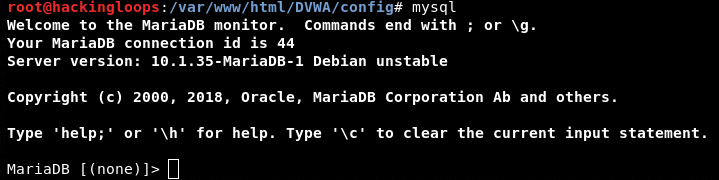
The following command changes the database from MariaDB to MySQL.
use mysql
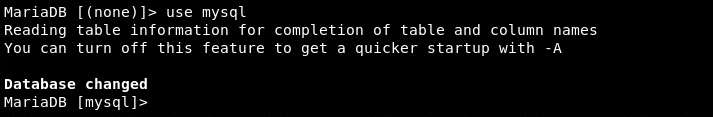
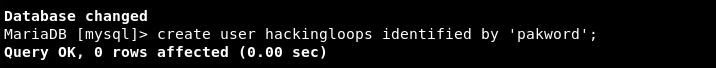
Create a new database username and password using the following command.
create user <username here> identified by ‘<password here>’
We have created the following user and password for the database configuration file.
username: hackingloops
password: pakword
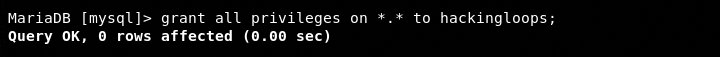
Grant the privileges to the newly created username by typing the following commands.
grant all privileges on ‘,’ to hackingloops flush privileges
Now open the config.inc.php file using any editor and update the database credentials as shown in the following screenshots.
leafpad config.inc.php
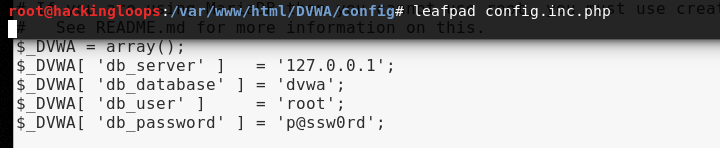
Updated Database Credentials
The aforementioned update should fix the database error by displaying the DVWA admin page. Sign in to explore all the test vulnerabilities as shown in the following screenshot.
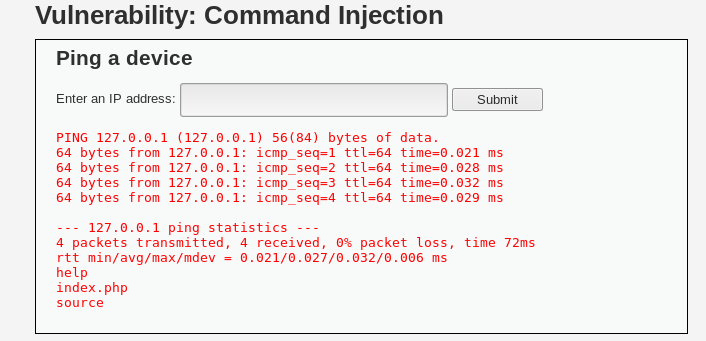
For example, we can assess command injection vulnerability in an application by passing additional arguments to the command, separated by semi-colon (;) . In DVWA, we can simulate the attack by trying to list the files using the ping and ls command together.
127.0.0.1;ls
The injection successfully lists the additional files along with ping response as shown in the following screenshot.
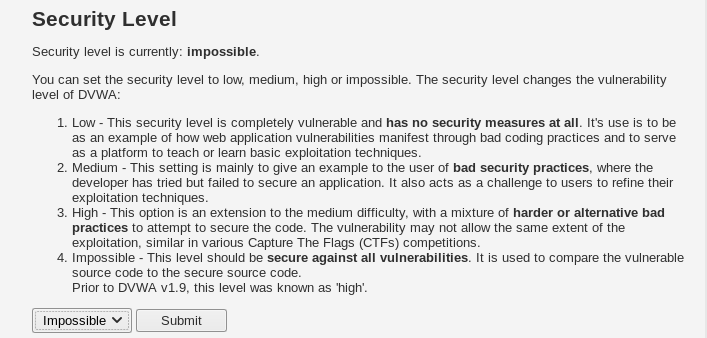
The DVWA has four different security levels to rank your penetration testing skills. Newbies can start with low-level vulnerabilities whereas the experts can use their expertise to solve the highest “impossible” challenges.
Damn Vulnerable WordPress
Damn Vulnerable WordPress (DVWP) application contains WordPress-related vulnerabilities and exploits. Penetration testers can practice the WordPress scanning and exploitation techniques in a safe environment by setting up the DVWP on a local machine.
How to Setup DVWP on Local Host?
Setting up DVWP on a local machine requires the Docker installation of the application. Clone the DVWP source files using the following command.
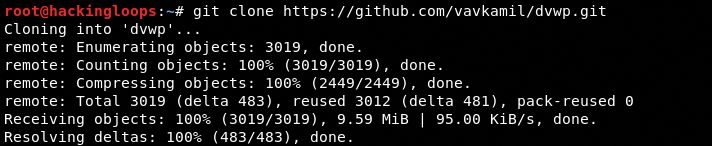
git clone https://github.com/vavkamil/dvwp.git
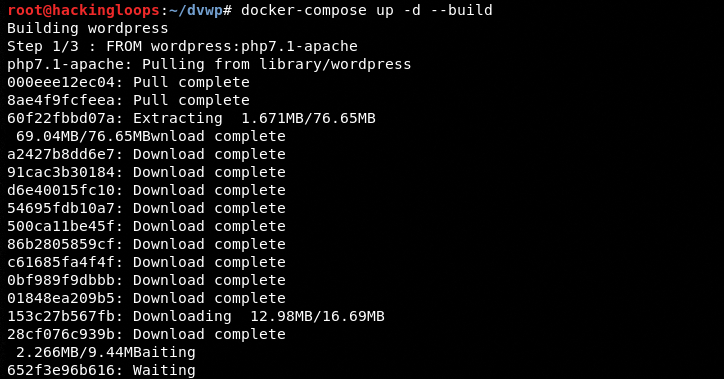
Navigate to the package directory and run the following Docker commands.
cd dvwp docker-compose up -d --build
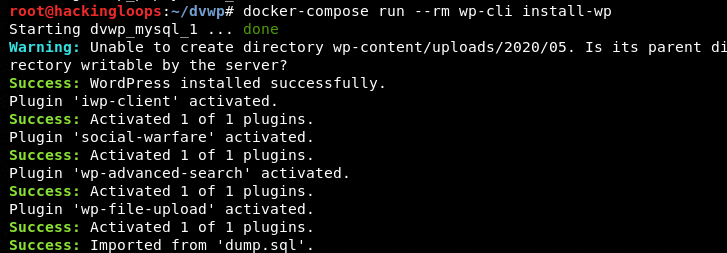
docker-compose run --rm wp-cli install-wp
When the installation process is finished, run the localhost IP address at port 31337 in a web browser to start the vulnerable WordPress application server on the localhost. The same address can be used for practicing scanning and exploitation techniques.
127.0.0.1:31337
The following administrative credentials can be used to log in to the DVWP. The application allows tweaking certain admin settings to meet the penetration testing requirements.
Admin URL: 127.0.0.1:31337/wp-login.php
Username: admin
Password: admin
Damn Small Vulnerable Web
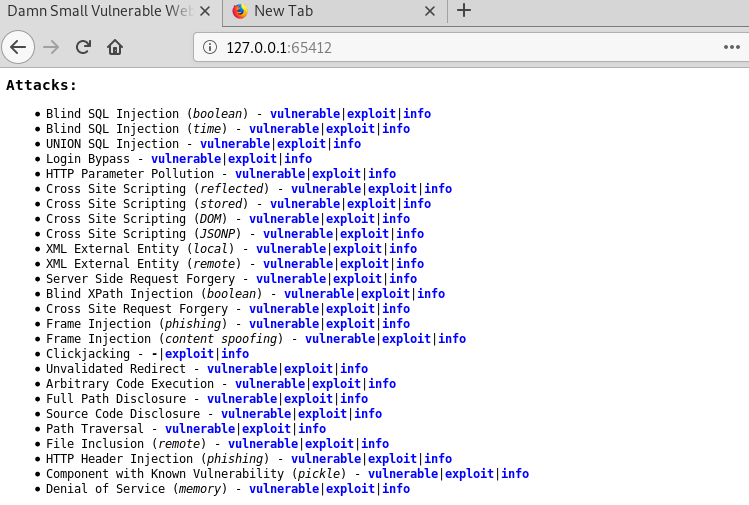
Damn Small Vulnerable Web (DSVW) is another web application that can be used to simulate various web application attacks. The DSVW has a number of vulnerabilities including SQL injection, XSS, Frame injection, path disclosure, directory traversal, and clickjacking.
How to Setup DSVW?
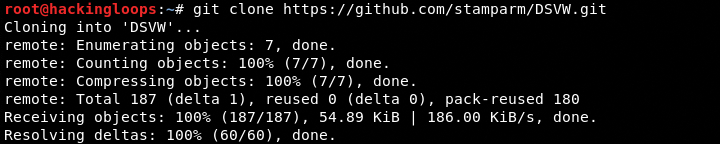
The DSVW can be cloned from Github using the following command.
git clone https://github.com/stamparm/DSVW.git
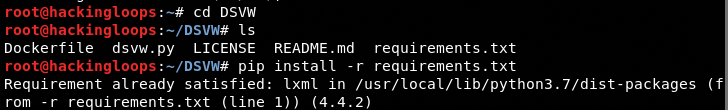
Navigate to the application’s directory and execute the following command to install the DSVW requirements.
cd DSVW pip install –r requirements.txt
After installing the requirements, start the DSVW server by executing the following command.
python dsvw.py
The DSVW server runs on localhost at port: 65412.
The server shows all the supported web vulnerabilities with a unique URL. Each URL is an attack vector for certain exploits.
127.0.0.1:65412
Conclusion
Targeting live applications for practicing and testing purposes can be harmful and illegal in some cases. The best approach is to use the demo applications. Online web applications like webscantest.com, testphp.vulnweb.com, and testasp.vulnweb.com can be used for this purpose. However, there are certain scenarios where we want to run the penetration tests on locally hosted applications. In such cases, we can use web applications like DVWA, DVWP, and DSVW.

Leave a Reply