Dracnmap is a network exploitation and information gathering tool. The type of information that can be gathered with the help of Dracnmap includes hosts status (up, down), ports status (open, closed, filtered), running services, OS version information, firewalls information, traceroute results etc. Dracnmap has an advanced script engine used to (target and) identify vulnerabilities related to networks and web applications. The scripts are divided into different categories including authentication, broadcasting, bruteforcing, malware, exploitation, vulnerabilities, and fuzzing categories. These scripts can be applied according to the nature of target (networks or web applications). Dracnmap has a dedicated set of web application functionalities to find out Web Application Firewall (WAF) information, detect open relays, collect WHOIS information, enumerate users in SMTP servers, track IP Geo-location, and detect vulnerabilities like backdoors, SQL injections, Cross site scripting, Cross Site Tracing (XST), and Denial of Service (DoS) attacks.
Dracnmap Installation
Dracnmap requires Nmap to function. Nmap can be installed by cloning the tool and running the following installation commands.
git clone https://github.com/nmap/nmap.git ./configure make make install
After installation of Nmap, clone Dracnmap using the following command.
git clone https://github.com/Screetsec/Dracnmap.git
Navigate to the Dracnmap directory and make the dracnmap.sh (dracnmap-v2.2.sh) file executable.
cd Dracnmap chmod +x dracnmap-v2.2.sh
Running Dracnmap
Dracnmap tool can be opened in command line interface (cli) by running the executable (dracnmap-v2.2.sh) in the terminal.
./ dracnmap-v2.2.sh
The command opens the tool menu shown in the following screenshot.
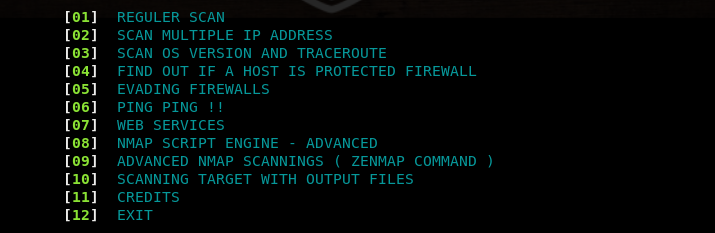
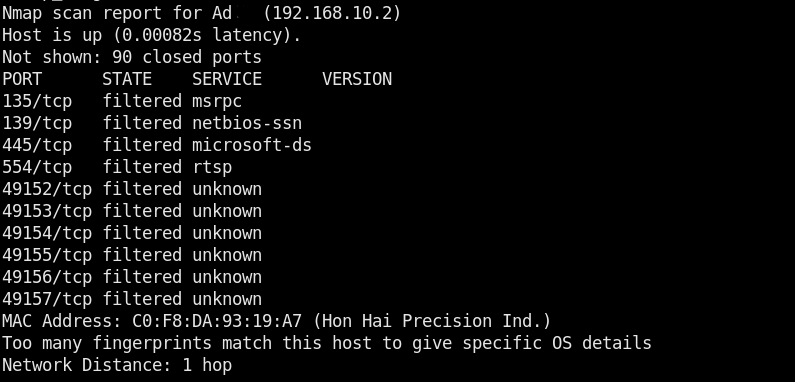
The menu is a list of utilities to perform the aforesaid penetration testing tasks. Each utility can be selected by typing its sequence number in the command line. For instance, we can select the Operating System (OS) scanning option by typing its sequence number (#3) in the command line. The tool asks for target IP address or hostname to scan the target. The OS scan results are shown in the following format.
Advanced Nmap scanning is one of the important features of Dracnmap tool. The advanced scanning utility has the following list of scanning options.
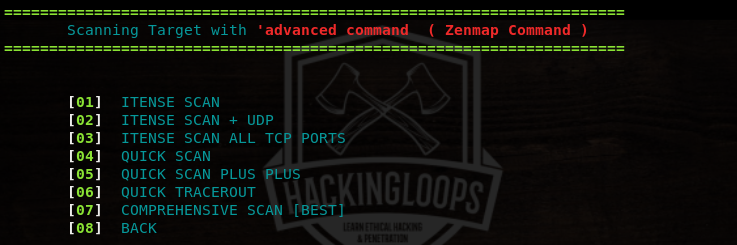
The advanced scanning offers quick and comprehensive scanning modes. The quick scanning mode gives information about open ports and the associated services. The comprehensive mode gives detailed results as compared to the quick mode. The advanced scanning also features traceroute function to find out the distance (hops) between the host and the target.
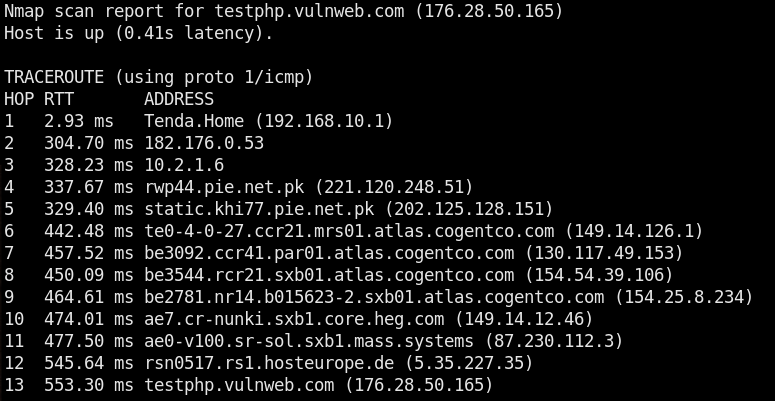
The nmap script engine contains the following list of categories to perform vulnerability checks. Each category has a set of scripts that can be tested against the target host

The exploit category has the following list of scripts that can be used to analyze the security of target host against various threats.
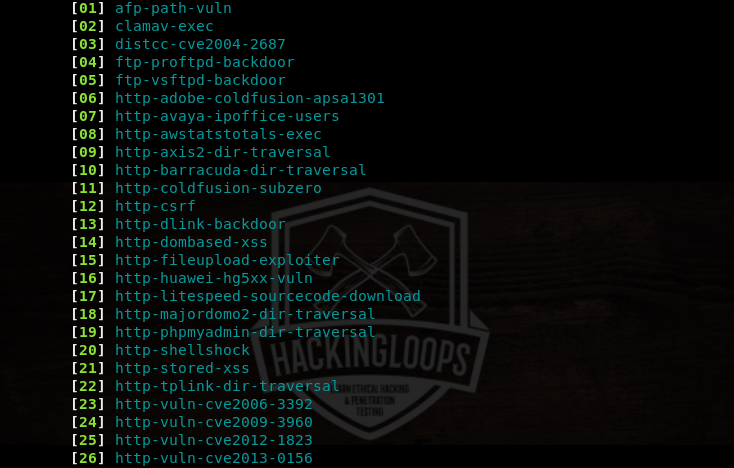
For instance, Remote File Inclusion (RFI) and Local File Inclusion (LFI) are common file upload vulnerabilities. We can check the security of target application against file upload vulnerabilities by executing the http-fileupload-exploiter script from the list.
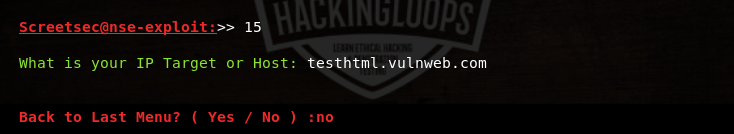
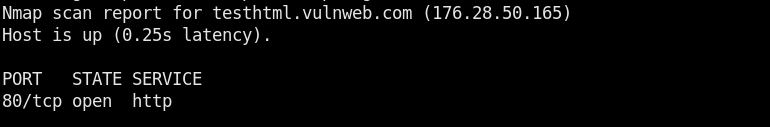
The tool checks if the target host is up and the target port is open for file upload test. If file upload is successful, the the details are added in the results.
Similarly, the following screenshot shows the list of scripts in the broadcast category.
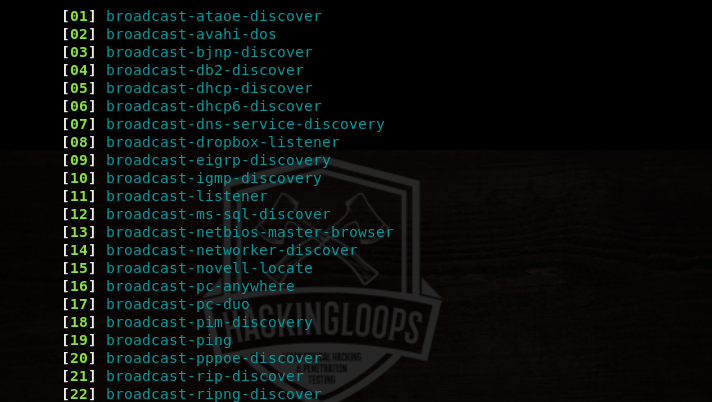
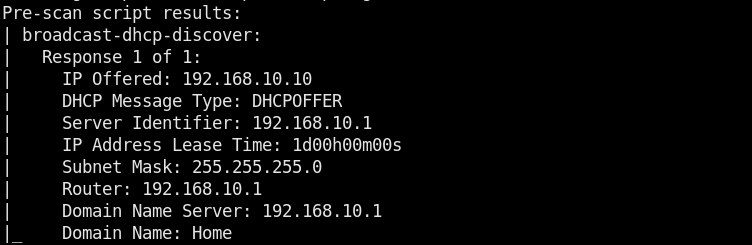
If we select the broadcast-dhcp-discover script from the list, the tool gathers DHCP information as shown below.
The web services of Dracnmap contain the following information gathering and vulnerabilities canning options.
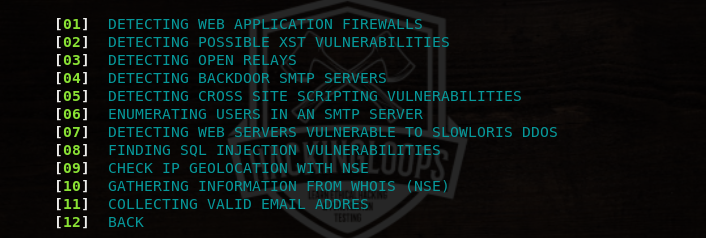
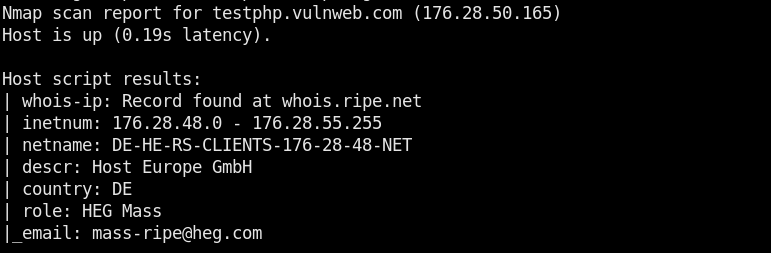
For instance, we can select the WHOIS utility by typing its sequence number (#10) in the command line. The WHOIS data is displayed in the following format.
Conclusion
Dracnmap resolves the complexity of Nmap tool by dividing its features into different categories. Each category contains specific options that automate the penetration testing process.

Leave a Reply