Information gathering is the foundation to the web-security testing pyramid. A stronger foundation (wealth of information) means less difficulty in staging the next phases of the penetration testing cycle. However, web application firewalls and Cloudflare-like technologies make the web information gathering process difficult. There are only a few tools with the ability to bypass these security challenges and get the desired in-depth information. In this article, we shall analyze the Eazy tool that claims to provide the desired web information along with vulnerabilities assessment features.
The Eazy tool is loaded with multiple information gathering and vulnerabilities assessment modules. Each module is a standalone utility maintained by different developers. The information-gathering modules are dominant as compared to the vulnerabilities’ auditing modules. The Eazy tool’s information-related modules can gather the following important information with good accuracy.
- WHOIS record
- Ports information
- Subdomains results
- Directory search
- External links finding
HOW TO GET EAZY TOOL?
The Eazy tool is a combination of Python modules that can be downloaded from Github using the following command.
git clone https://github.com/devcrax/Eazy
All the modules’ scripts come pre-packed with the cloned Eazy directory.
HOW TO MANAGE EAZY TOOL?
The Eazy tool can be operated from the core Python file in the package. Navigate to the tool’s directory and run the (Eazy.py) file using the following command.
cd Eazy python2 Eazy.py
The above command opens the Eazy terminal to run Eazy modules scripts and get the results. We can get an overview of all the modules using the help command.
help
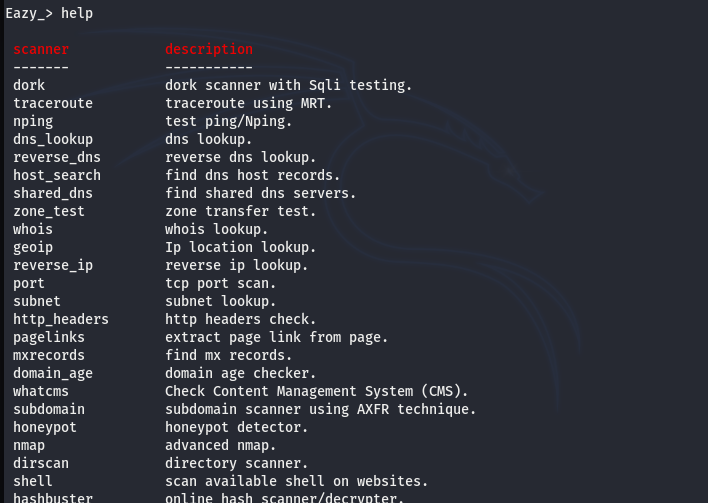
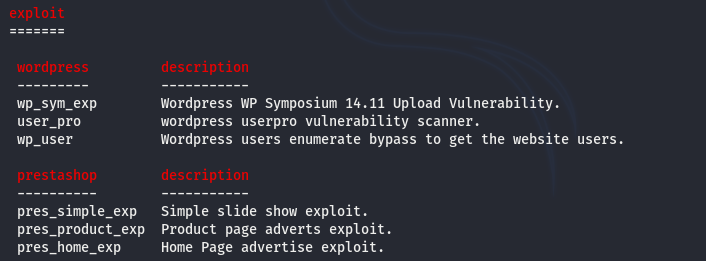
Apart from the aforementioned modules, there are some exploitation scripts related to WordPress and Prestashop technologies.
WHOIS RECORD EXAMPLE:
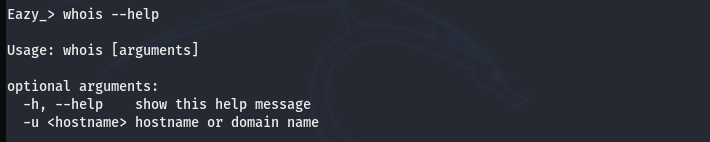
Information gathering with the Eazy tool is pretty simple. We can type the module name and –help argument to get the syntax for each command. For example, we can see the command structure and supported arguments for the WHOIS module using the following command.
whois --help
We can use the WHOIS module with the following command syntax to get the domain information.
whois -u <target URL>
For example:
whois -u webscantest.com
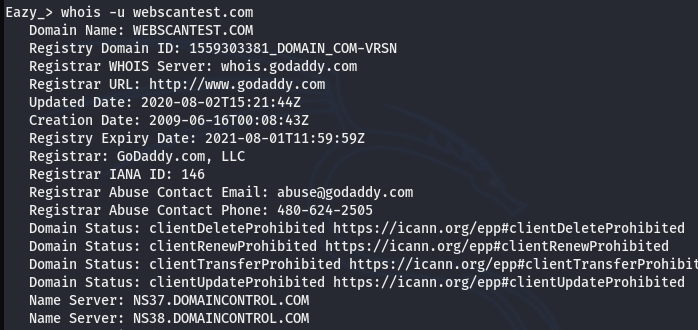
The above screenshot shows all the important domain-related passive information that can help penetration testers in narrowing down the enumeration and attack schemas.
BRUTEFORCE ATTACK EXAMPLE:
Some of the Eazy tool modules rely on the brute-force technique to fetch the results. The tool has a built-in wordlist directory with some decent wordlist files as shown in the following screenshot.
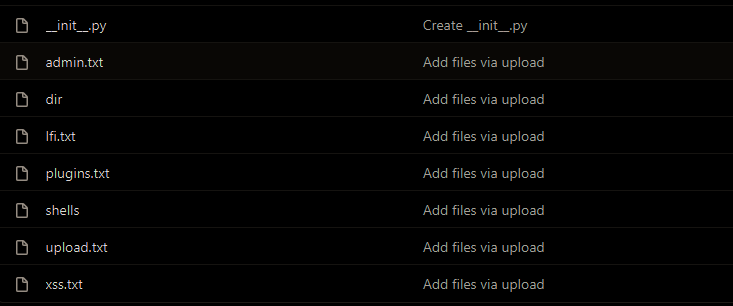
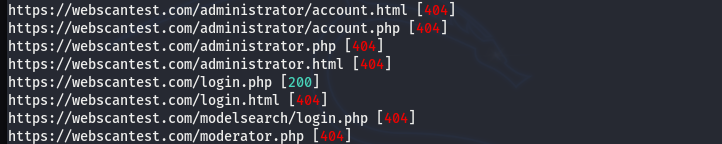
These wordlists can be manually updated with the latest keywords to get the best brute-force results. We have tested the existing wordlist files for the Admin console finder and Directory search module. The admin module wordlist consists of 4K+ entries. The module managed to find the existing admin panel on the target web server in a few seconds.
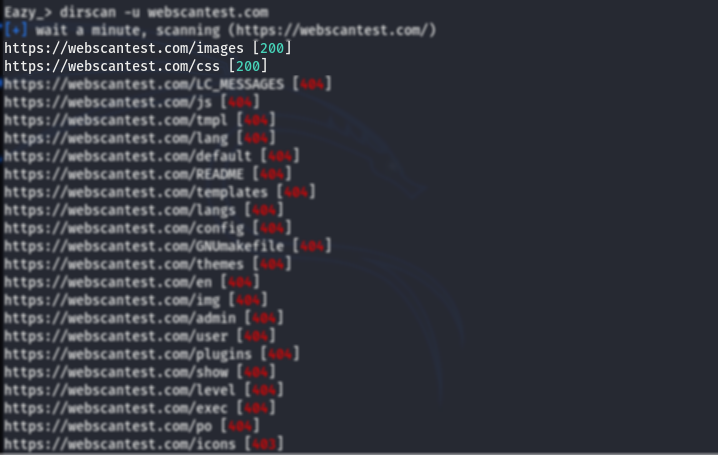
The directory scan results were also satisfactory.
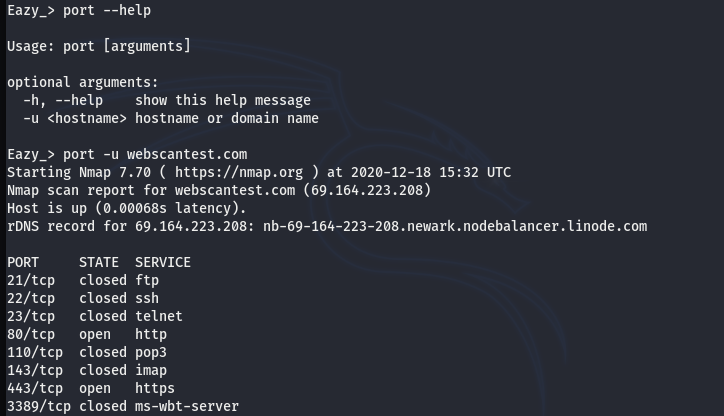
PORT SCAN EXAMPLE:
Port scanning is one of the critical penetration testing tasks as it gives an insight into different possible entry points for the target web application. The Eazy port scanner utilizes the Nmap services to find all the open ports and the associated services using the SYN scanning mode.
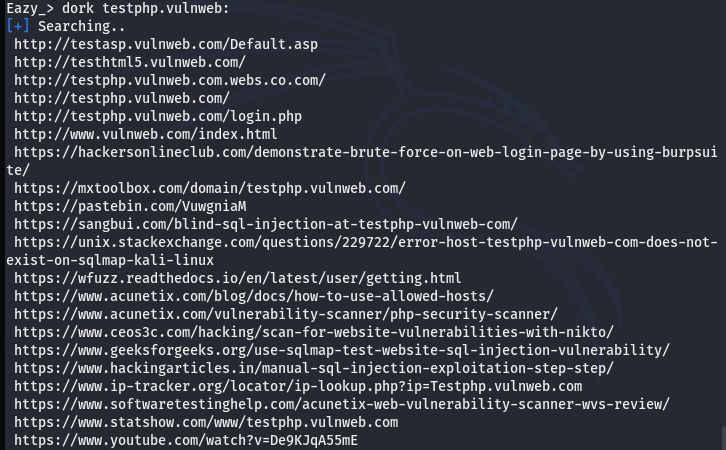
Eazy DORK EXAMPLE:
Dorking is a technique used to find information that is kept hidden from the public for security reasons. Security researchers use the technique to find the web flaws that are vulnerable or exploitable. Though the Eazy dork module is not as efficient as some other dedicated dork frameworks, the tool gives decent results for target strings or keywords.
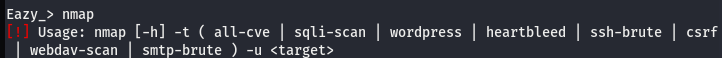
NMAP EXAMPLE:
Nmap is a key integrated module in the Eazy tool. We can use the Eazy-Nmap utility for the following information and vulnerability assessment tasks.
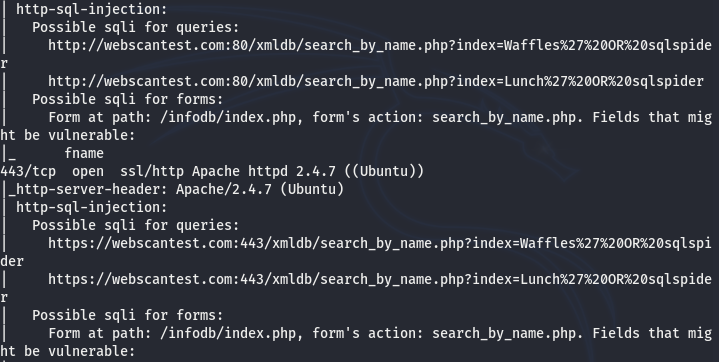
We have tested the Nmap-SQLi feature. The module managed to find some links on the target web domain that is vulnerable to SQL injection.
MISCELLANEOUS EXAMPLES:
Besides the aforementioned modules, there are many other modules that can be used to get useful web information. For instance, we can use the page link module to grab all the outgoing links on a target web page.
WordPress and Prestashop-related modules can be used to find CMS-related vulnerabilities.

CONCLUSION
Eazy framework is a decent collection of information gathering modules. Though there are some security audit features, the tool lacks the ability to be used as a standalone vulnerabilities analyzer. The available vulnerability scanner modules support only WordPress and PrestaShop CMS with very limited scope.

Leave a Reply