“How to get a security clearance” is one of the most asked questions we get. This article will answer most of those questions.

It is important to learn when and how to take your career to the next level in the cybersecurity and IT professional sector. If the job takes you in a position where security clearance is needed, chances are the industry you’ll be working in is critical infrastructure. It may be pretty challenging to achieve the clearance, and on top of that, it is not a permanent fiat.
A single question can’t answer everything you need to know, hence we filled the most asked questions with proper information. Let’s go through the details.
Table of Contents
- What is a security clearance?
- A brief history
- How to get a security clearance?
- Understanding the needs
- Understanding the types
- Going through the investigation levels
- Receiving the certificate
- EndNote
What is a security clearance?
A security clearance is a serious matter involving federal and private employees who need proper access to high-level data. It can access forbidden and higher access level data in secure facilities. Even safety personnel have an allowed level where the data is physically or digitally held.
Not every position needs a security clearance, but those with sensitive information handling do. There are about three million employees who have security clearance at a given time in the US. Security clearance has many levels, which we will discuss further in another point below.
According to research, one of every thirty Americans has some sort of security clearance. On top of it, estimation says that one out of a thousand who have security clearance may compromise the secretes entrusted. So, we can see what kind of motivation and value security clearance upholds.
Security clearance levels vary from employer to employer. A computer engineer in a company may have some level of security clearance, whereas a digital forensic expert has a much higher level of government clearance due to their work. We think that only government employees require a high-level security clearance, but that is not the case. Even government bodies collide with private sectors, and employers there require similar levels in these cases.
Among the three million clearances at the given time we mentioned, half of them belong to private contracting or consulting firms. Defense Counterintelligence and Security Agency (DCSA) administrates the program on behalf of the Department of Defense and 33 other federal agencies to give it out on a contractual basis. A typical clearance is issued by the Federal Government and similar higher authority bodies.
A brief history
Since 1972, the security clearance process has changed significantly as the US government underwent tremendous changes. The history is long and complicated, but we can point out the accomplishments. Certain milestones and focus words may shine some light on the idea.
There is no single government body that handles a “Yes” or “No” on security clearance. Dozens are working at their own pace and standards to go through the protocols. Most of the time Office of Personnel Management (OPM), as the Investigation Service Provider (ISP), handles the situation of accepting or denying the applications. 85% is conducted by Personnel Security Investigations (PSIs). These investigations are not only on private employees whose employer granted permission to seek the certificate but also on federal employees, contractors, and military personnel.
- In 1972, security clearance for armed forces (Army, Air Force, Navy, Marine Corps, DoD) was given to the Defense Investigate Services (DIS). DoD had 18 Central Adjudication Facilities (CAFs) that were later reduced to 9.
- In 1972, DIS grew from 800 to over 2,500 field investigators as the need for people with security clearance increased. In early 2000, DSS (Defence Security Service) started to shift PSIs. The JSSRT (Joint Security and Suitability Reform Team) began revamping the framework.
- January 2009, Executive Order 13488 started providing public trust individuals security clearance.
- 2013, a 105-day moratorium took place, causing a delay for the first three weeks of October.
- In July 2015, POTUS directed a 90-day review period for the OPM data breach.
- 2018, DoD appointed Charles Phalen, former NBIB director, as the director of DCSA.
- May 2020, the Defense Counterintelligence and Security Agency (CISA) noted that the security clearance backlog is down to 180,000. These take a processing time of up to 119 days for the Top-Secret category and 65 days for Q2. Special thanks to ClearanceJobs for the valuable information on the history.
A lot happened between then and now. It would take a history book to mention almost everything. Even today, getting a security clearance can drive unexpected events as the critical infrastructure needs much thorough investigation before granting access.
How to get a security clearance?
Before getting a security clearance, we must ask ourselves “when” to get a security clearance before the “how.” The process unveils quite naturally when it is time to get the certificate. There should be a verifiable need to obtain a clearance. Companies, the military, or the federal government grants access to those who need security clearance for the job purpose.
An extensive background check takes place before the green signal. Obtaining a security clearance can be simple for straightforward candidates but can pose complications or limitations when papers are not in order. Upon filling out the forms, your background checks will begin. Investigators will check them, and data will be verified by law enforcement agencies.
According to Executive Order 10450 (requirements for government employment), the American tradition supports person should receive “fair, impartial and equitable treatment at the hands of the Government.” So we can’t justify that everyone with a need will get it. The Government will decide how to handle the situation. The head of each government department agency will be responsible for “establishing and managing” the details.
As the need for allowance grows, so is the time to execute a proper procedure. They are eligibility issue, information sampling, investigation, requirement fulfilling, paper processing, special approval, and many more that goes into a simple “approval!”
On the other hand, the candidate may further speed up the process if they feel like the approval will benefit them if received as soon as possible by following every government rule. But it is pretty impossible to get a security clearance before the initial job offer and background investigation, no matter how serious your concerns are. It is different for individual applications to obtain a security clearance. Let’s go through a few critical notes.
Understanding the needs
Even if most of us try to get a security clearance for interest and go through files that may uncover exciting information, most of us will not get the opportunity. But luckily, if the job demands a background check and clearance, there is no saying you’ll get the chance. At a professional level, where opportunity can bring advancement in your career, getting a security clearance means you’re on the right track. But we are not here to guide towards career advancements with other information rather than circulating security clearance as on Hackingloops. We have tons of articles covering them.
A security clearance is for someone that worked in an organization long enough that they are trusted with core & sensitive information. This information’s restricted from employees and other high-level officers. Military and federal officers are the biggest targets for security clearance. But the clearance certificate does not have a lifelong expiration date as their access is revoked at the end of their career. Over 200,000 military personnel transition into the service each year, and a sizable batch is given the clearance. They perform defense-related tasks, set up plans and workforce, and other technical curriculums.
Not only do the military or federal service holders get a security clearance, but also education, telecommunication, financial services, and medical fields have jobs that require high-level access to security. These posts are recommended by HR and the top management who decide to a conclusion.
Understanding the types
Among the different types of security clearances, here are three primary ones:
Confidential
It is a material-level security clearance given mostly to military and federal employees. Confidential is the most basic level that needing reinvestigating every fifteen years.
Secret
This level of security clearance passes serious secret information from Government to individuals to Government. A renewal investigation takes place every ten years for this one.
Top Secret
We heard of many Top Secret agents in movies, but the real-world case is different from that. This is one of the highest levels of a security clearance an individual can get with access to materials that can damage national security if released without authorization. The renewal period is 15 years. Top secret consists of Sensitive Compartmentalized Information (SCI) & Single Scope Background Information (SSBI).
Going through the investigation levels to get a security clearance
Levels are the concerns for purpose and requirement. Each type of clearance may need one or multiple levels of an investigation, depending on the eligibility and accessibility level.
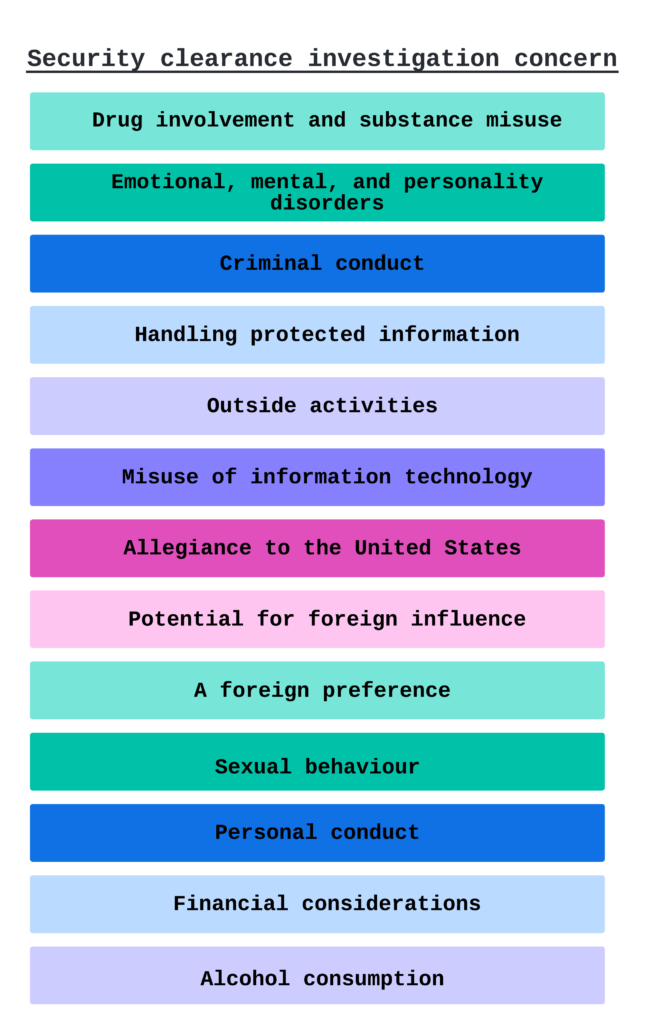
There are Tier 3, Tier 3R, SSBI, SSBI-PR, Tier 5, ANACI, NACLC, RSI, PPR, EBI, and ESI clearance. They include interview subjects, focus scope, extensive investigation, high to a low level, systematic studies, and similar traits.
Receiving the certificate
The long-running procedure is totally worth it. The certificate is not for impatient individuals, as you already understand. The hiring office will request sensitive personal, financial, and other background information to receive the security clearance. FSO sends out paperwork to Dod CAF, where it is reviewed. This information and investigation results are cross-matched. They will decide if you’re worthy of it or not.
If the application is denied, you’ll receive a Statement of Reasons (SOR). You can fix them before resubmitting the application or understanding your ground. You will have the ability to show the counter context of the given reasons. Once you receive the green signal, periodic investigations will take place depending on the type applied.
Additional resources
For guidelines and official documents, follow these links. You can also get the opportunity to advance your professional career with our informative content.
- The US Department of State
- Electronic Questionnaires for Investigation Processing (e-QIP)
- Peronnel Seucity Progarm Regulation
- Guide for SF 86
- Defense Counterintelligence and Security Agency
- Cyber Security Masters Degree Programs in 2022
- Cyber Security Careers Compared and Explained
EndNote
We’re not your legal advisors but only a beacon of guidelines in the world of information. We put together the puzzles for you to make it easy to learn with fewer clicks.
Getting it has many laws and regulations as requirements, and it may change at any time. But our information here should serve you for quite some time as they are from the latest research. A piece of the puzzle we would love to mention as a bonus tip for candidates is to sanitize social profiles. They can often be overlooked, but federal investigators may give over-sharers a negative marking.
On the other hand, as a professional needing this high level of permission, your employer will handle most of the tasks with the regulatory body. So sit tight, and let us know if you find this information helpful.

Leave a Reply