Metasploit framework is an open-source security project that offers multiple penetration testing and exploits development features. All these features can be combined into a set of modules. The core modules are divided into the following categories;
(1) Payloads
(2) Exploits
(3) Encoders
(4) Listeners
(5) Auxiliary functions
Metasploit has a number of payloads for different scenarios. These payloads can be classified as ‘single’ and ‘staged’ payloads. The single payloads are the complete lightweight malicious codes shared with the target machines. The staged payloads consist of a stub-loader that recalls the host machine to send the final piece of payload when (the sub-loader is) executed on the target machine. The exploits are the tools used to take over the target machines by exploiting the vulnerabilities. The encoders play the role of code scramblers. Listeners are used to establishing a connection between the host and target machines. Auxiliary functions are the supplementary tools and commands used to perform different penetration testing tasks, such as scanning, fuzzing, sniffing, etc.
How to Perform Metasploit Update?
Metasploit framework is available with BSD and propriety licenses. The free version supports the Command Line Interface (CLI). In this article, we will demonstrate how to upgrade the Metasploit framework using the command line and graphical interface.
CLI Method
For the CLI update method, we are using the Kali Linux operating system. Open the terminal and verify the current version of the installed Metasploit framework using the following command.
msconsole -v
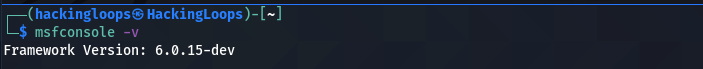
In our case, the -6.0.15 is the current version of the framework on the host machine. We can also verify this version by opening the Metasploit framework using the following command.
msconsole
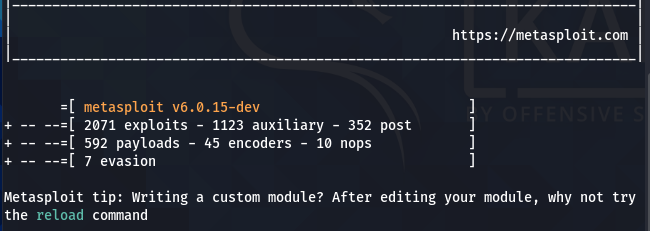
When executed, the Metasploit framework not only shows the existing version but also gives information about the available modules (exploits, payloads, encoders, etc.).
The framework can be updated using the following command.
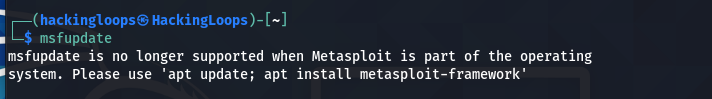
msfupdate
The above command does not work if the Metasploit is a preinstalled package on the current operating system.
In that case, we need to update and reinstall the Metasploit using the following syntax.
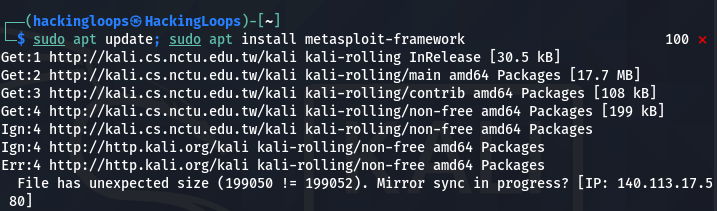
sudo apt update; sudo apt install metasploit-framework
The above command works in two phases. In the first phase, all the OS packages are updated.
In the second phase, the current version of the Metasploit framework is upgraded to the latest stable version. As we can see in the following screenshot, the system upgrades the current (-6.0.15) Metasploit to the latest Metasploit-6.0.38.
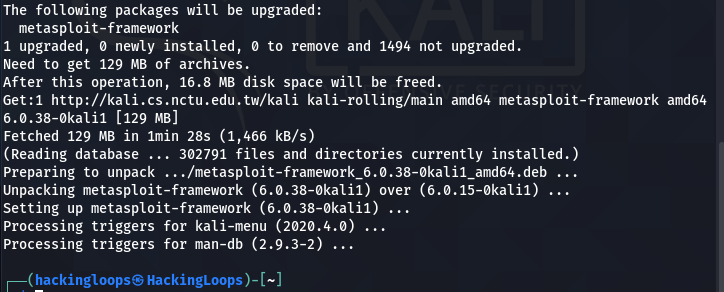
In some cases, the upgraded Metasploit won’t start due to the missing Gems error as shown below.
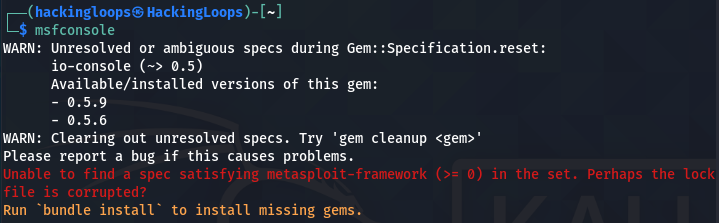
Since Metasploit is a Ruby project, the bundler can track and install the exact Gems required to run the Metasploit. The bundler can be installed using the following command.
sudo gem install bundler
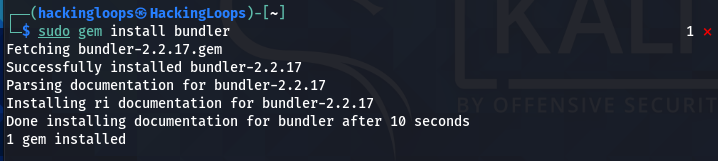
After installing the bundler package, run the following Metasploit upgrade command.
sudo apt-get upgrade metasploit-framework
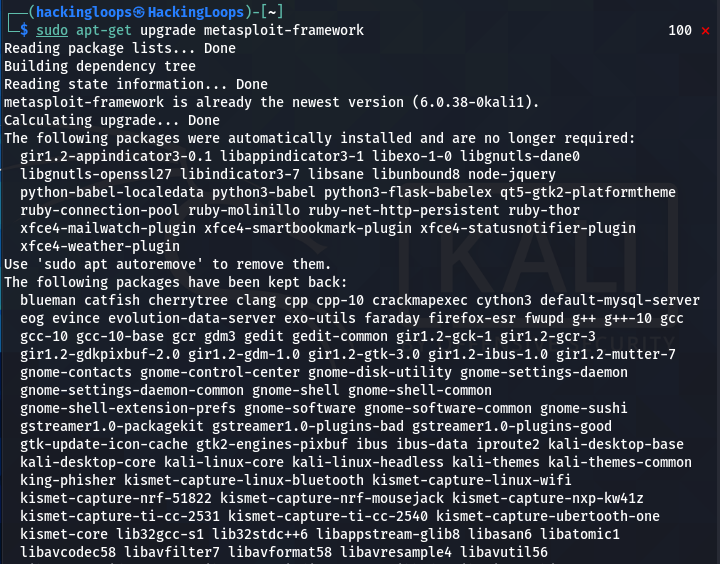
When the up-gradation process is completed, reinitiate the Metasploit database as shown below.
sudo msfdb reinit
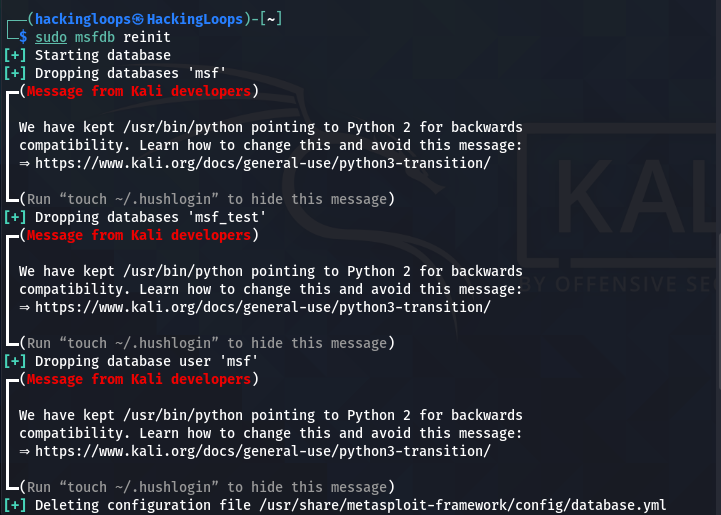
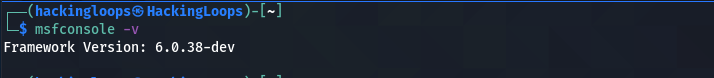
Now we can verify the newer version of Metasploit by typing the version check command.
msfconsole -v
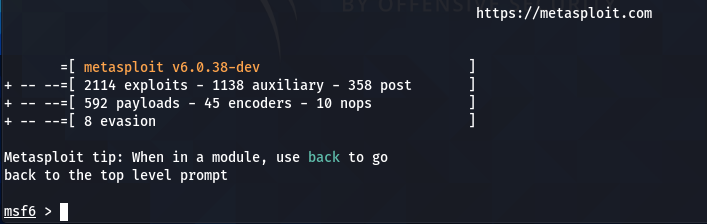
By running the framework, we can see an update in the number of modules in the latest Metasploit framework.
GUI Method
Users with the GU interface can update the framework by manually checking for the updates. The main menu of Metasploit contains a software update button to check the available updates.
If the updates are available, a new window pops up showing the latest available version of the Metasploit framework.
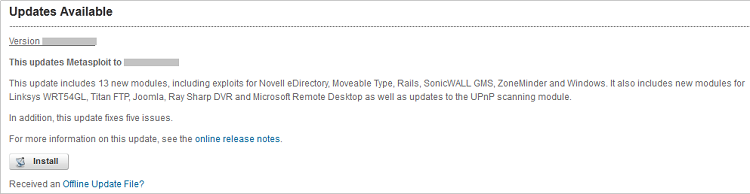
Click on the install button to initiate the update process. The pro users can even update the Metasploit in offline mode through binary update files shared by Rapid7 (the framework owners).
Conclusion
The open-source Metasploit is a leading penetration testing framework with thousands of contributors working on the project. The Metasploit community and Rapid7 developers work hard to update the framework in accordance with the latest vulnerabilities. The users can incorporate these updates by following the aforementioned Metasploit update techniques.

Leave a Reply