
Macchanger User Guide
One fundamental skill that any knowledgeable hacker needs to learn is how to spoof various addresses. In this particular tutorial we will be talking about macchanger but when most people think about spoofing an address, they typically think of masking their IP address with NAT or a VPN tunnel. That said, users also need to learn how to spoof their MAC address.
What is a MAC Address, and What Are They Used for?
Unlike an IP address (a layer 3 address), MAC addresses operate at layer two of the OSI model. As the name implies (Media Access Control), they are used to control and identify different computing systems as they connect to a layer two medium such as a wireless network or a LAN switch. Also understand that each network card has a globally unique MAC address that is composed of two parts – the OUI (Organizationally Unique Identifier) and a unique ID.
MAC addresses are composed of 12 hexadecimal digits, and the first six identify the network card manufacturer. The remaining 6 digits identify a unique network card specific to any given manufacturer. If you want to see who made your network card, simply Google the first six digits of your MAC address. The following are just a few of uses of MAC addresses:
- Static IP’s – If a network administrator didn’t want to use DHCP, they can configure static IP addresses. This is most typically done for servers since it would be a disadvantage if their IP addresses were constantly changing.
- Address Filtering – some network administrators only allow specific devices to connect to a network, and they make filtering decisions based on MAC addresses since they are globally unique.
- Authentication Applications – Sometimes ISPs and other network services require a user to sign in or log on with their MAC address.
- Identification and Temporal Services – Often coffee shops and airports will only permit a short amount of free Internet (30 minutes to an hour). After the time limit has been reached, they will sometimes ban a MAC address, but spoofing your address will allow more free access.
- Tracking Devices – Because every MAC address is globally unique, it is possible for software to track which locations and networks individual computers connect to.
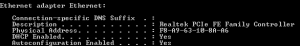 The following is an example of a valid MAC address:
The following is an example of a valid MAC address:
- 00:40:96:43:b7:de
In this example, 00:40:96 is the OUI that identifies this MAC address as belonging to a Cisco Aironet product. If you are using a Windows computer and you wish to view your MAC address, the procedure is relatively simple. First, simply open the command prompt by hitting the Windows key and typing “cmd.” This should pull up an application with an icon that looks like a small black window. Once the command prompt has been opened, issue the following command:
- ipconfig /all
This will display a wealth of information about your computer’s various network interfaces. However, we are interested in the field labeled “physical address,” which will display each network interface’s MAC address. Users on Apple systems or Linux systems can issue the following variant of the ifconfig command:
- ifconfig -a
Why Spoof Your Mac Address?
There are several reasons that a hacker might want to spoof their MAC address. The first reason is to ensure that they cover their tracks and don’t leave their globally unique MAC address in tables on a wireless router or network switch. These devices keep tables of known MAC addresses and bind them to layer three addresses, such as an IP address. Essentially, this would leave an audit trail that would lead back to the hacker’s computer. But there are many other reasons.
Believe it or not, some network administrators control access to their network by only permitting known MAC addresses to send data on the local network. If a hacker’s MAC address wasn’t allowed to send data, the hacker couldn’t even send a ping to another computer on the local network. However, if they know a device that is permitted to send data, all the hacker needs to do is spoof their MAC address to a known host’s MAC address to gain network access.
Macchanger Tutorial
In this demonstration, we are going to run through the steps necessary to use Macchanger to spoof our IP address from an Ubuntu command line (BASH shell). We will be performing the commands on an Ethernet interface, but the same concept and procedure applies to other interfaces. Furthermore, there are comparable alternatives to Macchanger for Windows and Apple systems, and some of them even have GUI interfaces that are ludicrously simple and easy to use.
Step 1
The very first thing we need to do is verify that our Ethernet interface is up and running. It is also advisable to check the card’s actual physical address. So, to start off, run the ifconfig eth0 command to check the status of your network card.
Step 2
The next thing we need to do is shut down our Ethernet interface to make the change. To disable the Ethernet interface, issue the ifconfig eth0 down command.
Step 3
Next, simply use Macchanger to spoof the MAC address. By entering the macchanger -r eth0 command, users can change their MAC address to a randomly generated address.
Step 4
Sometimes users may encounter the following error:
- ERROR: Can’t change MAC: interface up or not permission: Cannot assign requested address
If this is the case, make sure that two things are true. Firstly, ensure that your Ethernet interface is truly down with the ifconfig eth0 down command. Secondly, make sure that you are running these commands as the root user.
Step 5
Verify that the MAC address has truly been changed with the ifconfig eth0 command. If you wish to enter a specific MAC address instead of a randomly generated one, users can use the mac changer -m [MAC ADDRESS] command.
Final Thoughts
It’s pretty darn easy to configure a new MAC address for a Linux system. In fact, the operation shouldn’t even take novices more than a minute to complete. Remember, spoofing addresses is a pretty basic skill for a hacker to learn. I would also caution you not to use this information to break into a network that you don’t have permission to access. If, for example, your MAC address is blocked, I wouldn’t advise you to employ these methods to gain access, because doing so could be illegal depending on the context and location of the network in question. At any rate, this simple demonstration should show you just how easy it is to spoof a MAC address.

Leave a Reply