Lynis is an open source tool designed for security auditing, penetration testing, system hardening, and compliance checking. The tool performs in-depth analysis of the target hosts and warns users/system owners about security flaws and misconfigurations. Based on the discovered security and technical flaws, Lynis also gives suggestions to the users/system owners to improve the security and performance of the hosts/systems.
Supported Operating Systems
Lynis is supported by the following UNIX based OS.
Linux
macOS
FreeBSD
AIX
HP-UX
NetBSD
NixOS
OpenBSD
Solaris
Other systems that support Lynis include:
Raspberry Pi
QNAP
IoT Devices
Lynis Installation
Lynis does not require on any external package. It can be cloned from Github using the following command.
git clone https://github.com/CISOfy/lynis
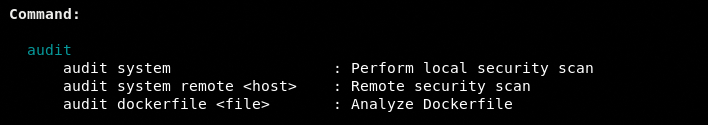
How Lynis Works
Lynis can be run directly from the source code using the following commands.
cd lynis ./lynis audit <audit options>
The following screenshot shows all the available audit options.
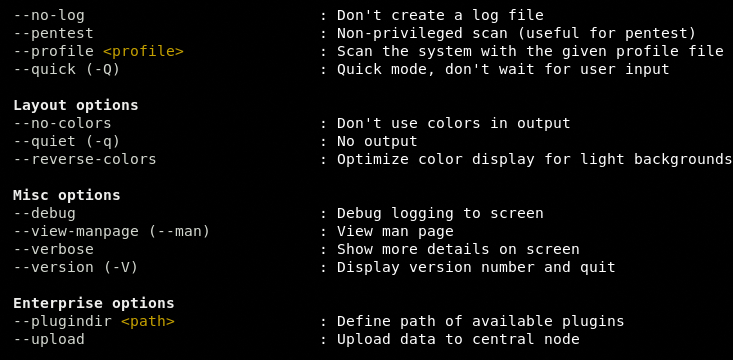
Audit options and the available scan parameters can be explored by typing the following help command.
./lynis –h
Lynis Auditing Cycle
Lynis tries to find out all the available system tools and libraries to perform the scanning (audit). The audit scope depends on the discovered tools and libraries. More tools and libraries mean extensive auditing and reporting. Lynis auditing involves the following steps.
Tool Initialization
Basic checks, such as file ownership
Identification of OS and tools
Available software components checks
Checking the latest Lynis version
Running the enabled plugins
Running the security tests
Performing custom tests (optional)
Reporting the status of security scan
A log file (lynis.log) is also generated that records all the technical details of the scanning process. Another file (lynis.dat) contains all the suggestions and warnings observed by the tool. The information about these files is shared during the program initialization. The scan results (findings/suggestions/warnings) also appear on the screen during the auditing process.
Lynis Audit Example
To demonstrate Lynis working, let’s assume the target is the Linux operating system. Lynis tool is cloned on the same OS. We can run the following command to start scanning the target operating system.
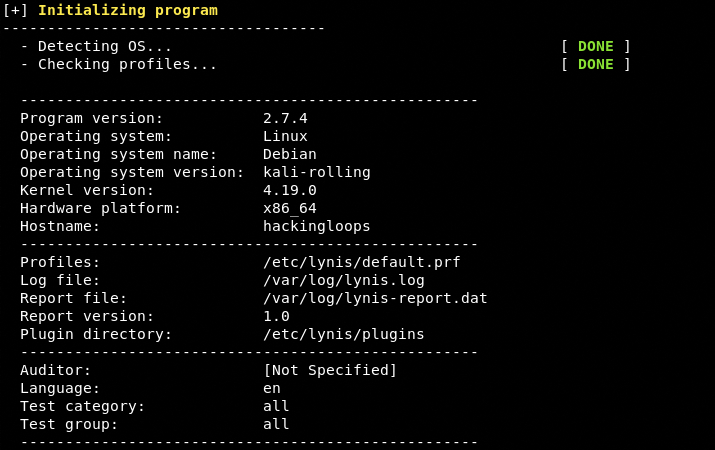
./lynis audit system –Q
Here –Q is optional that is used to enable the quick auditing mode. The command initializes the auditing process by detecting the OS and checking the necessary audit files (log file/report file) and directories as shown in the following screenshot.
As mentioned earlier, Lynis performs the auditing based on the available components (file system/tools/libraries etc). Following are some of the screenshots taken during the example auditing process.
Operating System Tests
The test covers system binaries check, authentication test, file system, and software checks.
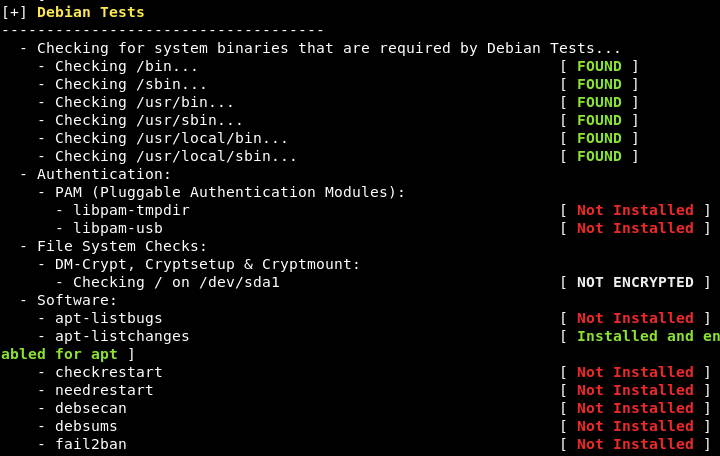
Boot and Services Test
The test covers different services and permissions.
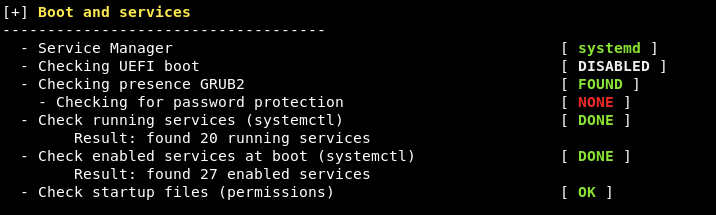
Kernel Test
Lynis performs a number of Kernel related tests, such as Kernel version, level, modules, and configurations.
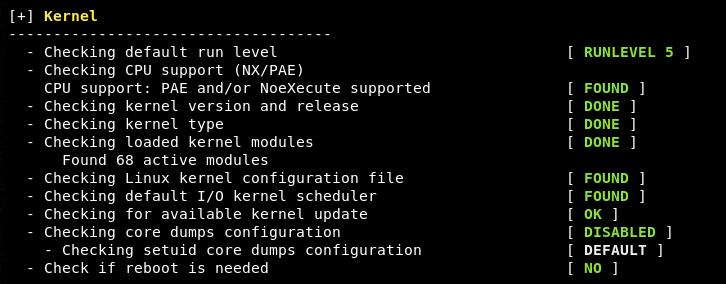
User, Group, and Authentication Test
This is probably one of the most awaited tests performed by Lynis. The tool looks for the users’ accounts, groups, authentication, and accounts security related data. The data gathered during this test is equally important for system administrators, penetration testers, and security auditors.
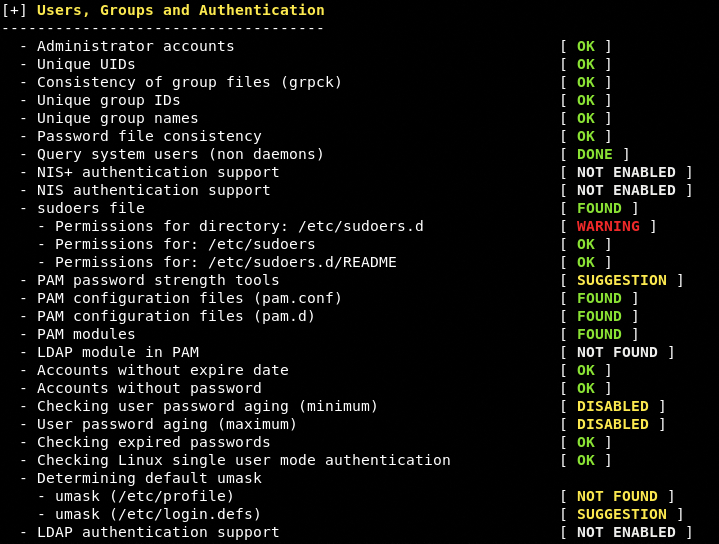
File Systems
USB Devices, Storage, and NSF
Networking
Kernel Hardening
After completing the scanning process, Lynis presents the auditing summary in the following format
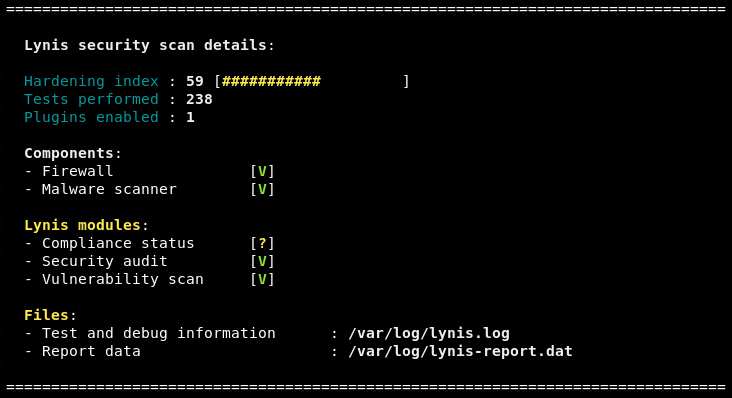
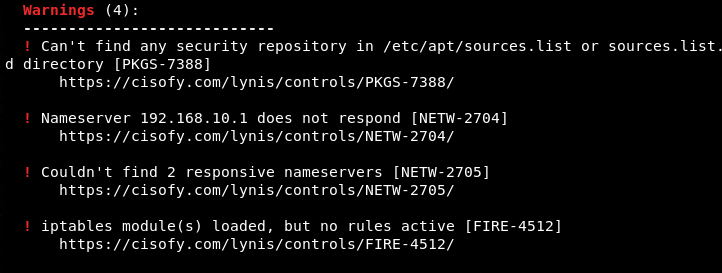
Warnings and suggestions are also mentioned at the end of scanning process.
Warnings
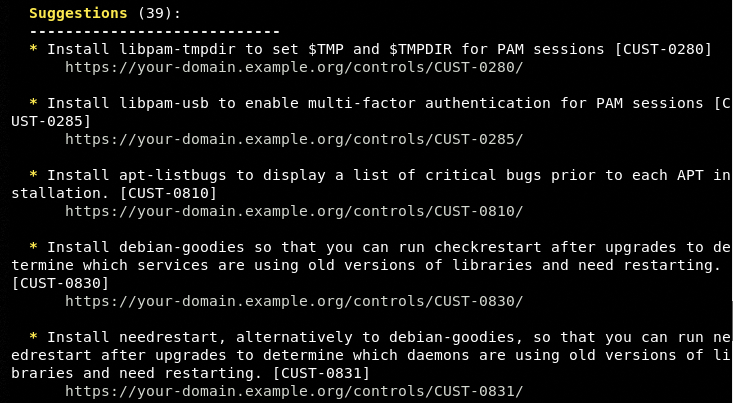
Suggestions
Summary
Lynis can be used by different individuals like systems administrators, developers, IT auditors, and penetration testers for security auditing, penetration testing, vulnerabilities detection, system hardening, and compliance check. The tool performs most of the tasks automatically.

Leave a Reply