Process Hacker 2
Not only humans are hackers. We now have automated tools and machines that can hack as well. Today we will discuss such a machine that can hack processes in an operating system.
The definition of hacking does not specifically mean that it can be used for negative means only. If we look at the literal meaning of hacking then we come to know that it means taking control over something. This control can be used for fair purposes as well. The tool Process Hacker gives one control over all the processes running in one’s system.
Let’s see where we can get this tool and how to install it. The link for the tool is given below:
Go to the link and press the Download Process Hacker button.
Now download the file according to your need. You can select multiple options. Let us choose the most used options these days i.e. Windows 10 version .exe file highlighted below:
You will see a 2.2 MB file downloaded to your machine. Now, let us see the different options we will get for installing the software.
The steps are as follows:
- Run .exe file
- Select path
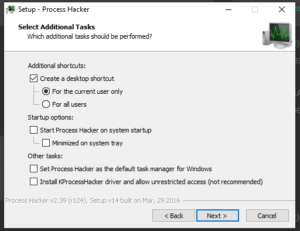
- Check all available options and click next
- Let’s choose the default options for now. You can also change them according to your need.
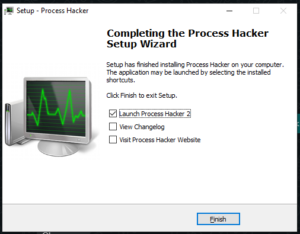
- Check the first option and finish the setup to launch the software.
The current version of this tool is known as Process Hacker 2. Now let’s see the working of this software. The home page of the software looks like this:
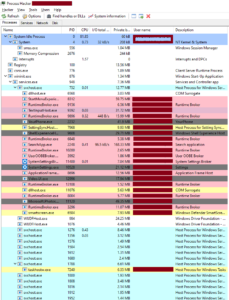
Once the software is opened, it shows multiple tabs:
- Processes
- Services
- Network
- Disk
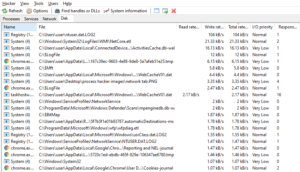
The default view would be the processes tab where we can see multiple details about all the processes running in the system currently. This tab shows the following details about the processes:
- Name of the processes
- PID i.e. process IDs of the processes
- CPU usage percentage by each process
- I/O i.e. input/output rate of each process
- The name of the user who is running that particular process
- Description i.e. a little more detail about the process
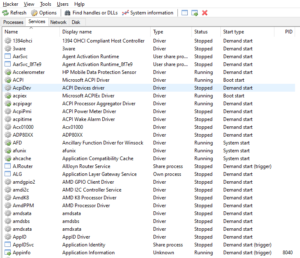
The next tab is the Services tab which shows the following details:
- Name i.e. name of the service on the machine
- Display Name i.e. the name which is known to the user, e.g. “asp.net state service”
- Type of the process which can be e.g.
- Driver
- User Shared Process
- Shared process
- Own Process etc.
- Status i.e. whether the process is in running state or stop state
- Start Type i.e. how the process was created or started
- PID i.e. process ID in the system
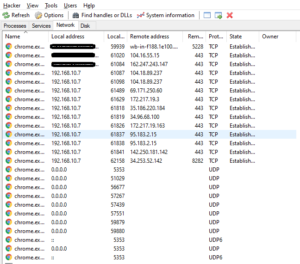
The next tab is an important one considering that if someone wants to know what is happening in the system or if someone wants to find out what kind of communication is going on between the system and the outer world. The network tab gives the following details:
- Name of software or service running
- Local Address: that is mostly your own system name or localhost
- Local Port i.e. The port number used by that specific software instance
- Remote address, i.e. the address to which communication is being made
- Remote port, i.e. Port in use of remote address/system
- Protocol, i.e. Transport Layer Protocol used by specific software or service (Mostly UDP/TCP)
- State of Connection: It can show multiple options based on the connection state which may be:
- Established
- Closed
- Close wait
- Listen
- Time Wait etc.
- Owner: specifies the owner of that connection
The next and last tab is Disk. The disk tab requires running it with administrative privileges. It shows the following details related to processes:
- Name: It shows the name of the software or service in use.
- File: Complete path of the file that is using that service
- Read Rate Average: Data reading rate from the disk (kB/s)
- Write Rate Average: Data writing rate on the disk (kB/s)
- Total Rate: Total of Reading/Writing rate
- I/O Priority: It shows what is the priority of the service for reading/writing data from/on the disk respectively. It can be:
- Very High
- High
- Normal
- Low
- Very Low
- Response Time: Time is taken by service in giving response back (calculated in milliseconds)
If we bring the cursor on any process or service in any tab, it shows the details related to that further which can clarify many details about that process.
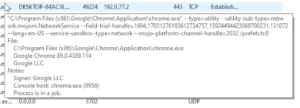
Settings
We can also change multiple settings related to the processes. To access settings, look at the top menu and find the “options” tab next to “refresh”. You can find multiple settings there. The settings which people mostly use are in the “highlighting” tab. After clicking on “highlighting”, you can see multiple colors and some checkboxes along with them just like the image shown below.
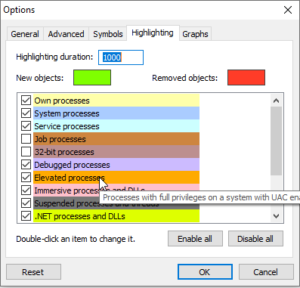
One can do the following tasks with this tab:
- Select type of processes to see in the list according to requirements
- Duration of highlighting a process
- Change the color for each process according to need. Double click the item and select the required color for that particular process type.
Uses of Process Hacker 2
Considering the working behavior of Process Hacker 2, a person can use the functionality of this software for various purposes.
- One can replace the Task Manager with Process Hacker 2 because it also keeps track of all the processes
- Process Hacker 2 provides the tree-like structure of all the processes giving a better understanding of what’s going on in the system
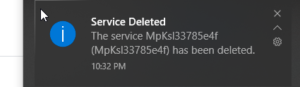
- The users who look closely at their systems can use this software to keep track of every service running in their system. When services are created or deleted, it sends a notification on the laptop and this way every time a process or service is started, one can look at it if it is legitimate or not.
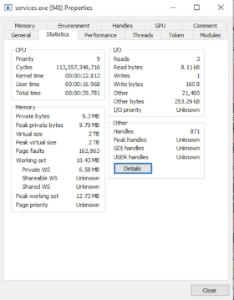
- If one identifies something as malicious, one can find its details by double-clicking on the process. Double-clicking the process opens up a window containing different information. One can identify the memory usage of process, GPU usage, etc. One can also identify where the process resides in the memory, when it was started, who started the process(parent of the process), and much more.
- One can identify the processes which are not closing down due to some reason and then close them manually. One can also search about specific processes/applications etc. and take action according to need. Process Hacker can close down those processes that others cannot close for any reason.
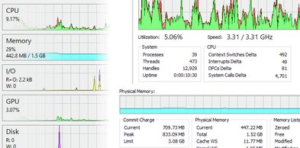
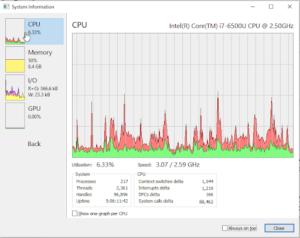
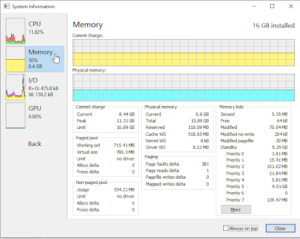
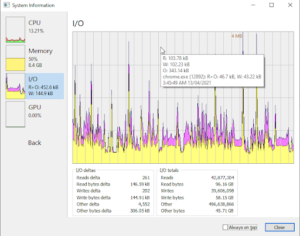
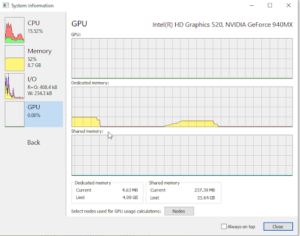
- One can find useful information related to the usage of the system resources by all the processes running. There is a tab of “System Information” on the top menu. Click it and you will see multiple tabs on the left. The window tells the following information:
- CPU Utilization & Info:
- Memory Utilization Info
- I/O rate and Info
- GPU Utilization & Info
- CPU Utilization & Info:
- We can also create memory dumps of different processes. It helps in the forensics phase of any investigation in which it is practiced to understand the behavior of any process. If the process is a malicious entity, its behavior will give the idea to the investigators how the process started its damage and what steps were followed in this process. To get this file, right-click on the process and select “Create Dump File”. Select the path and it will create a dump file that can be used for further processing. This file is mostly opened in a hex file editor or text editor etc.
Summary
This was the short and basic introduction of process hacker 2. The software can be very useful as it gives one detailed information about all the processes and services running in the system. Users can get complete control over the system resources. Users can also keep the track of what kind of applications are using system resources and identify if something malicious is active.

Leave a Reply