Red Hawk is a PHP based web application scanner used for information gathering purpose. The information gathering tasks that can be achieved with Red Hawk tool cover basic web scanning, WHOIS record, Geo IP data, Banner information, DNS record, sub-domain information, reverse IP lookup, MX record, bloggers specific data, and WordPress scanning. In the basic web scanning task, Red Hawk grabs information like IP address, Content Management System (CMS) identification, server information, and Cloudflare detection. The subdomain scanner fetches subdomains and their IP addresses information. The bloggers specific scan covers the data that can be useful in analyzing the web application from optimization point of view. This includes information about domain authority, page authority, social links, Alexa ranking, and HTTP response of the web pages. WordPress scanning includes WordPress sensitive files lookup, WordPress version detection, and scanning vulnerabilities that are associated with WordPress versions. Apart from these information gathering features, Red Hawak has SQLi scanner that fetches links and parameters that may be vulnerable to error based SQL injections.
Red Hawk Installation
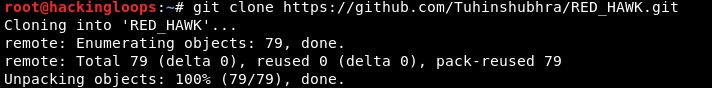
To install Red Hawk on Linux OS, first we need to clone the tool from Gitub using the following command.
git clone https://github.com/Tuhinshubhra/RED_HAWK
In the next step, navigate to the RED_HAWK directory and run the rhawk.php file using the following commands.
cd RED_HAWK php rhawk.php
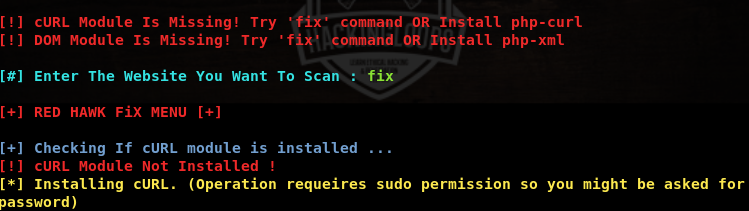
As a result, Red Hawk tool loads with a warning message showing the missing modules. Type the fix command in the terminal to auto complete the installation of missing modules.
fix
How Red Hawk Works
Running the following command in the terminal opens the Red Hawk tool.
php rhawk.php
At this stage, Red Hawk asks for web application address and communication protocol (whether it is http or https).
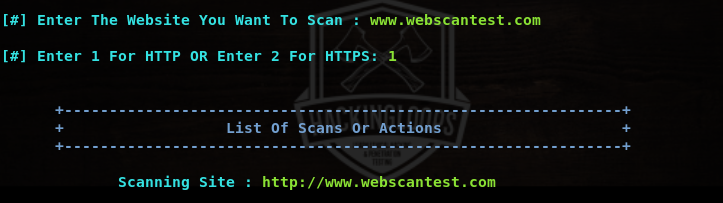
Once the information is provided, Red Hawk loads all the scanning modules as shown in the following screenshot.
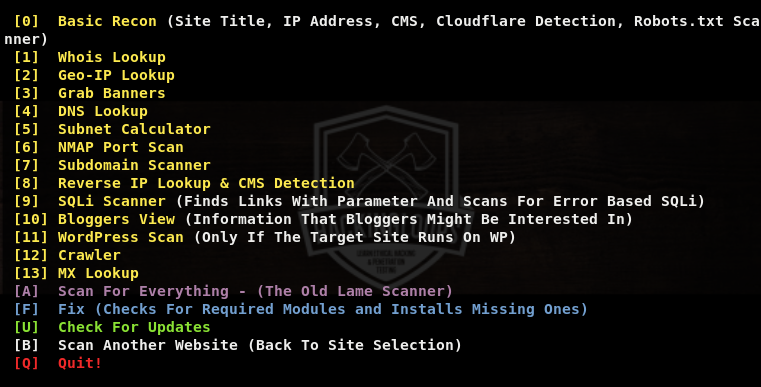
We can select any scanning module by typing its sequence number in the terminal. For instance, we can select the WHOIS scanning module by typing its sequence number (#1) in the terminal as shown in the following screenshot.
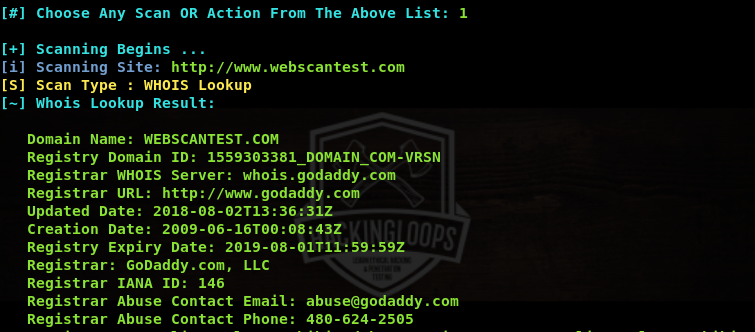
Similarly, we can get geo IP data (IP, country, state, city, latitude, longitude) about target web application in the following manner.

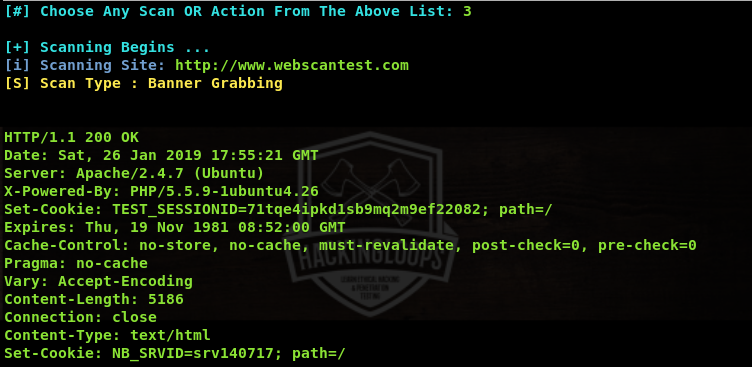
The banner grabbing module fetches very useful information about server, programming language, cookies, and connection type of the target web applications.
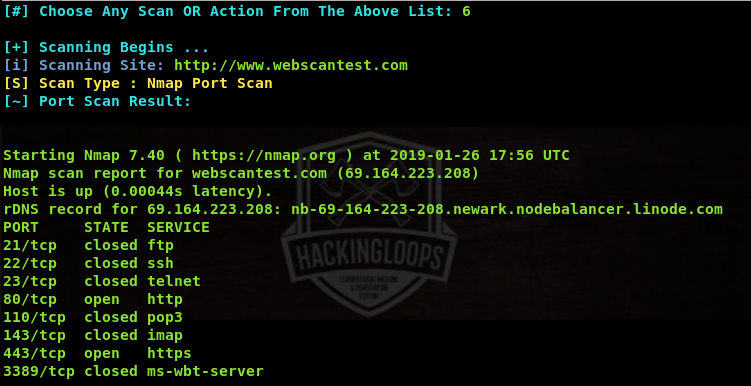
The port scanning module scans all the major TCP ports of the target web application along with the services and current state of the ports.
Subdomain finder is another useful feature of Red Hawk tool. The tool finds all the subdomains of the target web application and their IP addresses.

Apart from these information gathering modules, Red Hawk has SQL vulnerability scanner that finds out links with possible error based SQL vulnerabilities. The potential vulnerabilities can be verified with the aid of other database injection tools like sqlmap.
Conclusion
Red Hawk possesses a number of active and passive information gathering modules. The information obtained through these modules is pretty accurate and comprehensive.

Leave a Reply