There are many open-source penetration testing tools available to perform security auditing. The security professionals can get these tools from the official repositories of the creators of these tools. Since a platform like Github supports all sorts of Cybersecurity projects, finding the best penetration testing tools often becomes a tiresome job. However, there are developers who spend time to find and program these tools to make them executable from a single place. Sifter is one such platform that contains a number of useful penetration testing tools to perform different actions, such as open-source intelligence, reconnaissance, enumeration, vulnerabilities assessment, malware analysis, and exploitation tasks. The framework automates the process of selecting and running the integrated tools, making the execution part simpler and easier for the users.
How to Configure Sifter in Kali Linux?
The sifter can operate in all major distributions including Windows, Linux, Parrot, and Ubuntu systems. In this tutorial, we configure Sifter on a Kali Linux virtual machine. In order to configure Sifter on the host machine, clone the framework from the following Github repository.
git clone https://github.com/s1l3nt78/sifter.git
After cloning, navigate to the sifter directory and change permissions for the installation file using the following commands.
cd sifter chmod +x install.sh
In the next step, execute the installation file as shown below.
./install.sh

Since the Sifter is a combination of multiple tools and scripts, the installation process takes some time to download and configure the basic scripts and utilities on the host machine. After installing the required libraries and packages, the framework performs a self-test to validate the installation process.
How to Run Sifter Framework
Once the Sifter is successfully installed, we can run it from the terminal using the following command.
sifter
The above command opens the following primary menu in the terminal.
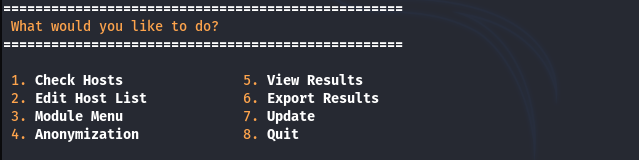
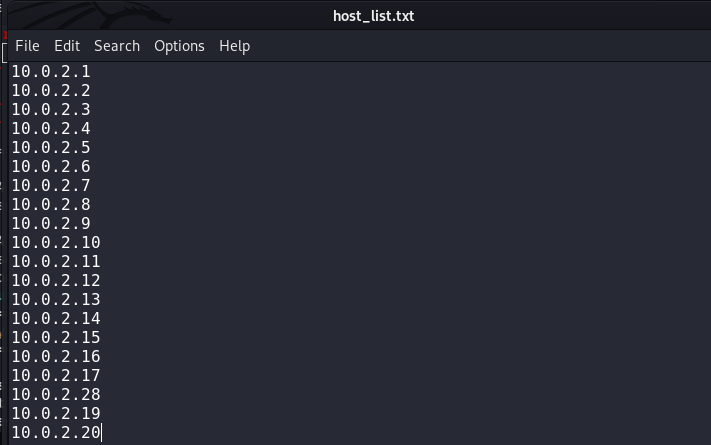
The menu shows different options like hiding the user identity, defining target network hosts, and navigating to the modules menu. Since it’s a fresh installation, we need to define the target hosts by selecting the Edit Host List option from the list. A modified list containing the target hosts IP addresses is shown in the following screenshot.
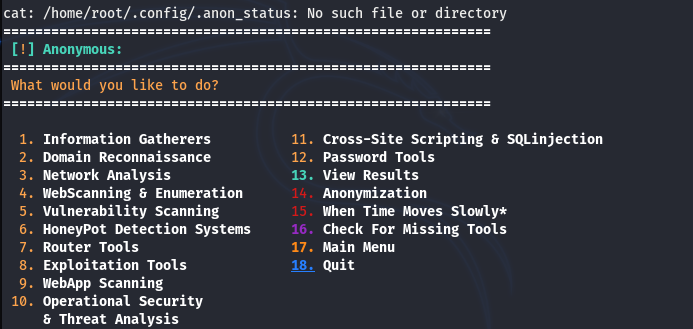
After defining the host’s list, we can navigate to the Module Menu by selecting its sequence id (i-e 3).
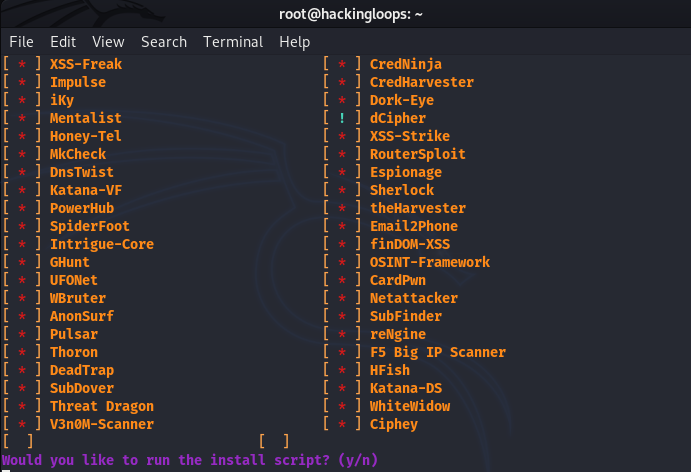
There is a missing tools category at number 16 in the modules list. This section shows the list of penetration testing tools that are yet to be installed by the user.
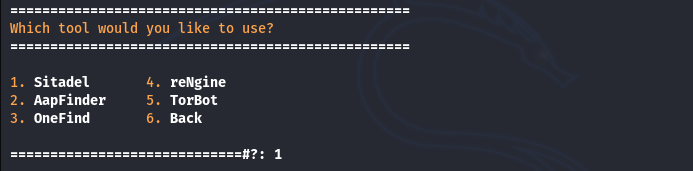
The missing tools can be installed by simply following the on-screen instructions of the Sifter framework. Each module category represents a unique set of tools. We can explore each module section to find out the available tools and apply them in penetration testing campaigns. For instance, if we open the Webapp Scanning module (At #9), we get the following related tools to perform the web applications security audit.
If we select the Sitadel tool from the list, we are presented with some basic configurations that are required to initiate the scanning process. These configurations can be seen in the following screenshot.
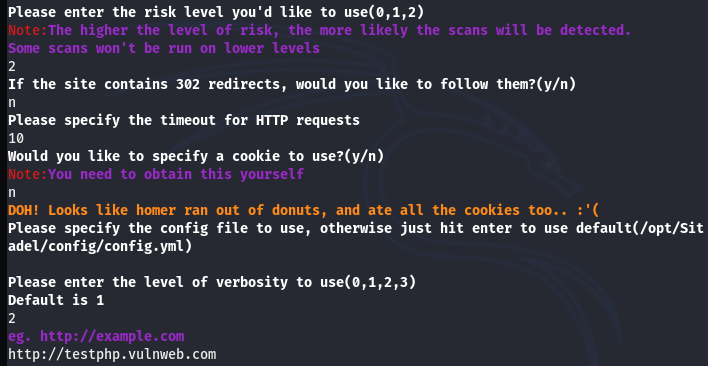
After configuring the tool and selecting the target host, the Sitadel tool scans the target host and displays the gathered information in the following format.
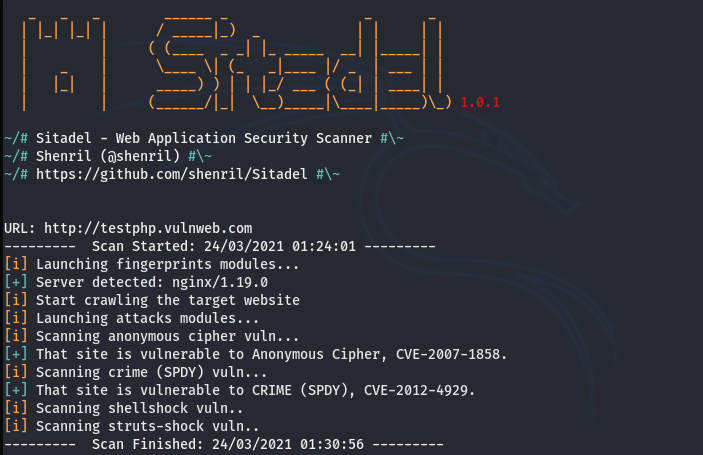
Similarly, if we explore the Vulnerability scanning module, we find the following listed tools in the arsenal.
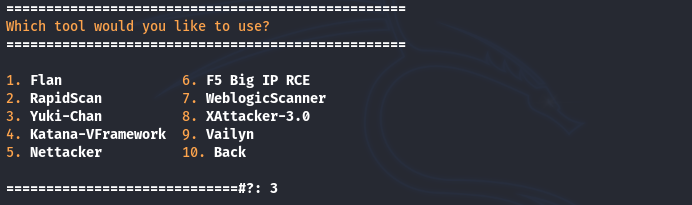
The list contains some renowned web auditing tools like RapidScan, Yuki Chan, and Nettacker. We select the Yuki Chan as an example tool. After providing the web address, the tool automatically runs to analyze the target host and fetches the results. Following are few screenshots of the results gathered by the Yuki Chan vulnerability assessment tool.
WHO IS INFORMATION
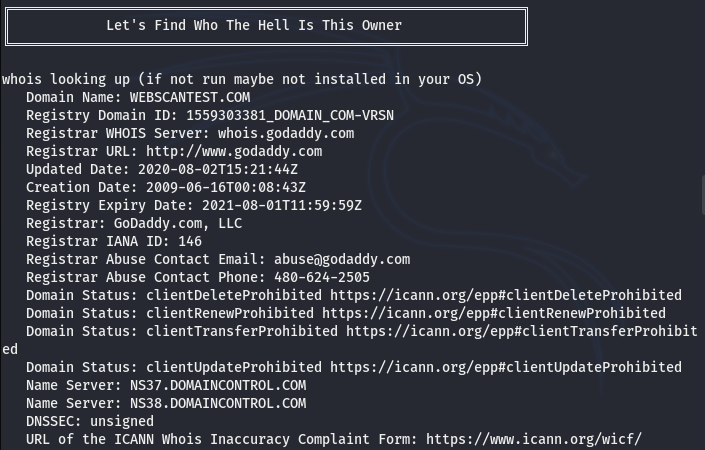
REGISTRY INFORMATION
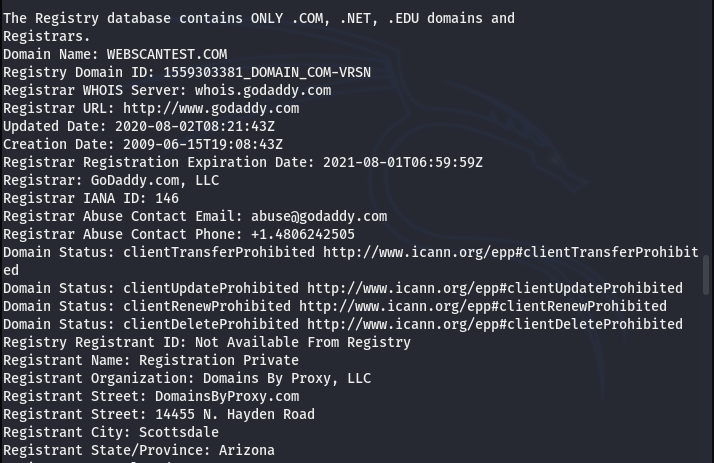
SERVER INFORMATION
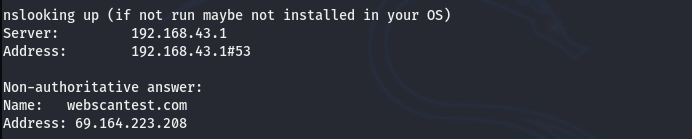
OPEN PORTS INFORMATION
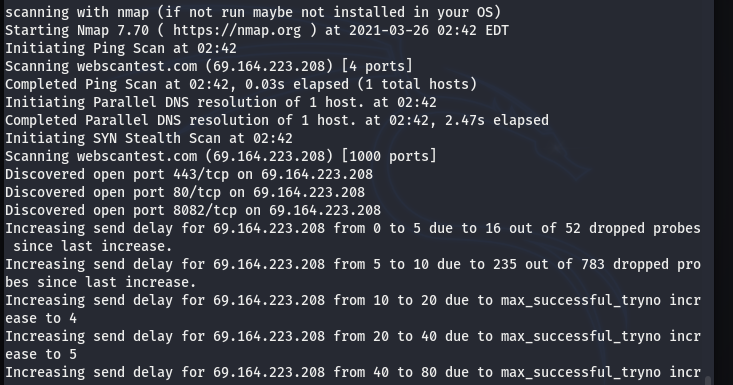
Conclusion
Sifter is a nice effort to compile a list of useful penetration testing tools and automate their functionality. The framework is a combination of multiple useful penetration testing tools. A large set of tools requires decent space and memory to perform the desired operations. Therefore, Sifter is not an ideal choice for systems with limited physical resources. Lack of ability to install the selected tools is another drawback of the Sifter framework.

Leave a Reply