Network Mapper, also known as Nmap, is a powerful open-source tool for scanning local and remote networks. Scanning ports, discovering an operating system on a network, typical network scans, looking for open and closed ports, detecting sniffers, state of the remote machines can be done via Nmap protocols. Network administrators, enthusiastic learners, and hackers use the tool to know remote host stats, allow or block connections, and monitor remote hosts, among many others.
The article will demonstrate hands-on scanning for live hosts with Nmap and its fundamentals.
Disclaimer
Nmap is a pretty powerful tool and can provide well-documented results on a network. It is advised to perform scans on own network and not to mess with systems without the permission of a network administrator. Setting up rate limit, ignoring addressed packets, using VirtualBox to stay on the safe side of the network is suggested.
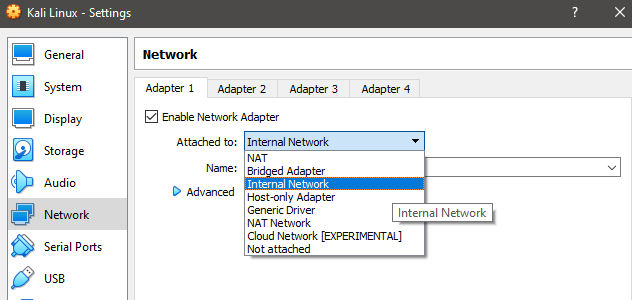
In VirtualBox of any OS, it is recommended to active a vulnerable sandbox environment, and from the “Network” setting, “Internal Network” should be selected. If that wouldn’t be an issue, then the default is fine.
Nevertheless, it is a great way to learn about the network, looking for ports and information on other users in the network.
What is Nmap
There are plenty of tools for active information gathering during a penetration test. One of them is Nmap, which can send out a detailed profile of the target. The library or commands are plenty and powerful, and it doesn’t have any GUI (graphical user interface). So command line is the suitable option to achieve goals with Nmap.
Besides being open-source, Nmap is portable, flexible, and easy to use. The command-line utility can be started just by typing “nmap.”
Scanning for live hosts with Nmap
Setting up the environment: To scan for live hosts with Nmap, we first need to install it on our Windows or Unix-based machine. Simple browsing this link will give us a download option. We can download and install the executable (.exe) file for Windows operating system, and for the Unix-based system, we have to use the command line, but in Kali Linux, it is installed by default. Using #ipcionfig and hitting enter will show relevant network information for us to get started.
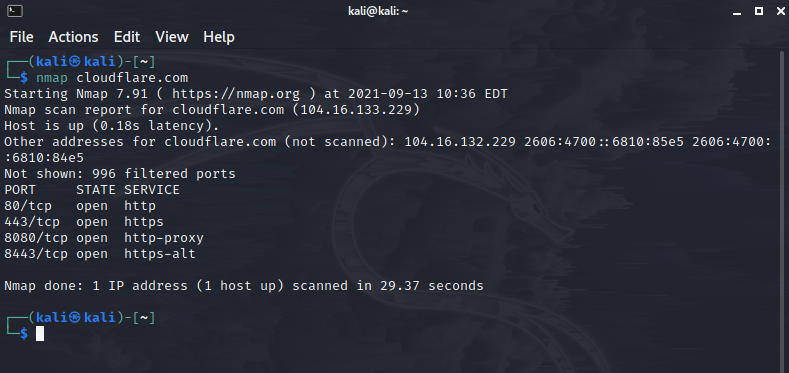
Let’s start by testing a basic Nmap scan using IP or host. For this, we can state the following command. It will show us open ports relevant to the network.
#nmap cloudflare.com
Now we can start launching ping scan against any network segment using,
#nmap -sn <target>
Running basic scan: To start a basic scan, we can use the following syntax:
#nmap <target IP or hostname>
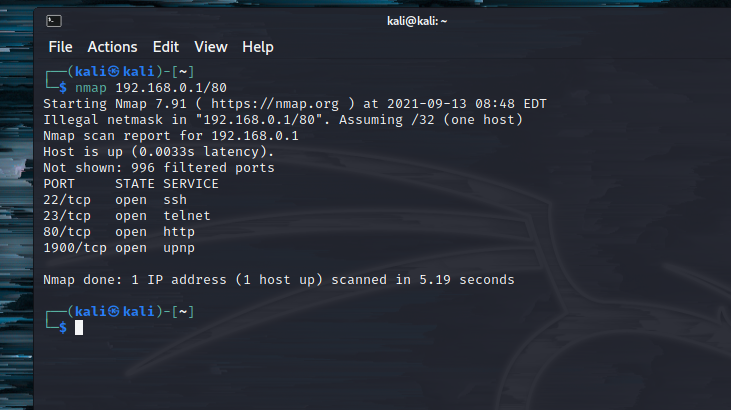
Let’s assume the home network is 192.168.0.1/80, and we want to scan the network, running the scan with
#nmap 192.168.0.1/80
It will give us a list of open and closed ports and even MAC addresses. Even websites can be scanned and assuming we have legal permission to do so with the following command:
#nmap scname.nmap.org
Once hit enter, it scans for 1,000 most commonly used IP/TCP ports.
The Nmap scripting engine helps us scan a network and look for hosts simultaneously. As additional information, we can execute other tasks; there are sample Nmap scripts that we can find throughout the web, especially GitHub.
Nmap sends out the packet to hosts to check if it is live or not. Alive targets responded to our command, and closed ports don’t, the only sign we can see a host is shut, and that’s it. So, we can perform on our own machine or set up a vulnerability to tweak with.
Cybersecurity professionals disable Internet Control Message Protocol (ICMP) responses to show ICMP echo reply targets offline or online. For this, we use -Pn operator and the Nmap host discovery and target will be handled as an online function.
#nmap -Pn 10.10.10.100
Network administrators tend to apply multiple layers of security to prevent attackers from gaining information this easily, so don’t be discouraged if no results come back. Though hidden systems and firewalls can be bypassed, using the correct command in the right situation is quite tricky.
Though we can scan for specific ports on specific targets (e.g., 32/80) using Nmap. For a network running on TCP protocol,
#nmap -sV -p 192.168.0.1/32
#nmap -sV -p 192.168.0.1/80
Network administrators can detect if a port scan is being done by a hacker or penetration tester. For that reason, there is another version of Nmap scanning for live hosts stealthily.
TCP in Nmap scanning establishes a three-way-handshake to open ports. Once the handshake is established, packets of data or messages are exchanged, and we can see a snippet of transfer. To perform a stealth scan, we can use Wireshark too for getting target packets.
To evade firewall and develop a career as a cybersecurity expert, a Nmap user should learn how to bypass a firewall for scanning live hosts.
To scan a specific port within a range, we need to set up the parameter, like 192.168.0.1.x with a class c range, and it can extend up to 254. For range scanning using Nmap:
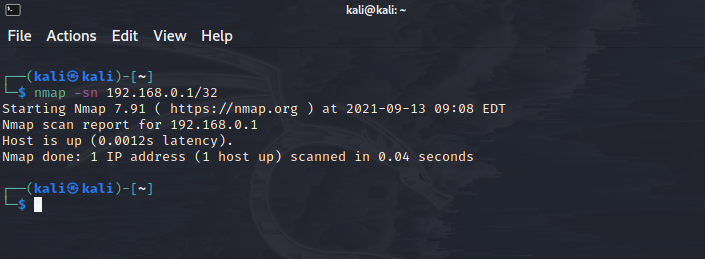
#nmap -sn 192.168.0.1-254
CIDR method uses the same way to sweep a ping.
Ping sweep with Nmap
Sometimes we need to identify live hosts during penetration tests. There are special tools with GUI for ping sweep, and we have a dedicated article for that. Nmap can perform ping sweep multiple targets at once, and we just have to set the range or subnet to run the scan. -sn operator allows us to ping sweep of a network and stays on the safe side of things, and we are using our network to perform ping sweep. The GUI application list mentioned as a link has a few chosen and best options to experiment with.
Useful Commands
Specific commands are more valuable than others, but eventually, it depends on the user and the situation of a scan. Here are a few useful and popular commands to get started
- –v to increase verbosity
- -n to skip DNS resolution, which as a results boots scan speed
- -PE for ICMP echo requests
- -sn to skip scanning ports
- -T4 for TCP ports exceeding delay of above 10 ms
- –packet-trace for tracing sent and received packets.
Conclusion
Open-source tools are open for a reason; they are powered by a large community of enthusiasts and can be accessed via literally everyone, making the tools powerful as many experts contribute to the matter.
Being a robust system inventory and port scanning tool, it has both good and bad sides. The wrong side is utilized by hackers or people who want to cause harm to leverage stuff. Necessary precautions should be taken by network administrators to keep bad intentions out of the network. There are tons of documentation and user guides for Nmap concerning scripting, NSE scripts or Zenmap.
