Android Forensics Tutorial 4 – Unlock Android Pattern Lock: In our previous Android Forensics Tutorials, we have learned about Directory structure, File Systems, Data Acquisition methods and how to copy sdcard data to your computer drive. In this Android Forensics Tutorial, we will learn about How to unlock or recover Android Pattern Lock or pass code. As we all know, currently android supports three basic types of pass codes to lock Android Smartphones namely Pattern Lock, PIN and Alphanumeric Code. Each of these pass codes can be hacked via using a different approaches. Each method has its own limitations. Today i will explain how to unlock Android Pattern Lock of a rooted device via USB debugging method.

Forensics Tutorial 4 – Unlocking Android Pattern Lock
If USB debugging is enabled, then bypassing the lock code can be done in a matter of seconds. Imagine an attacker who wants to get access to his friend’s files and applications on his Android mobile. You can first ask his handset for some false reason, to make a call, for example, and turn on the USB debugging under Settings à Developer Options à USB debugging; and then hand over the mobile back to him. So later, at some convenient time, when you get access to the device, you can exploit it using any of the following ways discussed in this article. Now adb (Android Debugging Bridge) is primarily a command line tool that communicates with the device. ADB is bundled with the Android platform tools. To explain in simple terms, this is what happens when you communicates with adb(Android Debugging Bridge):
-
An adb daemon runs as a background process on each Android device.
-
When you install Android SDK on your machine, a client is run. The client can be invoked from shell by giving an adb command.
-
A server is also run in the background to communicate between the client and adb daemon running on the Android device.
Now lets learn how to Hack Pattern Lock of any Android device in less than 5 minutes. The only condition required is that, smartphone should be rooted.
Unlock Android Pattern Lock or Pass code :
-
Connect the device to the machine where Android SDK (including platform tools etc.) is installed.
-
Open command prompt and type cd C:\android-sdk-windows\platform-tools>adb.exe devices
-
The device will be identified by the adb if everything is going fine.
-
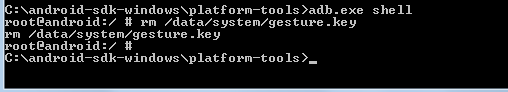
Connect to adb shell by typing : adb.exe shell
-
The terminal appears giving you access to shell. Now type rm /data/system/gesture.key. This is the file where pattern is stored.
-
Restart the phone and you will still observe that the device is asking for the pattern. You can draw any random pattern and unlock the device.
Below is the screenshot of above process :
That’s all for today friends. We will learn other Forensic Methods in detail in future articles.
List of Previous Android Forensic Tutorials :
Hope you all have enjoyed our Forensics tutorial on Unlock Android Pattern Lock. Keep Learning !! Keep Connected!! Sharing is Caring!!
