A Vulnerability Scanner is a software tool that allows you to scan for any vulnerabilities on a given target. In some cases you may only have external access, such as when doing a penetration test; and some others you may even have physical access to the host you want to protect, such as configuring a web server, an end user’s host or even a border firewall.
Knowing this, we’re going to highlight some of the most popular and best vulnerability scanners that either come included in Kali Linux, or are available just an apt install <program> command away.
nmap

Nmap (network mapper) is perhaps the most popular network and port scanner ever created. It is capable of scanning for useful information; such as open ports, running services, operating system version, etc. It accomplishes these tasks by sending IP packets to probe the target host, or network, in various ways.
The main characteristic of nmap is that you can specify whether to scan entire networks or single hosts, while it keeps record of every single host it finds and lays it all for you in the report it generates.
Nmap can be used for host discovery, TCP/UDP scans, ICMP scans, Protocol scans, OS detection, Service/Version detection, and more.
For more detailed information about nmap, you can have a look at its Manual (man) page. We also have an Nmap Cheat Sheet that you can take a look at.
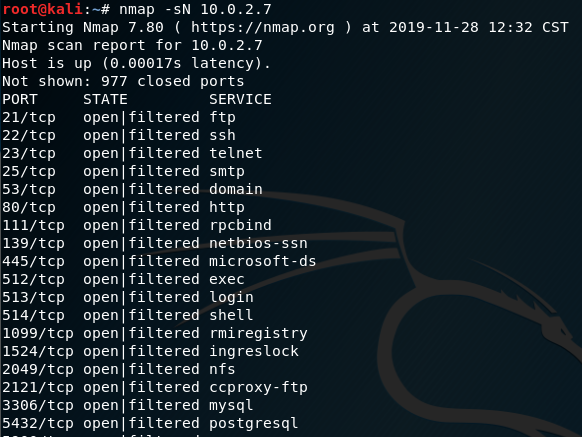
Here is a screenshot of a simple nmap port scan.
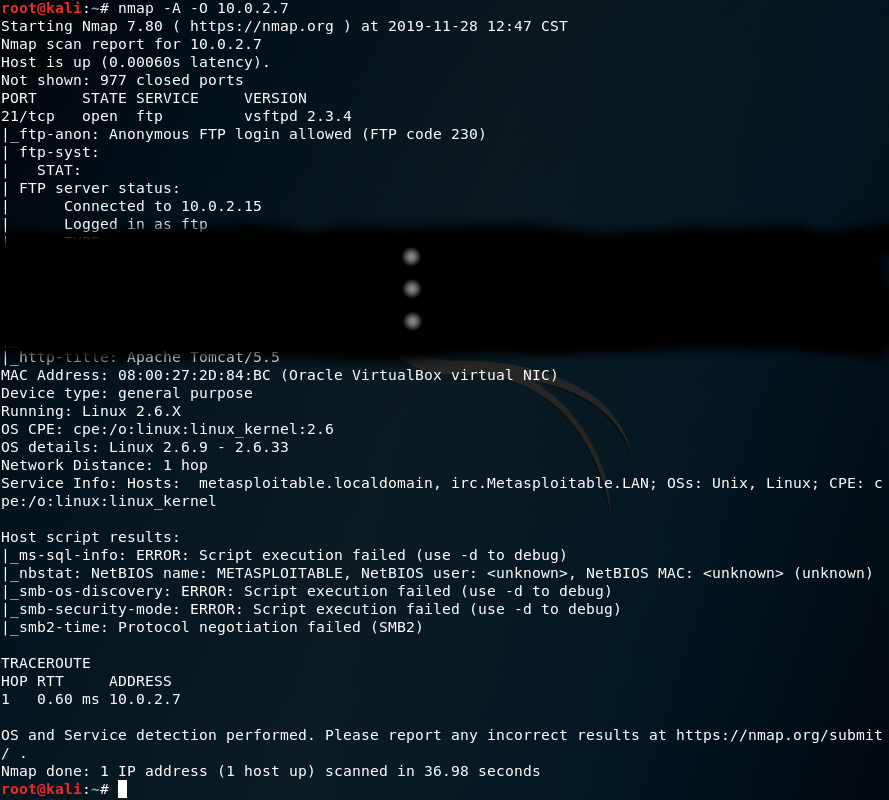
And here is a screenshot of a deeper scan, that searches for the detailed information about running services (-A) and for OS detection (-O).
dirb
dirb is a web content scanner that looks for hidden directories and files on the target website.
Dirb will use a word list to launch a set of HTTP requests, from which it will analyze each of the HTTP responses to determine whether or not the directory exists on the target. Though it
comes with a set of pre-installed word lists, many others are available on the Internet.
Because of this, dirb doesn’t exactly search for vulnerabilities. On the other hand, it does look for specific web objects that other generic CGI scanners simply can’t look for; which means it is capable of covering some holes that other vulnerability scanners can’t cover.
WPScan
The WordPress Vulnerability Scanner, WPScan is a free vulnerability scanner, written specifically for security professionals and blog maintainers that want to scan the security of their WordPress sites.
It is capable of enumerating installed plugins, login accounts, brute forcing passwords, and traversing the directory structure of the target.
Nikto
Nikto is a scanner that performs a comprehensive set of tests against multiple items.
Nikto is capable of tasks such as:
- Checking HTTP response headers, page content and content hashing
- Verifying cookies for session hijacking possibilities
- SSL inspection
- Checking for outdated server components
- Inspecting \verb|robots.txt| for “interesting” information ;)
- Guessing subdomains for recursive inspection
Nessus/OpenVAS
Nessus

Nessus started in 1998, to provide a free remote security scanner. It is capable of scanning for:
- Vulnerabilities that could be exploited by an attacker to intrude the system
- Bad configurations in system services (software versions, etc)
- Default passwords, even calling external tools to launch dictionary attacks.
- Denial of Service (DoS) vulnerabilities
- Custom reporting
If you’re interested in Nessus usage, you may take a look at our tutorial on Pentesting using Nessus.
OpenVAS, a Nessus fork
In 2005, however, the company that was co-founded by the creator of Nessus, decided to change from an Open Source license to a proprietary (closed source) business model. In response to this, some of its contributors began forking the project.
From the many forks that spawned, the most resilient one is the Open Vulnerability Assessment System, (OpenVAS for short). Since 2008, it’s been maintained by the German company Greenbone Networks GmbH.

OpenVAS carries the functionality from Nessus, but also includes additional features; such as Risk Management.
Feel free to also check our comparison between Nessus vs OpenVAS.
Lynis
Lynis is an Open Source security testing and auditing tool for Unix-based systems; such as Linux, macOS, the BSDs, etc. It is aimed for developers, systems administrators, auditors and penetration testers alike.
The main difference between other tools, such as Nessus or OpenVAS, and Lynis is that the former perform scans of either entire networks, or network-attached hosts. On the other hand, Lynis runs all vulnerability scans while running on the host itself.
This is key since Lynis is able to locate possible configuration flaws, even if they’re related to kernel parameters that need to be hardened. On top of that, once the report is displayed, it will include links to the related Lynis test (control).
Some of the benefits cited on their website is that it is much faster, lower risk of disrupting business services, and the added scanning depth from being host-based. Plus, if you download the portable version, you can run Lynis without installing.
Conclusion
You can probably tell by now, there are some tools that work for one context, but not for the
others. This is why you need to know about these tools, in order to make informed decisions. As the old saying goes:
If all you have is a hammer, everything looks like a nail.

Leave a Reply